Compliance violations for end users
Overview
You can enable inSync end users to view and take action on violations reported for the data stored in their system. This is helpful when the Data Compliance team is small, and a huge number of violations are reported because of the nature of data stored in the data sources.
A good example of this is the mock data that a financial company uses to test the software that they are developing. Test data often contains mock sensitive information such as account numbers and credit card numbers. inSync might report a violation for the information stored in the test data. The user can easily identify that these violations are harmless as they are reported for mock data and then resolve the violations without administrator intervention. Administrators no longer need to wade through unimportant violations and can focus on critical violations.
As an administrator, you can configure the entire workflow of how a violation moves through various phases, right from detection to resolution. You have complete control over the entire process flow which ensures that there are no gaps or critical misses.
Workflow of a violation with end user violation visibility enabled
You can enable inSync client users to see violations per policy. The following workflow diagram shows how a file violation moves through different stages when End user violation visibility is enabled.
Notes:
C means that the option is Configurable.
The flow for email violations is the same. The only exception is the False Positive resolution as it is not applicable for emails.
- The diagram also takes into consideration that all the default options are enabled for End User Violation Visibility.
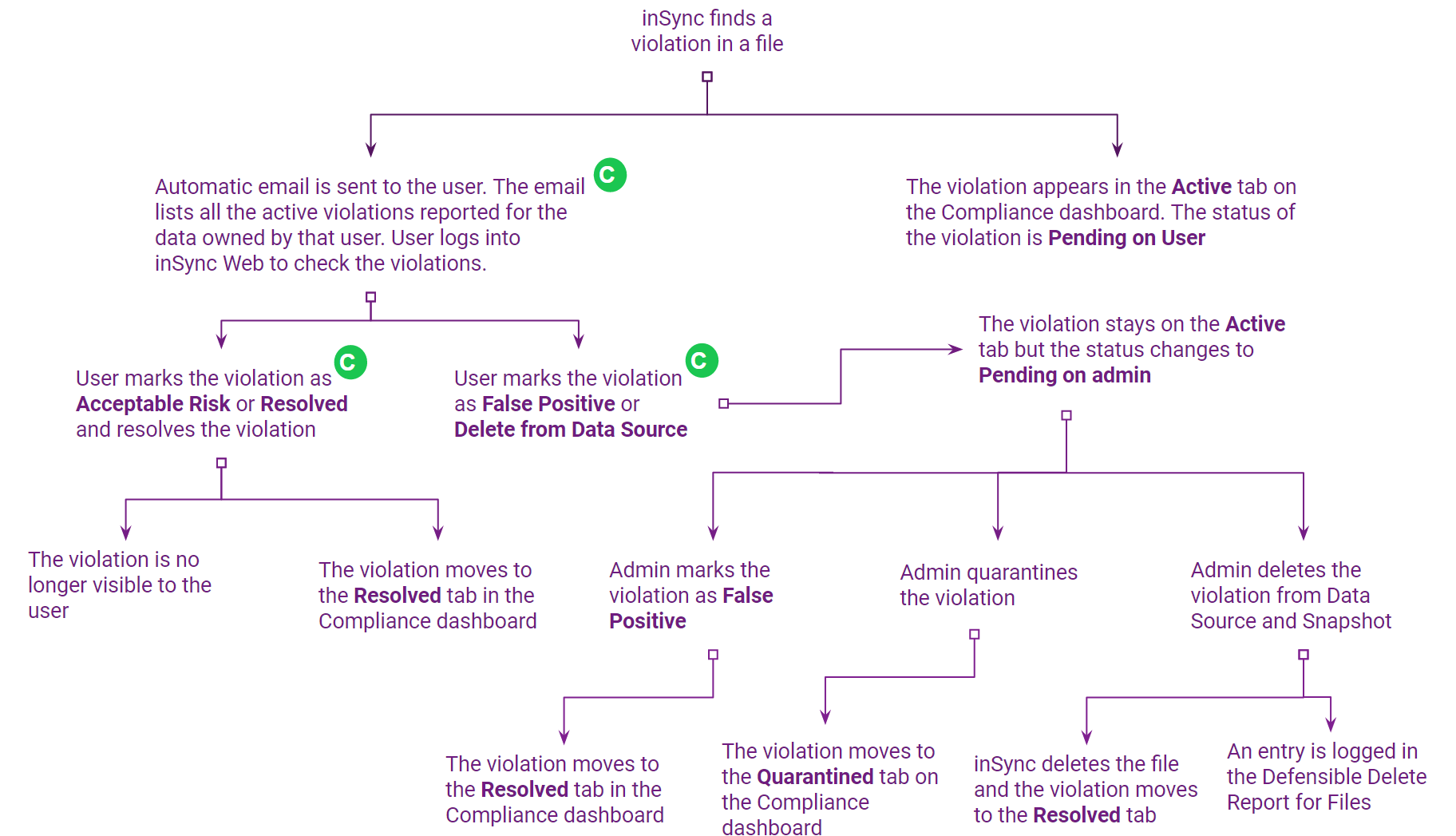
The following is the sequence of events that are triggered when inSync finds a violation for a policy that has end user violation visibility criteria enabled.
-
inSync scans the backed-up data for violations as per the details defined in the Compliance Policy.
-
The user receives an email notification about the violations reported for the data owned by the user.
The file violations are also displayed on the Active tab, in the Sensitive Data Governance Dashboard - File Violation page. The status of such a violation is Pending on User. The process is the same for Email violations. -
The user logs in to inSync Web using the link in the email to view details of the violations.
-
The user resolves the violations using the available options. The resolution options visible to the end user depend on the resolution types available for end users.
-
Depending on the resolution option selected by the user, the violation ends up either in the Active tab or in the Resolved tab on the Sensitive Data Governance Dashboard. If no one takes any action, the violation will be auto-resolved as per the defined criteria in Compliance settings. For more information, see Modify Compliance Settings.
All the activities of the administrator and the end user are logged in Admin Audit Trail and User Audit trail respectively. The details are also available in the Non-Compliant File report and Non-Compliant Email report.
Settings related to end user violation visibility
When you enable End user violation visibility for a policy, the default configured settings are auto-applied. If you want, you can configure these settings before you enable end users to view violations. The following settings are available:
-
Define the notification frequency for the violation summary email that is sent to end users. Learn more.
-
Violations visibility criteria applicable for end-users. Learn more.
-
Configure the resolution statuses that will be available to end users. Learn more.

