Ports and communication protocols
 Business
Business  Enterprise
Enterprise  Elite
Elite
Druva communicates with your virtual infrastructure to backup and restore virtual machine data. This communication happens via ports and communication protocols that are secure for communication and transition of data.
Druva uses a combination of Transport Layer Security (TLS) and Secure Socket Layer (SSL) protocols for establishing a connection and initiating communication between Druva components and your virtual infrastructure components such as vCenter Server, ESXi hosts, and virtual machines.
The following diagram depicts the ports and communication protocols that are used by Druva for secure connection and communication during the backup and restore operations.
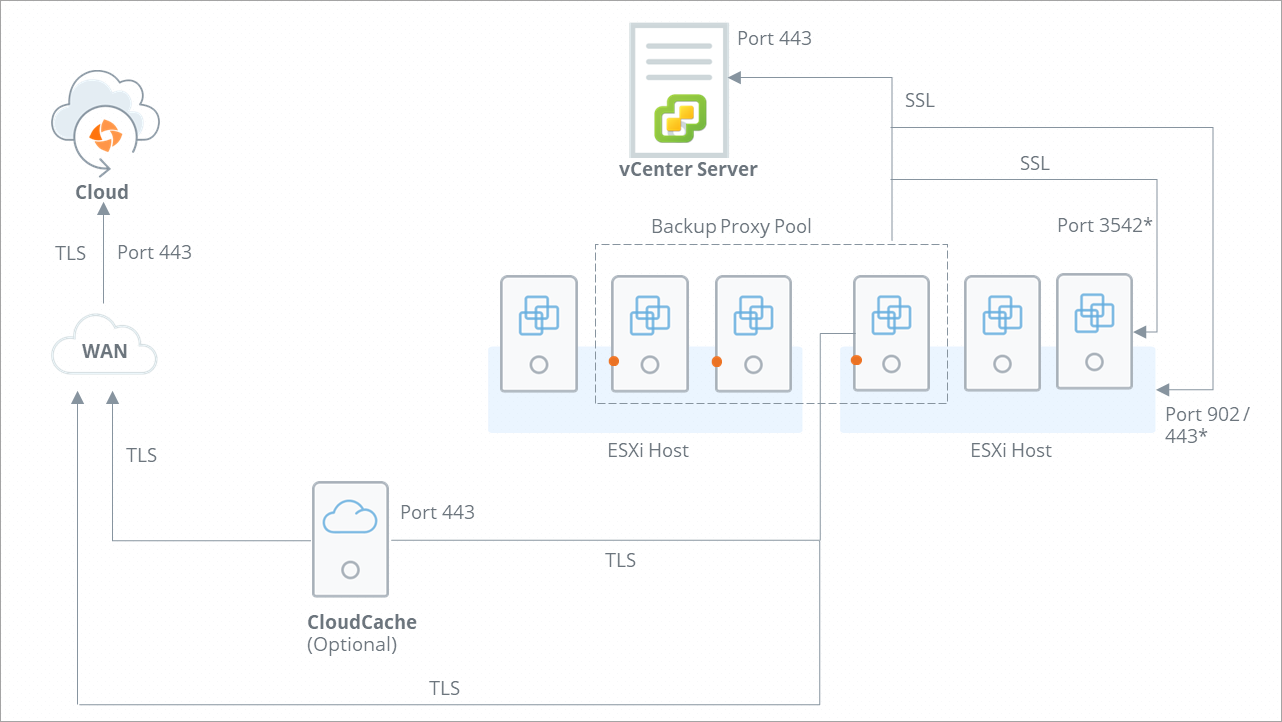
The following table describes the port and communication protocols used for communication between Druva and various VMware components.
Note: Communication happens from a backup proxy to other parties on various ports. Here, the backup proxy is the communication initiator, which is unidirectional. These ports are used for outgoing (unidirectional) communication, not incoming communication. However, data in the form of a response can flow in the opposite direction. Standard system ports such as 22 (SSH) and 2049 (NFS-SERVER) are used for incoming requests.
|
Port |
Communication Protocol |
Description |
|---|---|---|
|
443 |
HTTPS+SSL |
Druva uses Port 443 to establish a secure connection and communication between the following:
Note: Backup proxy establishes connection with ESXi host over Port 443 only if it registered with Druva as Standalone ESXi. If the ESXi host is registered with Druva through vCenter Server, backup proxy communicates with the ESXi host over Port 902. |
|
902 |
TCP/UDP |
Druva uses port 902 to establish a connection between the backup proxy and ESXi host registered with Druva through vCenter Server. Note: By default, VMware uses the port 902 for the vixDiskLib connection (All Transport Modes). You must use the VixDiskLib to access a virtual disk. All operations require a VixDiskLib connection to access virtual disk data. |
| 3542 | HTTPS+SSL | For application-aware backups, the backup proxy uses VMware Tools to inject two executables and a few supporting files such as certificates into the guest OS of the virtual machine. When the executables run, they start guest OS processes called guestossvc and PhoenixSQLGuestPlugin. The backup proxy uses the opened port 3542 on the guest OS so that it can communicate with guestossvc to run SQL Server backups. Ensure that this port is open on the guest OS. The backup proxy also uses this port to restore databases to the virtual machine. |
| 3545 | HTTPS+SSL | For application-aware backups, the SQL executable service PhoenixSQLGuestPlugin queries the Microsoft VSS APIs to back up and restore SQL Server databases. The guestossvc service interacts with the PhoenixSQLGuestPlugin service using this port. The PhoenixSQLGuestPlugin service cannot directly communicate with the backup proxy. |
|
3389/22
|
TCP/UDP |
During the backup cycle, the backup proxy sends network packets to Windows virtual machines (where VMware tools are installed) on port 3389 to identify if the RDP port is open or not. For Linux virtual machines, the port is 22, which is used for SSH. This is used for Disaster Recovery or DR restores. |
| 123 | UDP | Backup proxy accesses NTP server on Port 123 (UDP) for time synchronization. |
|
443 |
HTTPS+TLS |
Druva uses TLS 2.0 or a secure connection that happens between the following:
|
Firewall rules for protection of Enterprise Workloads
For more information, see article.

