Support for Azure Active Directory (AD) Conditional Access policies
Overview
Druva validates the Conditional Access policies enabled for your Microsoft 365 tenant during the Microsoft 365 app configuration to authenticate and provide conditional access to users. For example, if a conditional access policy grants access to users from a specific location. In that case, the Microsoft 365 app configuration step will validate this requirement to allow or deny access to those resources.
For a list of supported policy settings, see Supported Conditional Access policy settings.
-
If you have configured Conditional Access policies for your Microsoft 365 tenant, the app authentication step will adhere to these policies during Microsoft 365 app configuration for data protection.
-
The app authentication step checks if token-based authentication can connect with the Microsoft 365 tenant.
-
If the conditions in the access policies are not satisfied, the token-based authentication fails with the following error message.
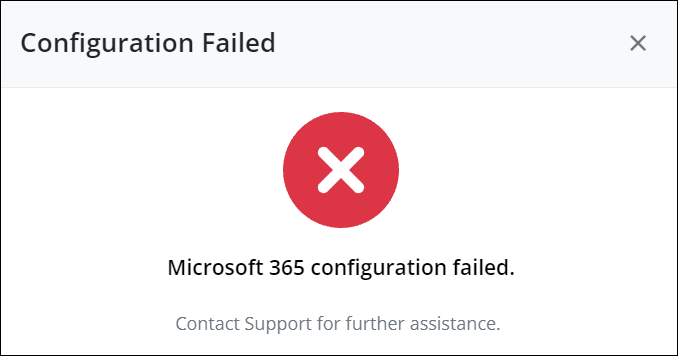
Let’s try to understand this workflow with an example.
Scenario: Conditional Access policy using Multi-factor Authentication (MFA)
Consider a scenario wherein you want to implement MFA for specific cloud applications in your organization. If you have defined a policy that requires all users to authenticate using MFA, then the Microsoft 365 app configuration for data protection adheres to this policy using the following workflow.
-
You have defined a Conditional Access policy with the MFA authentication setting for all users in the Azure admin portal.
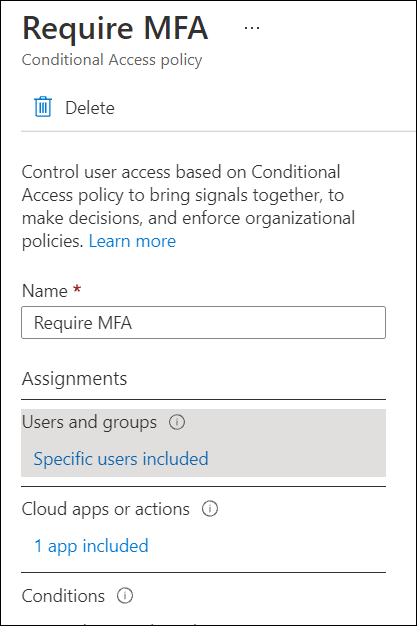
2. Configuration of Microsoft 365 app for data protection enforces this policy to implement an additional layer of security and authenticate the user using MFA.
3. The user must authenticate using the requested MFA method.
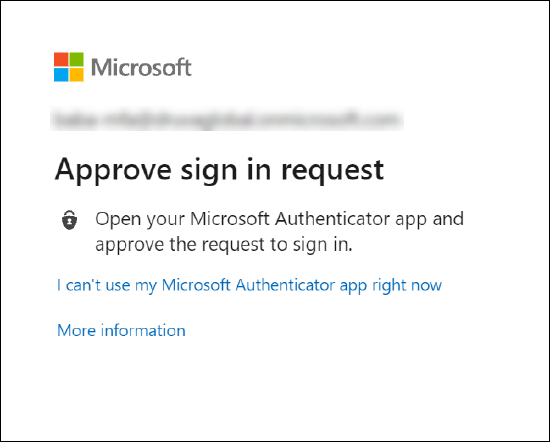
4. The user is allowed or denied access to the data protection services as per the MFA success or failure scenarios.

