Configure Multifactor Authentication
Multifactor Authentication allows you to verify the administrator's identity by combining two authentication steps. It provides an additional layer of security when administrators access their accounts from any device and ensures that only authorized access is permitted.
At every login, the administrators across your organization must enter a One Time Password (OTP) and their login password.
Note: Multifactor authentication is not required if you have configured SSO. It is applicable only for password logins, including failsafe administrators.
Supported Multifactor Authentication Methods
Starting April 13, 2023, Druva will no longer support Email-based Multifactor Authentication. If you have not updated your multifactor authentication method, the Authenticator App-based Authentication method is configured by default for your Druva Console login.
|
Method |
Public Cloud |
Enterprise Workloads GovCloud |
inSync GovCloud |
|---|---|---|---|
|
Authenticator App (Default) The OTP is sent to the administrator's Authenticator app.
|
Yes |
Yes |
Yes |
|
SMS The OTP is sent to the administrator's registered mobile number. |
Yes |
No |
No |
Prerequisites
- Only a Druva Cloud Administrator can update the Multifactor Authentication for an organization.
- SMS-based Multifactor Authentication is not supported for Cuba, Iran, North Korea, Syria, and Sudan.
Update Multifactor Authentication for your organization
Note: Authenticator App-based Authentication method is configured. by default.
-
Go to the Global Navigation Panel > Druva Cloud Settings > Access Settings.
-
In the Multifactor Authentication section, click Change.
-
Select an authentication method.
-
Authenticator App-based Authentication configuration steps
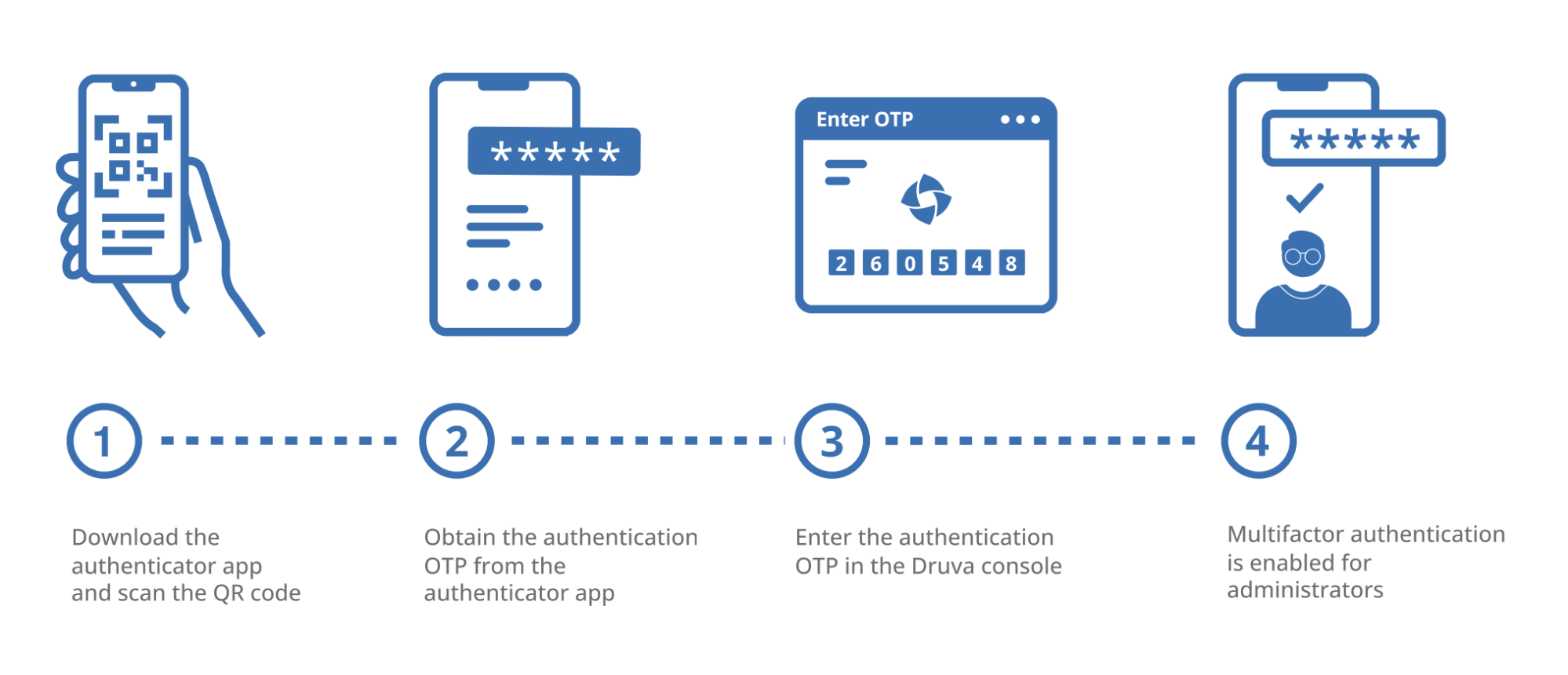
-
SMS-based Authentication configuration steps
-
Upon successful authentication, the authentication method is updated for your organization. All the administrators across your organization are notified with an email about the activation.
-
For SMS-based Authentication:
At every next login, the administrators are required to authenticate themselves using the OTP they receive on their mobile devices. -
For Authenticator App-based Authentication:
At the first login, the administrator needs to link to the authenticator app by scanning or entering a QR code in the authenticator app.
At every next login, the administrators are required to authenticate themselves using the OTP they receive via the authenticator app.
-
-
After successful configuration, note the numeric code or download the QR code PDF file for future reference if you need to change your phone or app.
Note:
Ensure that the Date & Time on the mobile device is correct and the Automatic time and date and Automatic time zone are turned on. If the Date and Time on the mobile device are incorrect, Druva will not accept the MFA codes.
Along with this, you may also want to perform time correction on the authenticator app itself. The option may be placed at different locations (generally under settings) within the Authenticator app. For example, see Google Authenticator and Microsoft Authenticator.
Reset the Multifactor Authentication of another administrator
In case, you have lost or forgotten your mobile device, or if your account is compromised, you can ask the Druva Cloud administrator to reset your Multifactor Authentication.
- In the left navigation, click Manage Administrators.
- Click on the administrator name whose authentication you want to reset.
- Click on the menu button next to Edit and click Reset Multifactor Authentication.
- In the confirmation dialog, click Continue.
- Authenticator App reset: For the first login after reset, reconfigure your App with your Druva account using the QR code displayed.
- SMS reset: For the first login after reset, register your mobile number with your Druva account.
Frequently asked questions
After this update, when Druva configures my account to use Authenticator App-based Authentication, can I change it later?
You can change the Multifactor Authentication anytime. Refer to the product documentation.
What happens if I am using an email alias for login?
After this update, email aliases will not be supported. You will need unique login credentials and separate devices for each administrator to log in.
Is Multifactor Authentication required for Druva products accessed via Single Sign-on (SSO)?
No. Multifactor Authentication is not required with Single-Sign on.
How can other administrators in my organization login into the Druva Console after Multifactor Authentication is enabled?
After enabling multifactor authentication,
- Enter your Email Address and Password, then click Sign In.
- Configure the Authenticator App-based Authentication: Link to the authenticator app by scanning or entering a QR code in the authenticator app.
At the first login, the administrator needs to link to the authenticator app by scanning or entering a QR code in the authenticator app.
At every next login, the administrators are required to authenticate themselves using the OTP they receive via the authenticator app.
What should I do if I change my mobile device or the authenticator app?
You can ask another DCP administrator to reset the Multifactor Authentication.
What if an administrator doesn't receive OTP?
You can contact support.
Will this change impact me even if I have configured SSO?
No. This change will not impact customers who have configured SSO. This change is applicable only for password logins, including failsafe administrators.

