How to create or update the CloudFormation stack
Overview
This article provides the steps to recreate or update the CloudFormation stack if it has been incorrectly updated, removed, or deleted, either inadvertently or deliberately.
The CloudFormation template creates various resources in your AWS account and must be executed by a user with the following permissions:
IAM create role/policy
s3 create bucket
IAM create instance profile
SNS publish
Update CloudFormation stack
Update the CloudFormation stack from the AWS console as follows:
- Log into the CloudRanger console, and navigate to your Account Settings.
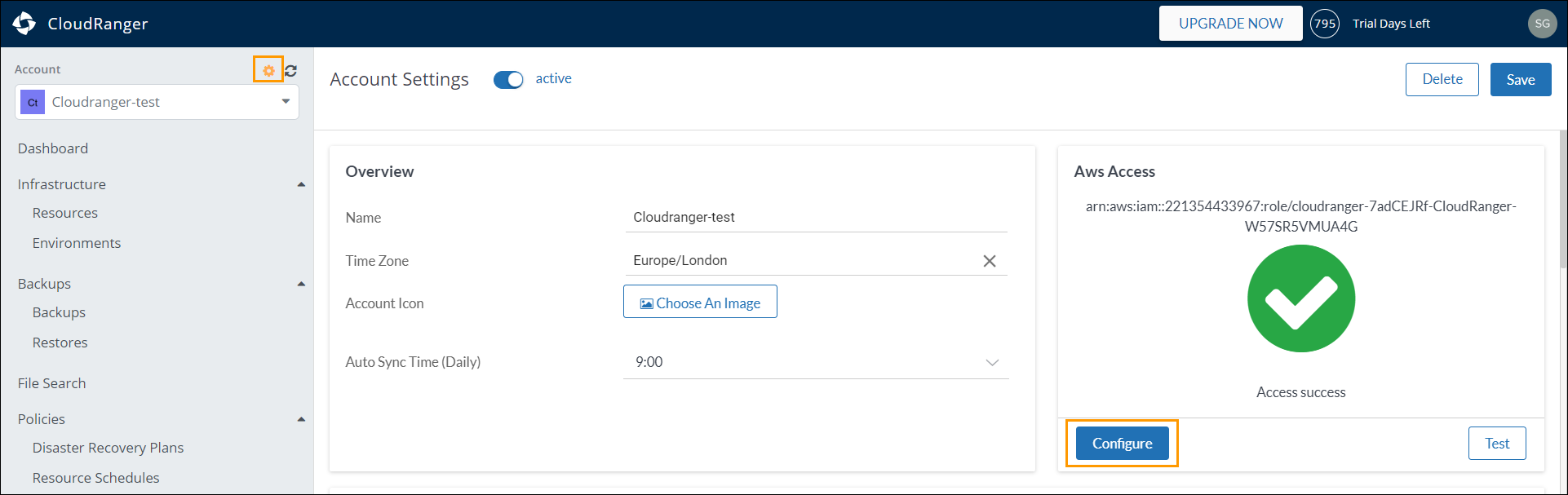
- Under AWS Access section click Configure, and copy the CloudFormation URL.
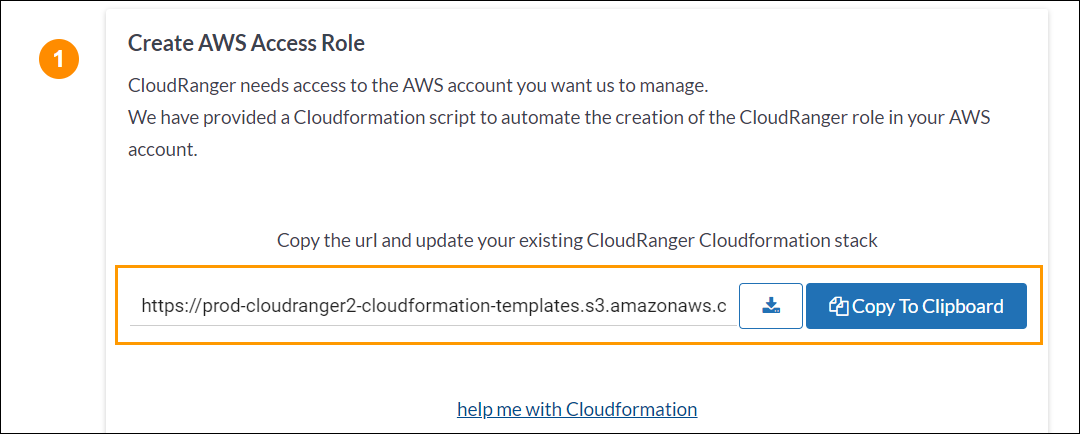
For step-by-step instructions on CloudFormation, you may click help me with Cloudformation.
- Login to your AWS Console and navigate to the CloudFormation page.
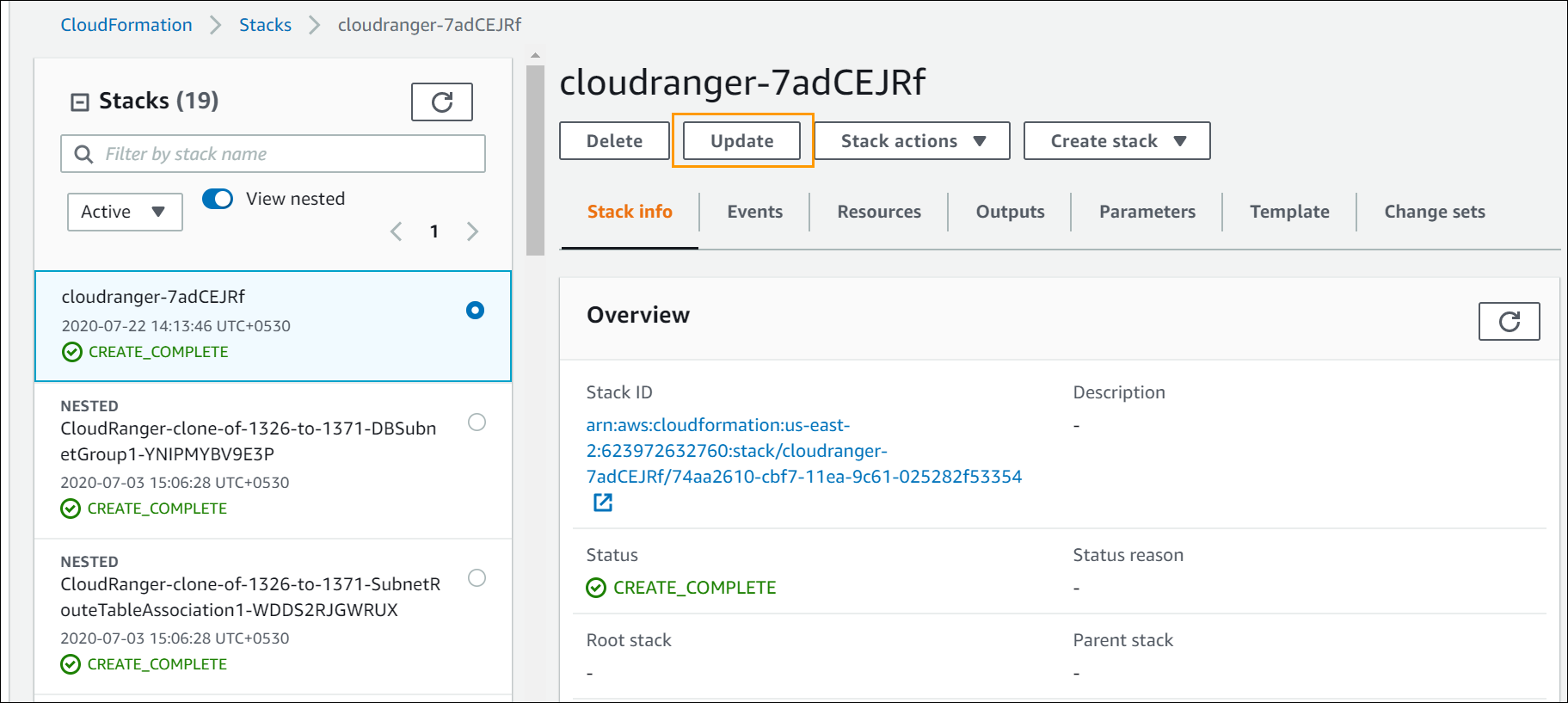
- Select the stack that you previously created when configuring CloudRanger, and then click Update.
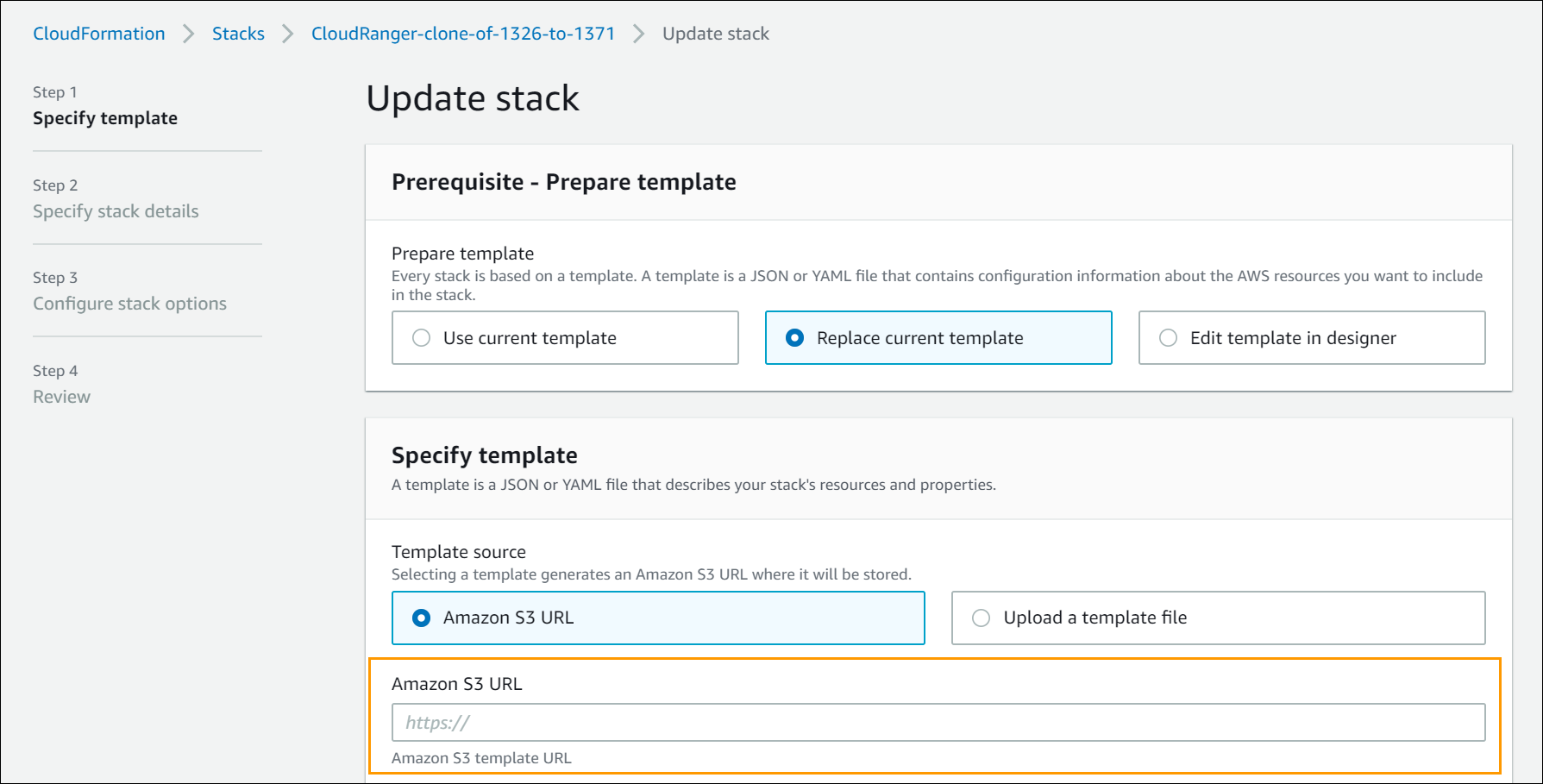
- On the Specify template page, select Replace current template. Then paste the CloudFormation URL into the Amazon S3 URL text box. Click Next.
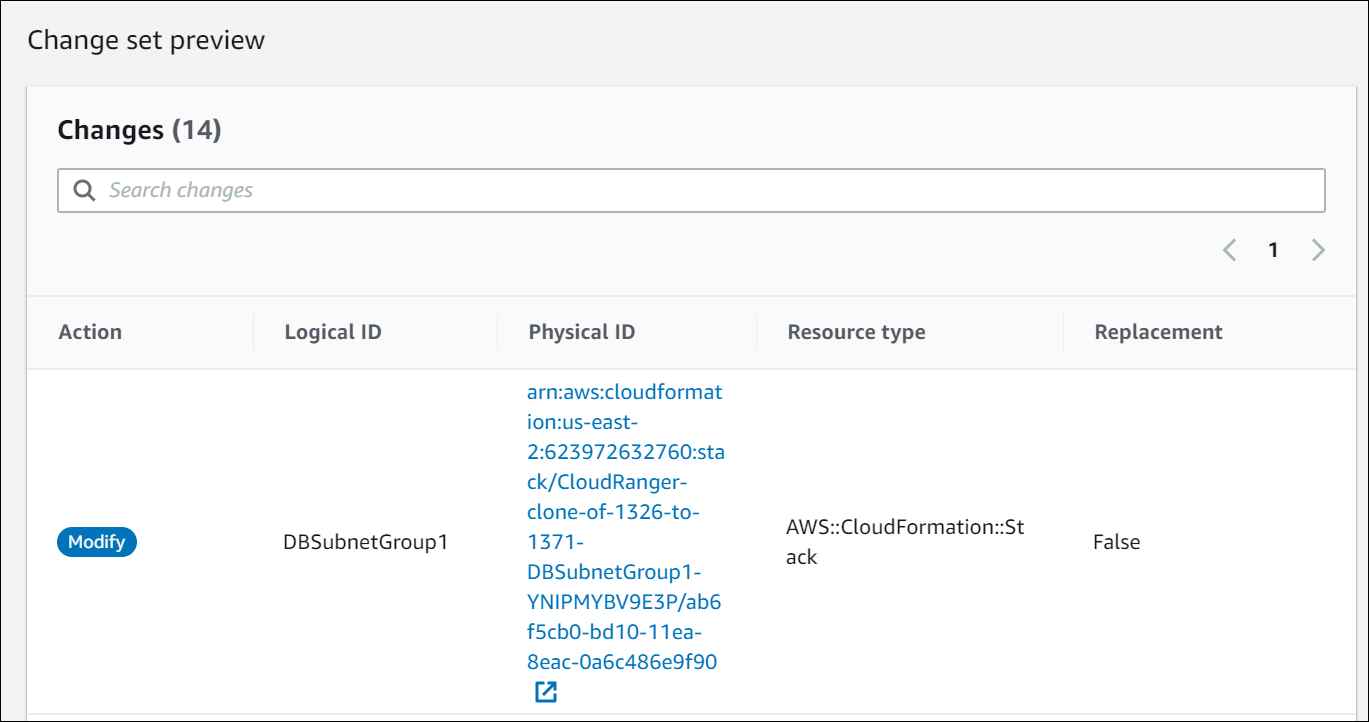
- Click Next on the Specify stack details and Configure stack options pages.
You will be able to preview the changes before you click Update stack to confirm the CloudFormation changes to resources.
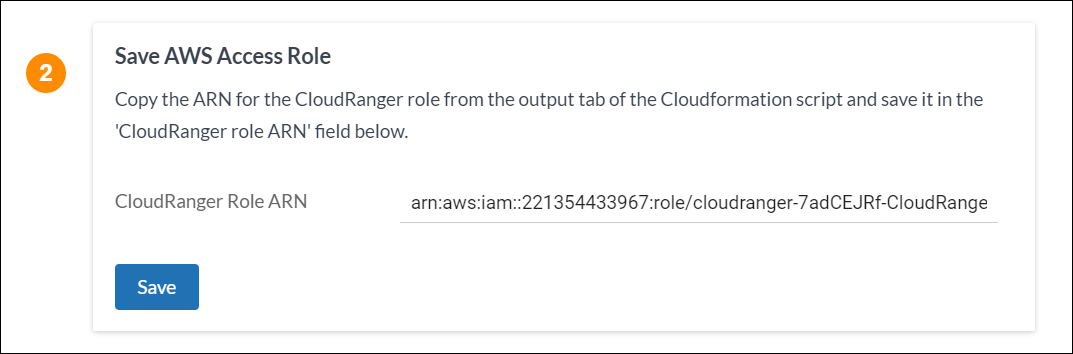
- Once the stack update is complete, navigate back to CloudRanger and click Save under Save AWS Access Role.
Your IAM role and AWS account access should now be updated with the latest permissions, allowing you to take advantage of any new functionality that is released.
Troubleshooting
This section provides the troubleshooting steps for any unexpected issues that may cause failure in the CloudFormation stack:
Create_Failed - AWS:S3:Bucket
Create_Failed - AWS:IAM:ManagedPolicy
Create_Failed - CRFileLevelSearchBucket
ROLLBACK_IN_PROGRESS - CloudRanger-Access
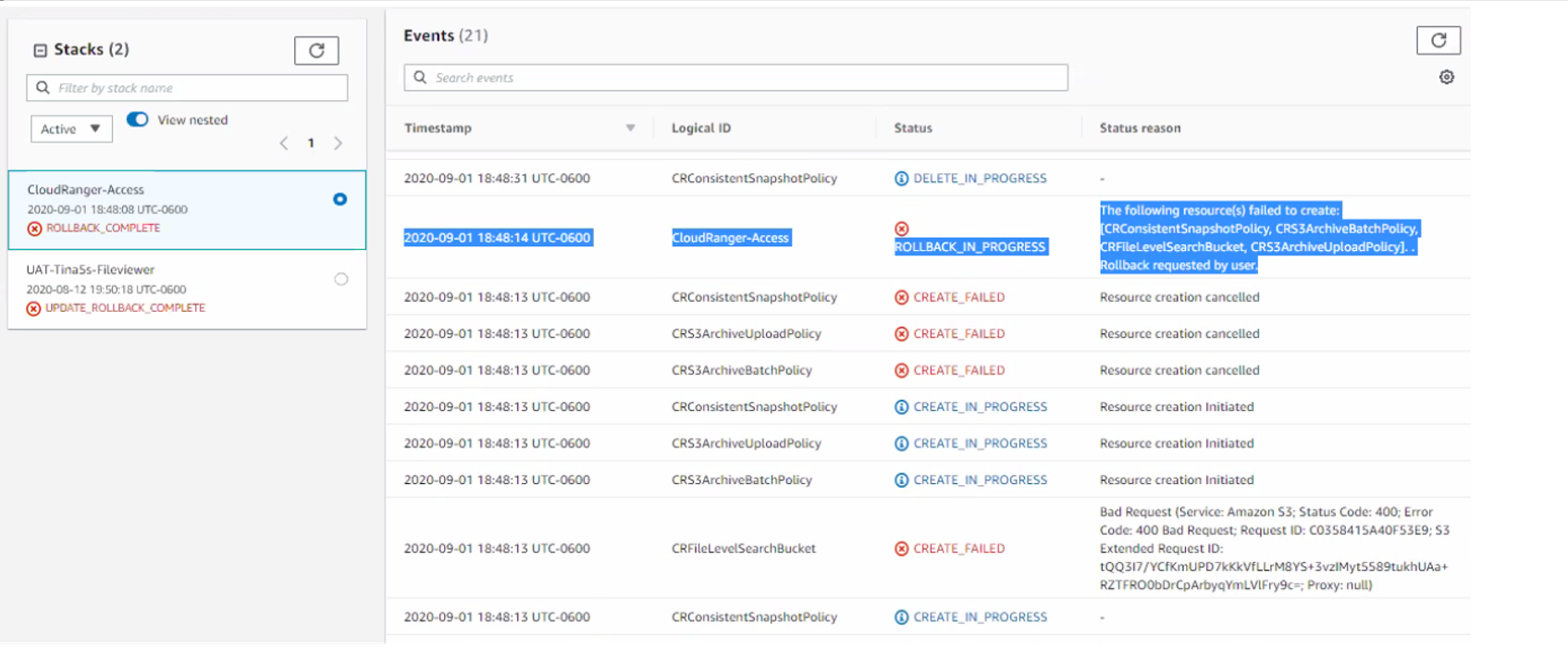
Causes
- The CF stack has S3 bucket already associated with it (created by old CF stack).
- The CF stack has IAM Policy associated with it, which was created by an old CF stack (which has been deleted).
Resolution
Perform the following preliminary steps before deleting the concerned IAM Policy and S3 bucket associated with it:
- If the S3 bucket is empty, delete it.
- If S3 storage has data, copy the data to another temporary bucket as follows:
- Create a new temporary bucket.
- Copy the data from the S3 bucket to the temporary bucket.
- Delete the S3 bucket.
- Again run the CF script. This again creates a new S3 bucket.
- Copy the data from the temp bucket into the newly created S3 bucket.

