Configure Azure AD Conditional Access to exclude inSync
If your organization uses Azure AD with Conditional Access for authenticating and providing access to users, as an inSync administrator ensure -
- Druva inSync IP address range is defined as a Named Location in Conditional Access.
- The Named Location is part of the Conditional Access Policy Exclusion list.
It is mandatory to ensure the above conditions, else Druva inSync fails to backup & restore Microsoft 365 data of all users and administrators.
Pre-requisites
- You must be an Azure AD administrator with Conditional Access administrator privileges.
- Get the IP Address range in CIDR notation for inSync Cloud by raising a case with Druva Support.
Procedure
- Login to Azure Portal.
- Configure or define a Named Location.
- Go to Azure Active Directory > Protect & Secure > Conditional Access > Named locations.
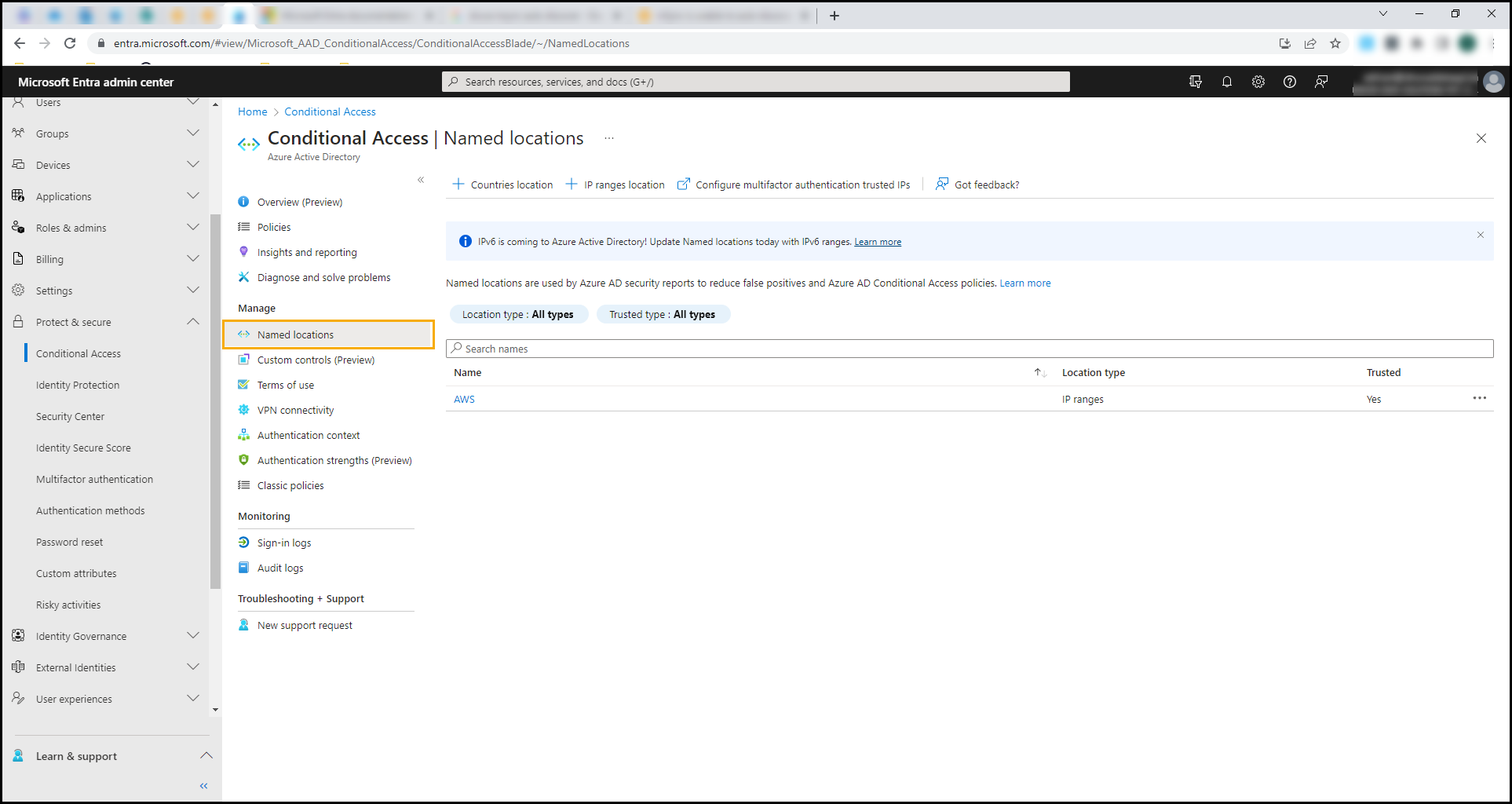
- Click to add IP Ranges Location.
- Provide a Name and the IP range.
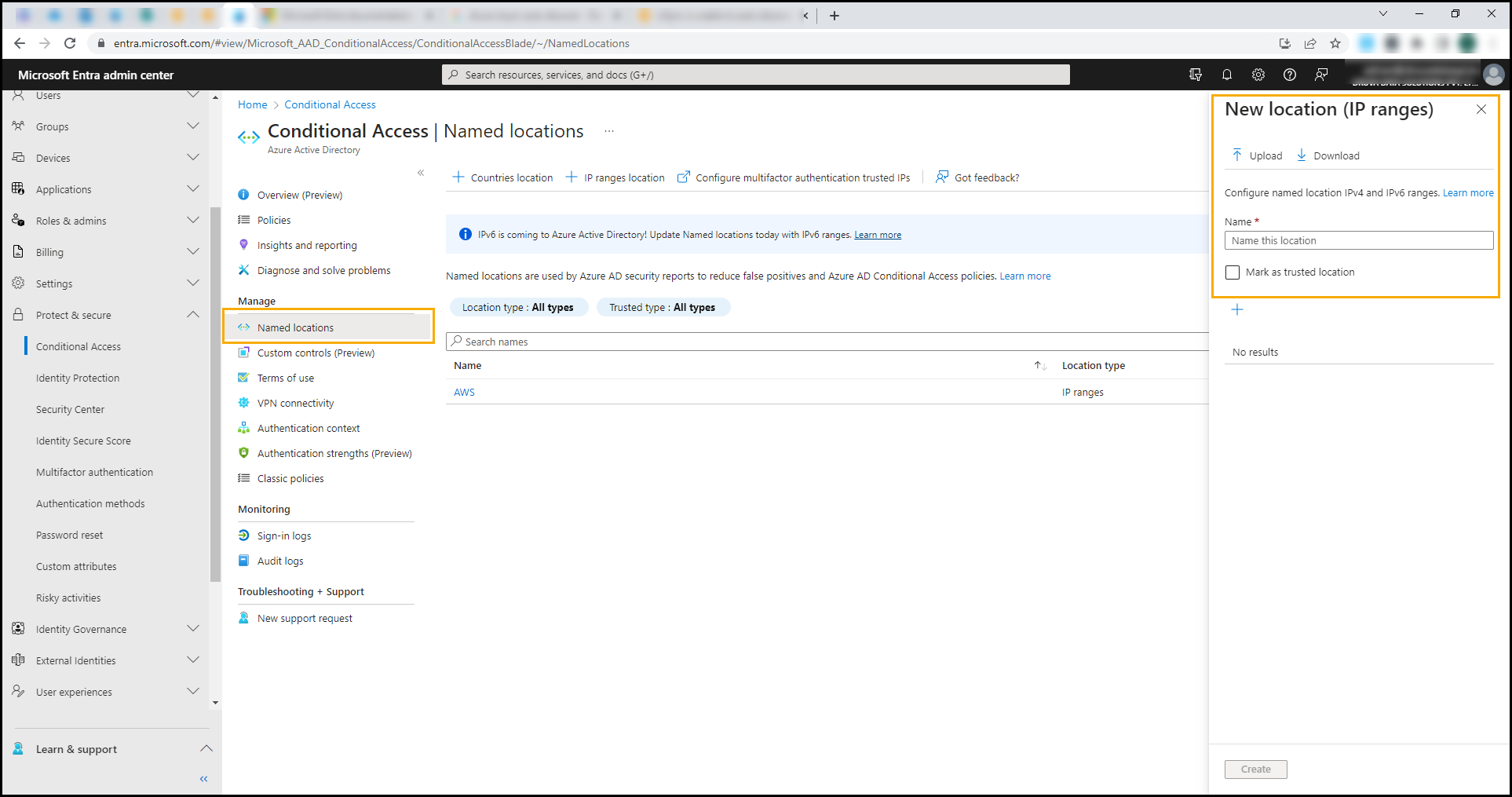
- (Optional) Select Mark as Trusted Location.
For more information, see Using the condition location in a Conditional Access Policy.
- Go to Azure Active Directory > Protect & Secure > Conditional Access > Named locations.
- After creating the Named Location, ensure you exclude this Named Location in the Conditional Access Policy's Location list. For more information, see Conditional Access: Condition Location.
- Go to Azure Active Directory > Security > Conditional Access > {Select your Conditional Access Policy}.
- Click on Conditions > Locations.
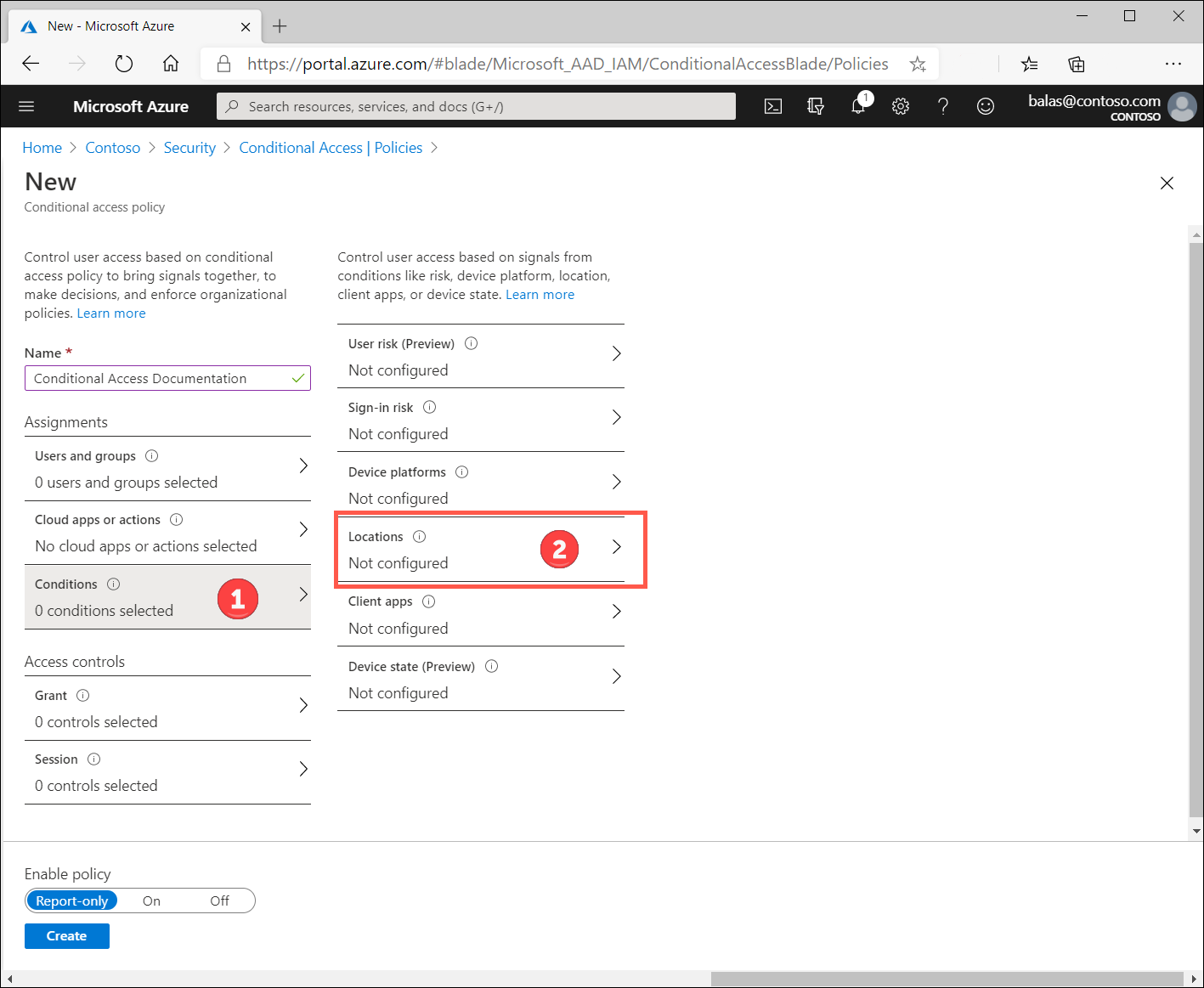
- Select the Exclude tab and then click Selected Locations.
- Select the Named Location that you created in Step 2 from the right-hand side panel.
- Click Save.
inSync users and administrators now logging on using MFA and with Conditional Access will be backed up successfully. Users and administrators can even restore their data seamlessly.

