Set up Single Sign-On (SSO) with Managed Services Center
Overview
Single Sign-On (SSO) can provide you seamless access to various services using a single action of authentication and authorization. Druva supports SSO for Managed Services Providers (MSP) to access Managed Services Center (MSC) without the need for a separate login. An SSO login validates usernames and passwords against your corporate user database, typically managed by your Identity Provider (IdP). MSPs can use IdPs such as Okta and Azure to authenticate and authorize the user.
Druva categorizes IdP support levels as follows:
Certified IdPs
A certified IdP is fully tested by Druva Quality Assurance (QA) team. Druva certifies these IdPs and performs regular testing with every cloud release to ensure the SSO functionality works as expected.
- Azure AD
- Okta
Supported IdPs
A supported IdP is not tested by the Druva QA team with every cloud release, however, the SSO functionality should work as expected. Druva will provide support for such IdPs. Issues that require time and resources beyond commercial viability may not be addressed.
- SAML 2.0 supported IdP excluding certified IdPs
How SSO Works
When admin enables SSO, you can access the Managed Services Center directly through your IdPs. This IdP keeps the record of your credentials to authenticate your login and access to your authorized app.
Pre-requisites
To use SSO:
- Set up a corporate database with an Identity Provider (IdP) to include all administrators.
- Get IdP login URL and IdP certificate from your Identity Provider (IdP).
SSO Working Process
Let's look at an example of the SSO working process:
- Admins signing in to the Managed Services Center will be redirected to their IdP login page if SSO is configured and enabled.
- The identity provider verifies the administrator's identity, and if valid, asserts back to the Managed Services Center that the administrator should have access. After successful authentication, The IdP redirects the administrator to the Managed Services Center
- Administrators can now access the Managed Services Center without individual passwords.
- However, if the identity provider does not verify the administrator within its database, it asserts back to the Managed Services Center that the administrator is not authorised to access MSC. Upon receiving this response, the access to Managed Services Center is denied.
Generate SSO Token
To enable your IdP to recognize MSC sign-in requests, you must generate an SSO token and update your IdP configuration with that token. This token is a unique identifier that Managed Services Center uses for sign-in requests. When someone tries to sign in, Managed Services Center sends a request to the IdP using HTTP POST. The IdP attaches the SSO token to its response to indicate that the authentication request is valid.
Managed Services Center then checks the SSO token ID in the IdP's response to ensure it is authentic. The SSO token helps to ensure the security of sign-in requests by uniquely identifying them and allowing the IdP to verify their authenticity.
You can generate the token multiple times, but until you update the newly generated token in IdP, the previously generated token will be used to authenticate sign-in requests.
Procedure
- Sign in to Managed Services Center, and then go to Settings > Access Settings.
- In the Single Sign-on section, click the Generate SSO Token button.
- Copy the Token Generated, and then click Close.
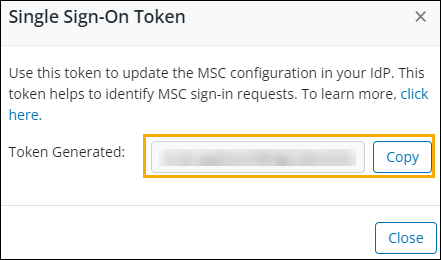
- Save the copied token as plain text using the text editor.
- Use this token in the next steps while configuring IdP with SSO.
Configure Identity Provider (IdP) For SSO
Pre-requisites:
- Get an SSO token from Managed Services Center.
This section explains how to integrate your Managed Services Center (MSC) with Identity Provider (IdP). From the given list, you can choose your preferred IdP that is supported in your organization and then integrate MSC and configure IdP for SSO.
Configure SSO Settings in Managed Services Center
Pre-requisites:
- You must configure your Identity Provider (IdP) to create a corporate database that contains the usernames and passwords of all administrators.
- Get the IdP URL and certificate from your Identity Provider (IdP).
If you are an MSP administrator, you can configure and edit SSO settings in Managed Services Center. While configuring it, you must provide IdP details you received after configuring your IdP for SSO.
Procedure
- Sign in to Managed Services Center.
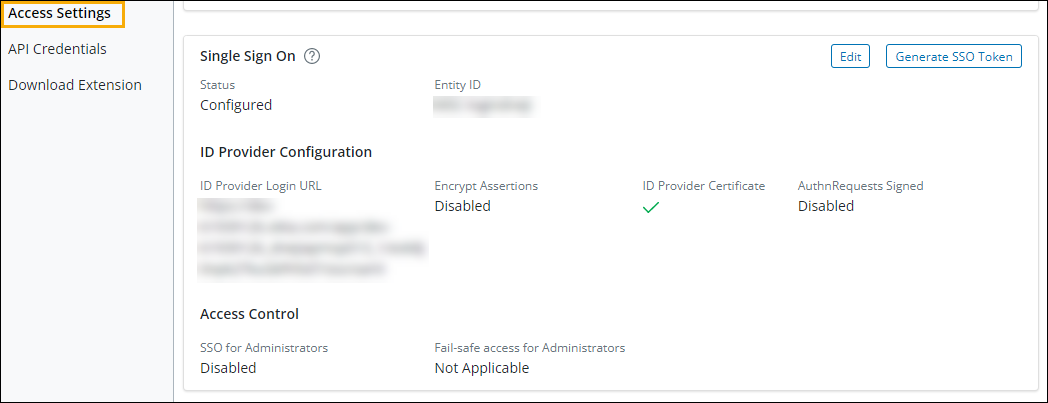
- Go to Settings > Access Settings.
- In the Single Sign-on section, click Configure SSO (if this is your first time configuring SSO) or click Edit to modify existing settings. This will open the Single Sign-on Settings window.
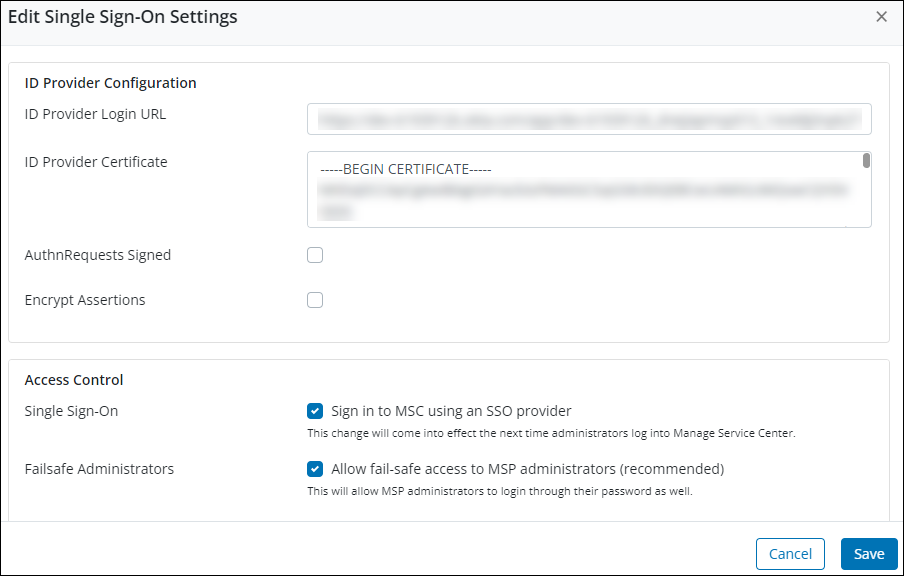
- Provide the appropriate information for each field.
Field Action ID Provider Configuration
ID Provider Login URLType the identity provider's URL. The URL that you provide in this field points to the identity provider's authentication page.
When the email is entered on the Managed Services Center login page, the administrator is directed to the identity provider's authentication page.
ID Provider Certificate Copy the content of the public key certificate that your IdP provided. This certificate ensures that the communication between MSC and your IdP is secure. AuthnRequests Signed (optional) Select this checkbox if you want to sign SAML Authentication Requests.
By default, SAML Authentication Requests are not signed.
Encrypt Assertions (optional) Select this checkbox if you want to enable encryption for the SAML assertions.
By default, encryption is disabled.
Access Control Single Sign-On Select the Sign in to MSC using an SSO provider checkbox to let administrators use the SSO configuration to sign in to Managed Services Center. Failsafe for Administrators Select the Failsafe for Administrators checkbox to provide MSP Administrators an option to use a password to sign in to Managed Services Center even if SSO is enabled for administrators.
Only MSP Administrators get the privilege to use a password to sign in to Managed Services Center.
By default, this setting is enabled, and it is recommended that you DO NOT disable this setting.
- Click Save.
Only MSP administrators can configure and manage SSO for Managed Services Center.
Enable SSO
After configuring the IdP details in Managed Services Center, you can enable Single Sign-On (SSO). This change will take effect during your next sign-in to Managed Services Center. Once SSO is enabled, all administrators can access Managed Services Center using their IdP credentials.
Procedure
- Sign in to Managed Services Center.
- Go to Settings > Access Settings.
- In the Single Sign-on section, click Configure SSO (if this is your first time configuring SSO) or click Edit to modify existing settings. This will open the Single Sign-on Settings window.
- In the Access Control section, select the Sign in to MSC using an SSO provider checkbox.
- Click Proceed, and then click Save to apply the changes.
- When the administrator enables SSO, the account recovery credentials are shared with all MSP administrators via email.
- These account recovery credentials are useful to recover your account if SSO stops working or all the MSP administrators forget their account password.
- Please keep these credentials safe and secure with you. In case all Administrators lose access to MSC, contact Druva Support to help with account recovery.
Failsafe Administrators
If you are an MSP administrator, you can enable SSO for other administrators' accounts including yours.
After enabling SSO,
- If the Failsafe option is disabled, the use of a password to sign in will be disabled for all administrators.
- If the Failsafe option is enabled, all the MSP Administrators can use both SSO and password login mechanisms to gain access to Managed Services Center. The use of a password to sign in will be disabled for all the Administrator roles, except for MSP Administrators.
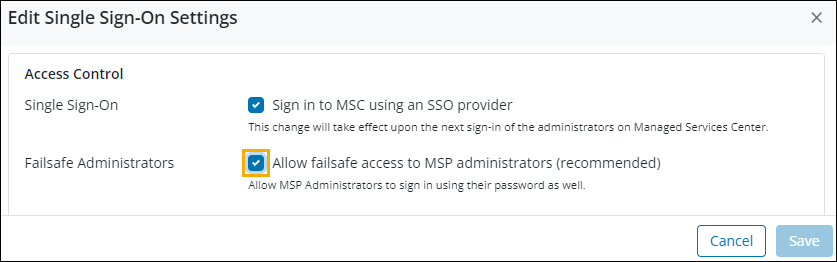
In SSO settings, access control for Failsafe administrators is by default enabled.
It is highly recommended to keep access control for failsafe administrators enabled.
Procedure
To disable failsafe access for MSP administrators
- Sign in to Managed Services Center.
- Go to Settings > Access Settings.
- In the Single Sign-on section, click Edit to modify existing settings. This will open the Single Sign-on Settings window.
- Check if SSO is enabled, if not, enable the SSO by selecting the Sign in to MSC using an SSO provider checkbox.
- De-select the allow failsafe access to MSP administrators checkbox in access control.
- Click the disable failsafe access button.
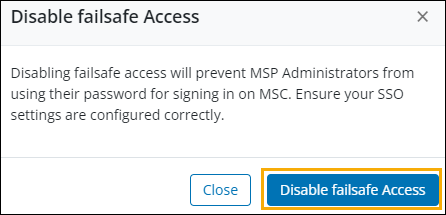
- Click save to apply the changes.
Disable SSO
MSP administrator can disable SSO. After disabling SSO, administrators can use their account password to sign in to Managed Services Center. If SSO is disabled, all administrators will receive a password reset link via email that they can use to reset their account password if necessary.
Procedure
- Sign in to Managed Services Center.
- Go to Settings > Access Settings.
- In the Single Sign-on section, click Configure SSO (if this is your first time configuring SSO) or click Edit to modify existing settings. This will open the Single Sign-on Settings window.
- In the Access Control section, de-select the Sign in to MSC using an SSO provider checkbox.
- Click Proceed, and then click Save to apply the changes.
If you have forgotten your account password, reset it using the link shared with you via email after disabling SSO.
Read more

