How to configure Okta as an SSO method for inSync authentication?
Overview
This article explains the steps that inSync administrators need to perform in order to configure Okta as an SSO method for inSync user and administrator authentication. Once done, inSync users will be redirected to the webpage of Okta for authentication.
Configure Okta as SSO method
Prerequisites: You need to have SSO token handy before you begin this procedure. The steps to generate SSO token are available in the Configure SSO on inSync On-Premise admin console procedure in this section.
- Log in to Okta Admin Console
- Click Applications.
- Click Add Application.
- On the next screen, select Create New App.
- Use the Sign on Method as SAML 2.0.
- Enter App name as Druva On-Premise.
- Click Next.

- Enter the details specified in the table on SAML settings:
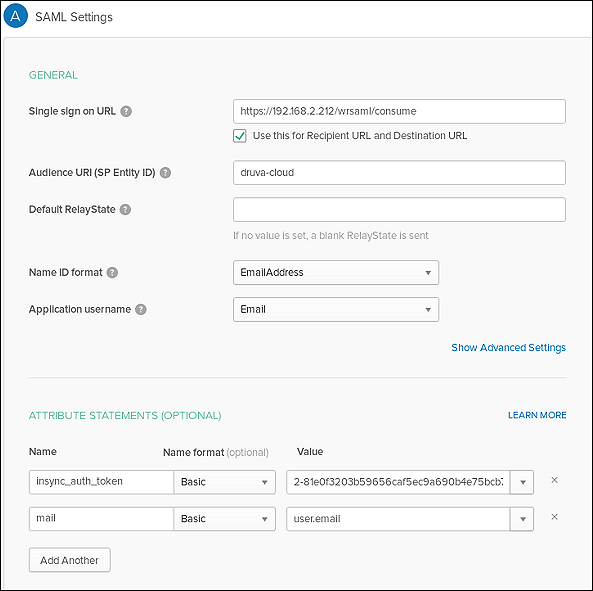
Field name Value Single Sign On URL
https://<IP/FQDN of inSync Server>/wrsaml/consume
Audience URL (SP Entity ID)
druva-cloud
Default Relay State
Leave this field blank
Name ID Format
Email Address
Application Username
Email
- Configure following values in the respective fields under ATTRIBUTE STATEMENTS (OPTIONAL).
Name
Name format (optional)
Value
insync_auth_token
Basic
<Single Sign on token from Console>
Enclose the authentication token in double quotation ("") marks, such as "X-XXXXX-XXXX-S-A-M-P-L-E+TXOXKXEXNX=" .mail
Basic
user.email
Leave the Group Attribute Statements as blank.
- Click Next
- On the third tab, select I’m a software vendor. I’d like to integrate my app with Okta.
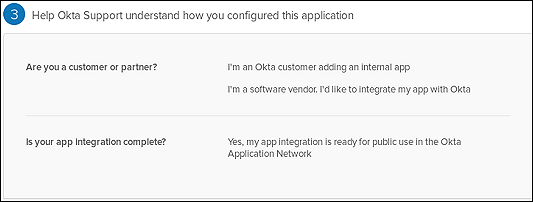
- Click Finish.
- On the next Settings tab, click View Setup Instructions.
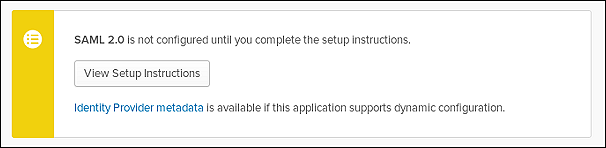
- From the Setup Instructions tab, copy the following. Keep these values handy when you perform the configuration on inSync Management Console.
- Identity Provider Single Sign-on URL
- IdP Metadata to your SP provider
- Map Okta users to this Druva On-Premises application using following steps:
- Open Druva On-Premise application.
- Click People & choose Assign to People.
- Select the user for whom you want to allow SSO authentication.
Configuration of Okta as SSO method is now complete.
SSO configuration on inSync On-Premise Management Console
You need to configure Druva On-Premise Console to use SSO feature.
Prerequisites: Keep the Identity Provider Single Sign-on URL and iDP Metadata to your SP provider copied in earlier procedure handy before you begin this configuration.
- Login to inSync Management Console
- Click
 > Settings
> Settings - Select Single Sign On tab.
- Generate the SSO token. You need to provide this token value to iDP under the attributes section.
- Click Edit.
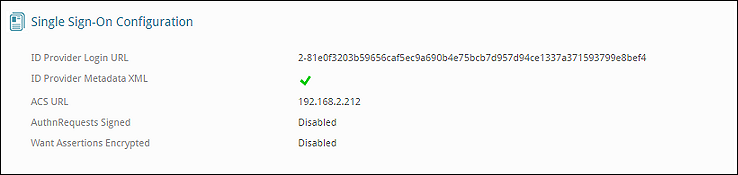
- Enter the ID Provider Login URL and ID Provider Metadata XML obtained during Okta configuration.
- Enter IP address or FQDN of your inSync Mangement Server as ACL URL.
- Ensure AuthnRequests Signed and Want Assertions Encrypted are disabled.
Your SSO configuration is now complete and appears as below:
Enable SSO authentication for users
SSO authentication must be enabled for inSync users as the last step to enable the SSO benefit for the users.
- On inSync Management Console, click Profile.
- Click the profile for which you want to enable SSO.
- Select Backup Policies and click Edit on under Retention and Access Policies.
- Set Log-in Using option to Single Sign On. Repeat these steps for every profile for which you want to enable SSO authentication.

SSO is now enabled for all users assigned with this profile. inSync users can now use SSO for:
- Accessing inSync User Web Console
- Activating a new device
- Reactivating existing device
Note: SSO cannot be used for Integrated Mass Deployment.

