Release Notes
Our Cloud services are being updated in stages. If you do not see the updates mentioned here yet, they will be available in your region soon. To know more, see Druva Cloud Upgrade Process.
March 14, 2024
This release has minor bug fixes.
February 29, 2024
This release has minor bug fixes.
February 15, 2024
Enhancement
Introducing Audit Trails for Unusual Data Activity
You can now track and monitor the following Unusual Data Activity actions using the Audit Trails feature:
-
Unusual Data Activity - Alerts Ignored: Details of the alert ignored for an affected snapshot and the administrator who performed the action
-
Unusual Data Activity - Logs Downloaded - Details of the downloaded logs and the administrator who performed the download
-
Unusual Data Activity - Configuration Changed: Details of UDA settings updated, and the administrator who edited them
This feature helps to meet the data governance and compliance requirements by providing a chronological view of administrator activities performed for Unusual Data Activity.
- ►Here is a glimpse of the update
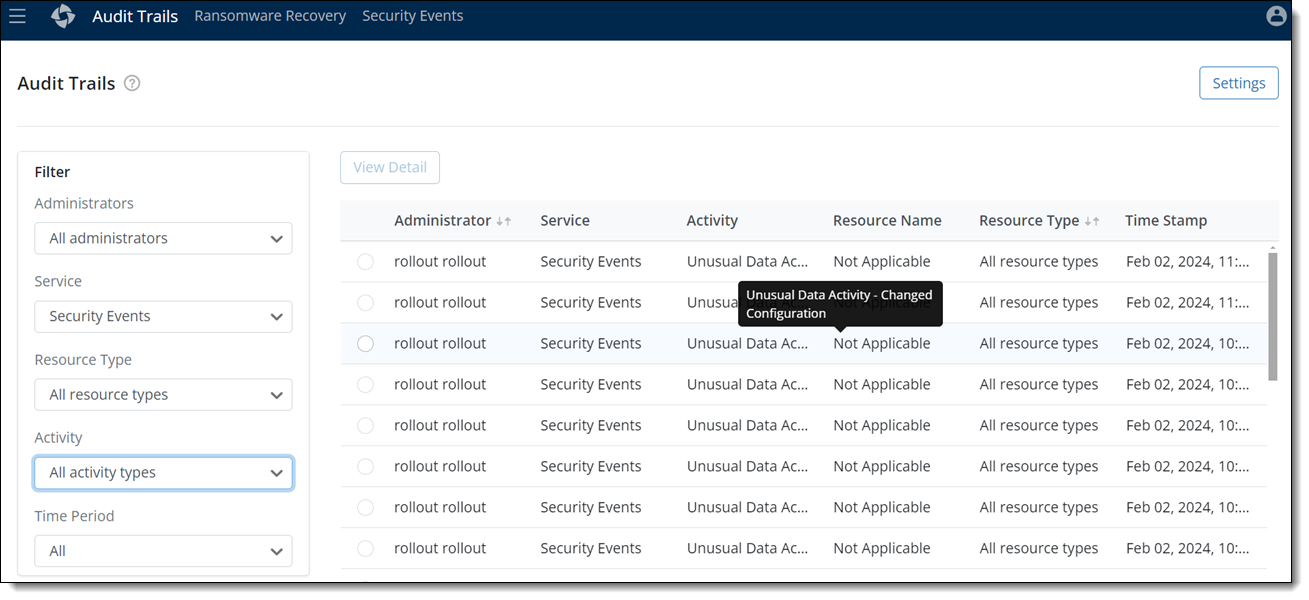
For more information, see About Audit Trails.
February 01, 2024
This release has minor bug fixes.
January 18, 2024
This release has minor bug fixes.
December 21, 2023
Enhancement
Introducing new UDA events for VMware resources
We are excited to bring in the following two new UDA events for VMware resources that help you with proactive error management in case of UDA failures and seamless functioning of Unusual Data Activity.
- Unusual Data Activity Scan Failure: A warning alert is generated and sent via email (if email subscription is enabled) when the UDA scan fails because the VMware prerequisites are not met. The alert also provides the exact reason for you to be able to take corrective action. You can access this alert from Security Events > Alerts. Alternatively, you can also access it via the Events API. For example: "VMware Tools is not installed."
- Unusual Data Activity Information Event: Provides information regarding the UDA scan events and can be accessed only via the Events API. For example, Snapshot is not scanned for Unusual Data Activity as learning is in progress.
For more information, see Alerts and Events API.
Security Events: Data Access events support for VMware resources
You can now closely monitor and track data restore activity access by administrators for VMware resources for a defined period with Data Access events feature. This enhancement helps ensure that the data is restored to a trusted location known to Druva and thus prevents any data security breaches.
When an administrator initiates Admin Restore activity for VMware, an access event job is created, which can be viewed from the Security Events Dashboard > Data Access page for further investigation.
For more information, see Data Access.
Hybrid Workloads: VMware events API integration with Splunk app
VMware backup (success/failure) and restore (success/failure) events API are now integrated with Druva Splunk app. This integration helps to monitor logging for threats and risks from different applications centrally.
For more information, see the Druva app for Splunk and VMware events API.
November 09, 2023
This release has minor bug fixes.
October 27, 2023
This release has minor bug fixes.
October 12, 2023
Enhancement
Introducing Curated Snapshots for Microsoft 365 (OneDrive and SharePoint)
We are excited to bring in the Curated Snapshots for Microsoft 365 feature that helps accelerate recovery time and minimizes data loss during cyber security attacks.
Curated snapshot allows you to create a customized snapshot with the latest, cleanest, and safest scanned file version available for restore.
You can restore files/folders for OneDrive and SharePoint from the Curated Snapshot without any security or malware risks. This enhancement eliminates the need to perform multiple granular restores from various snapshots.
- ►Here is a quick preview of Curated Snapshot for SharePoint and OneDrive.
-
For more information, see Curated Snapshots for Microsoft 365.
Fixed Issues
| Issue | Description |
|---|---|
|
REAL-30794 |
Fixed the navigation issue observed for the redirection from the Security Events > Administration Details page. |
September 28, 2023
This release has minor bug fixes.
Known Issues
| Issue | Description |
|---|---|
|
REAL-30794 |
You may observe incorrect redirection when navigating to the Administration Details page from the Security Events page between Oct 7 and Oct 11, 2023. Workaround: During this period, you can view the administrator details using the left navigation bar > Administration > Manage Administrator option. |
September 14, 2023
This release has minor bug fixes.
August 31, 2023
Unusual Data Activity (UDA) 1.0 end-of-life update
We have now deprecated the Unusual Data Activity 1.0 version, which was available as a part of the backup Elite license.
The new Unusual Data Activity (UDA) is a part of the Security Posture & Observability add-on.
Contact your Account Representative, Customer Success Manager, or Druva support for more details.
August 21, 2023
Enhancement
UDA for VMware: Added sudo user support for Linux virtual machines
You can now provide sudo user credentials for a non-root user while using UDA for Linux virtual machines. This enhancement thus offers more flexibility and eliminates the restriction of using only root credentials for UDA.
For more information about configuring and managing sudo user credentials, see Manage credentials for VMware servers.
For more information, see Unusual Data Activity.
Customer action required: Upgrade the VMware proxy to version 6.3.2-359254.
August 17, 2023
New Feature
Unusual Data Activity (UDA) support for SharePoint and OneDrive
You can now define the UDA settings for anomaly detection for your backed-up SharePoint and OneDrive resources from Cyber Resilience > Security Events > Settings page.
Based on the defined settings, the UDA algorithm detects malicious, intentional, or unknown activities for the number of files that are added, encrypted, deleted, or modified and subsequently generates alerts, thus providing efficient data resiliency from threats.
You can review the alerts from the Security Events > Overview > Unusual Data Activity section and take appropriate action to resolve the risk to ensure the backed-up data is safe.
- ►Here is a quick preview of UDA for SharePoint and OneDrive.
-
For more information, see Unusual Data Activity.
Customer Action Required: None
Enhancement
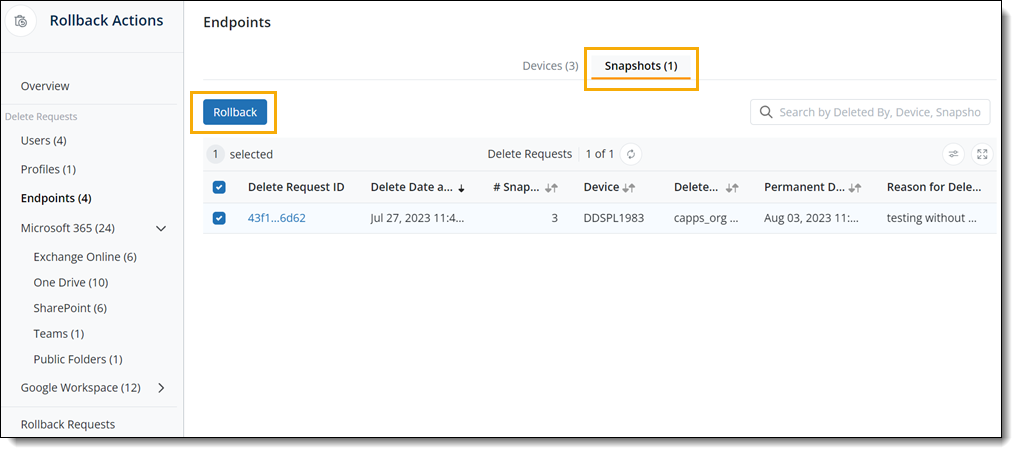
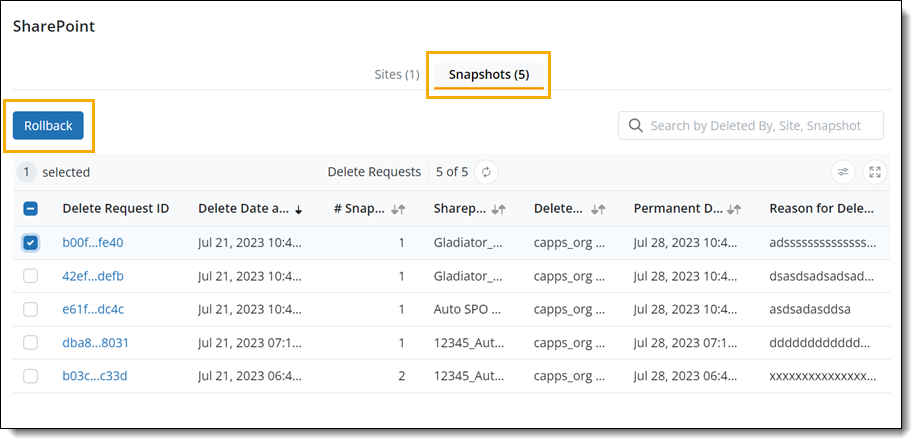
Rollback Actions support for manually deleted snapshots
With Rollback Actions, you can now rollback manually deleted snapshots for Endpoints and SaaS Apps within a configurable rollback window. By default, the Rollback Actions window is configured for 7 days.
The manually deleted snapshots are available for rollback for the specified days before they get permanently deleted.
This capability allows the administrator to revert malicious or unintended deletes without data loss and enables rapid restoring productivity.
If you have consciously triggered the deletes, the snapshots get permanently deleted after the rollback window expires.
Note: Currently, rollback action support for manually deleted snapshots is available only for Endpoints and SaaS Apps - Exchange Online, Gmail, OneDrive, Shared Drives, and SharePoint snapshots.
Endpoints
- ►Here is a glimpse of the update
SharePoint
- ►Here is a glimpse of the update
For more information, see,
Customer Action Required: None
Known Issues
| Issue | Description |
|---|---|
| REAL-31446 | Due to the backup throttling issue, the UDA logs display a higher count of modified files for OneDrive and SharePoint resources. |
| REAL-30815 | The UDA logs do not display the file owner's details for the SharePoint site if the file backup happens using REST API and the file change is through a Microsoft application or a user with an invalid email. |
| REAL-30757 | The UDA logs do not display the details related to Files Modified By for OneDrive and SharePoint resources. |
| REAL-30702 | False UDA alerts may get generated for OneDrive resources if any modifications are made to the Profiles to which the OneDrive user is mapped. |
August 07, 2023
Enhancement
Sandbox recovery: Support for automatic deletion of malicious files
In the Sandbox Recovery workflow, you can automatically delete malicious files detected via Malicious File Scan. This option safeguards against further damage and ensures the restored data is secure.
You can enable automatic deletion of malicious files from the Hybrid Workloads > Restore > Sandbox Recovery > Settings page.
- ►Here is a glimpse of the update
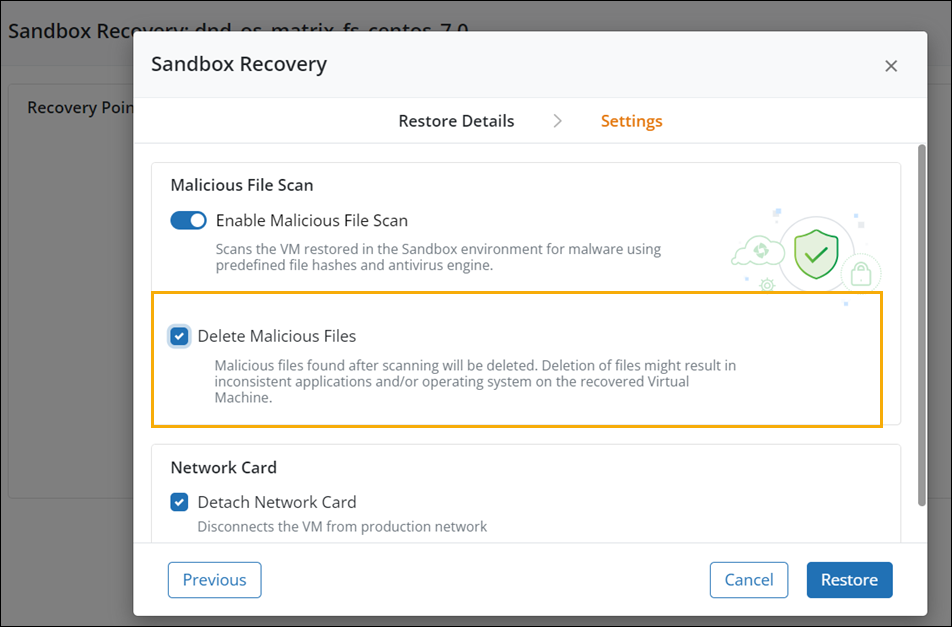
For more information, see,
Fixed Issues
| Issue | Description |
|---|---|
| REAL-31315 | Fixed the issue wherein File Hash scan is now supported for Linux VM's restored using Sandbox Recovery. |
July 20, 2023
This release has minor bug fixes.
Fixed Issues
| Issue | Description |
|---|---|
| REAL-29751 | Fixed the issue wherein the listing of malicious files / skipped files on the Sandbox Recovery Jobs page timed out intermittently in case of skipped file count exceeding 50k. |
July 06, 2023
This release has minor bug fixes.
June 23, 2023
New Feature
Sandbox recovery: Malicious File Scan support for Linux sandbox virtual machines
Use the Sandbox Recovery feature to recover a specific restore point, followed by an antivirus scan in a sandbox environment. You can certify whether the selected restore point is clean based on the scan results.
After a successful sandbox virtual machine data restore, you can scan the data for viruses and malware with the Malicious File Scan feature enabled.
For Sandbox virtual machines, you can enable the Malicious File Scan feature from the Hybrid Workloads > Restore > Sandbox Recovery > Settings page.
- ►Here is a glimpse of the update
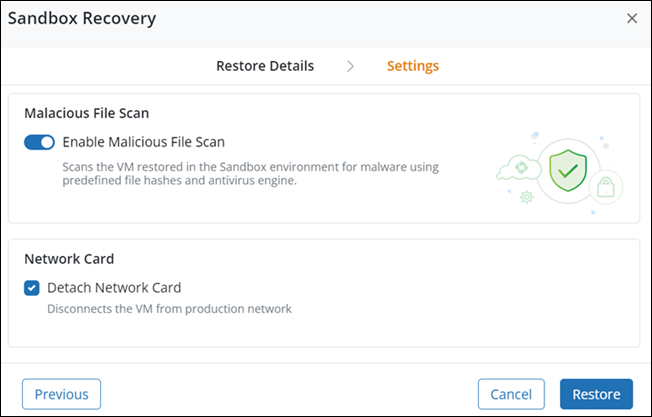
The anti-virus scan engine scans the entire data for potential viruses and malware and provides details for the following that can help you take the necessary corrective action:
-
File Scanned: Number of files scanned for a restore job
-
Malicious Files Found: Number of malicious files found in the restored snapshot
-
Files Scan Skipped: Number of files skipped from the scan
- ►Here is a quick preview of Sandbox Recovery.
-
For more information, see,
Known Issues
| Issue | Description |
|---|---|
| REAL-29751 |
Malicious files listing page for the Sandbox Recovery Jobs page times out intermittently. You will observe this issue when the count of skipped files is beyond 50k files. Workaround: You can view the detailed report using the Download Log option on the UI. |
June 08, 2023
This release has minor bug fixes.
May 25, 2023
New Feature
Sandbox recovery: Malicious File Scan support for Windows sandbox virtual machines
This feature is available for all customers using the Windows operating system. It is under early access and is available for limited customers using the Linux operating system.
Use the Sandbox Recovery feature to recover a specific restore point, followed by an antivirus scan in a sandbox environment. You can certify whether the selected restore point is clean based on the scan results.
After a successful sandbox virtual machine data restore, you can scan the data for viruses and malware with the Malicious File Scan feature enabled.
For Sandbox virtual machines, you can enable the Malicious File Scan feature from the Hybrid Workloads > Restore > Sandbox Recovery > Settings page.
- ►Here is a glimpse of the update

The anti-virus scan engine scans the entire data for potential viruses and malware and provides details for the following that can help you take the necessary corrective action:
-
File Scanned: Number of files scanned for a restore job
-
Malicious Files Found: Number of malicious files found in the restored snapshot
-
Files Scan Skipped: Number of files skipped from the scan
- ►Here is a quick preview of Sandbox Recovery.
-
For more information, see,
May 11, 2023
New Feature
Unusual Data Activity (UDA) support for VMware resources
You can now define the UDA settings for anomaly detection for your backed-up VMware resources from Cyber Resilience > Security Events > Settings page.
- ►Here is a glimpse of the update
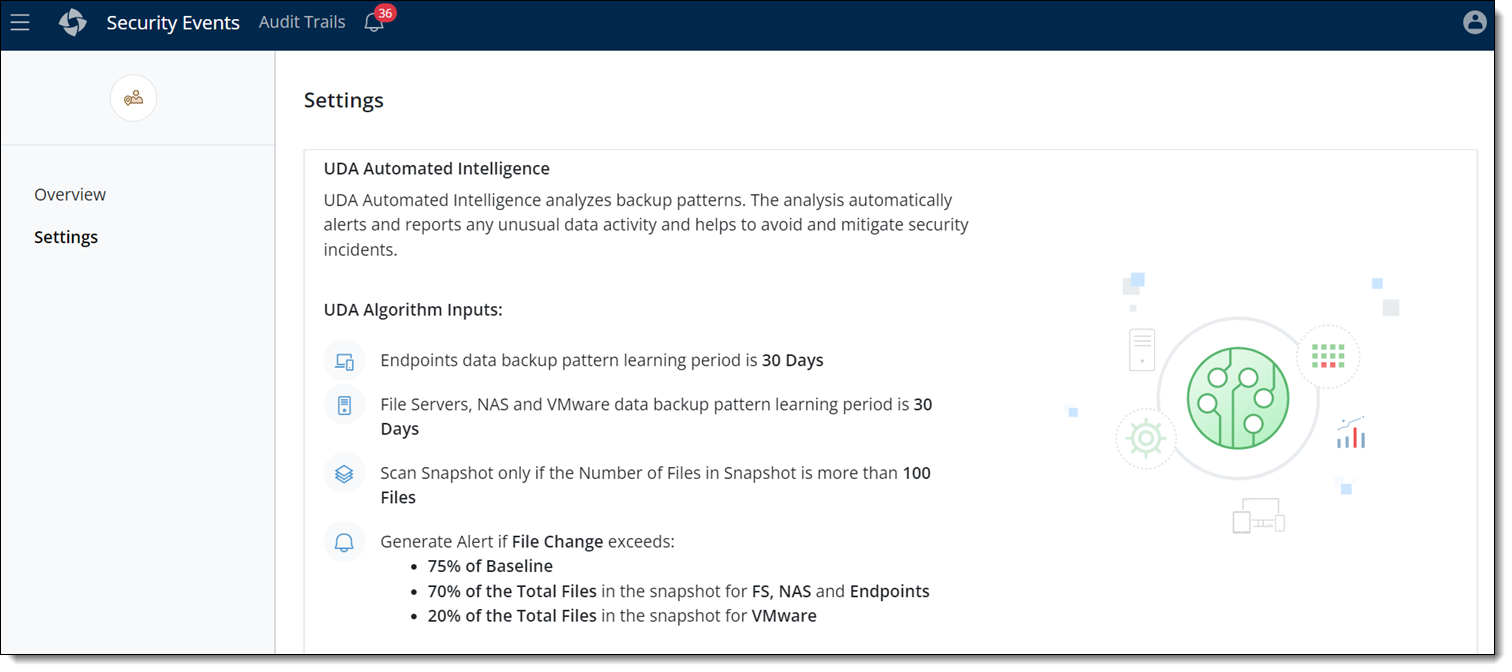
Based on the defined settings, the UDA algorithm detects malicious, intentional, or unknown activities for the number of files that are added, deleted, or modified and subsequently generates alerts, thus providing efficient data resiliency from threats.
You can review the alerts from the Security Events > Overview > Unusual Data Activity section and take appropriate action to resolve the risk to ensure the backed-up data is safe.
For more information, see Unusual Data Activity.
Customer Action Required: None
April 27, 2023
This release has minor bug fixes.
April 13, 2023
This release has minor bug fixes.
March 30, 2023
Enhancement
Endpoints: Manage antivirus scan during device replace
Administrators can now enable or disable an antivirus scan check before restoring data to a replaced device.
By default, the antivirus scan check is enabled to ensure that the data restored to the replaced device is safe and secure.
Navigate to the Ransomware Recovery > Malicious File Scan > Settings > Edit and select the Skip Antivirus Scan during Device Replacement check box to disable the antivirus scan and deselect the checkbox to enable the scan.
- ►Here is a glimpse of the update
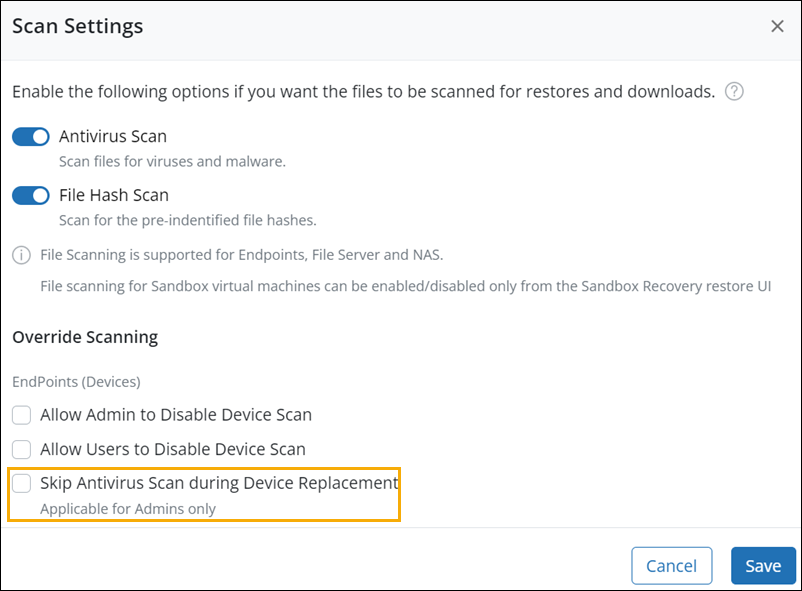
Alternatively, you can also perform this action using API.
For more information, see,
Customer Action Required: None
March 16, 2023
This release has minor bug fixes.
March 03, 2023
Enhancement
An enhanced experience for Unusual Data Activity (UDA)
Unusual Data Activity (UDA) for VMware is under early access and is available for limited customers.
With this release, we bring the following enhancements to Unusual Data Activity:
Unusual Data Activity with customizable settings
Unusual Data Activity (UDA) is now enhanced to allow you to customize and define the UDA settings for anomaly detection for your backed-up resources, thus providing efficient data resiliency from threats.
You can define the UDA Settings from Cyber Resilience > Security Events > Settings page.
- ►Here is a glimpse of the update
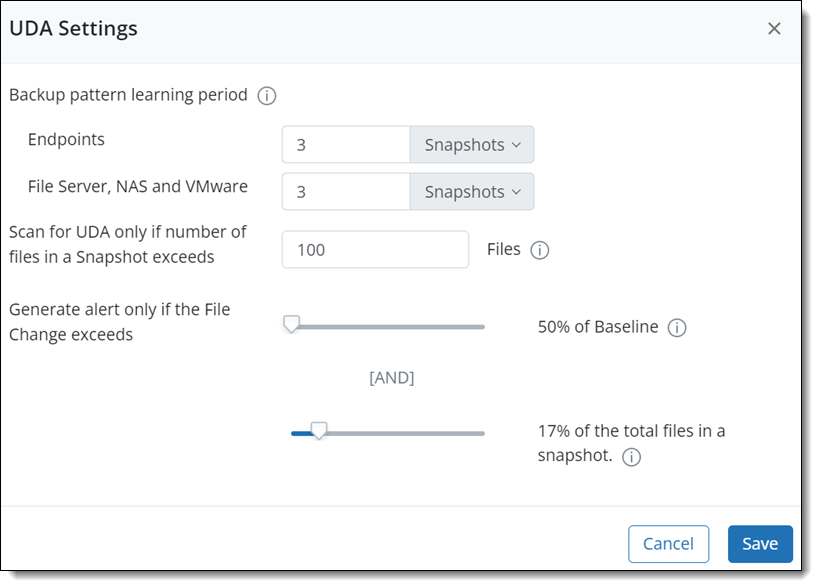
Based on the defined settings, the UDA algorithm detects malicious, intentional, or unknown activities for the number of files that are added, deleted, or modified and subsequently generates alerts.
You can review the alerts from the Security Events > Overview > Unusual Data Activity section and take appropriate action to resolve the risk to ensure that the backed-up data is safe.
Improved Data Activity trend graph
The Data Activity Trend that represents data backed up in the resource by snapshots is enhanced to provide a more detailed view for better monitoring and understanding of Unusual Data Activity.
- ►Here is a glimpse of the update
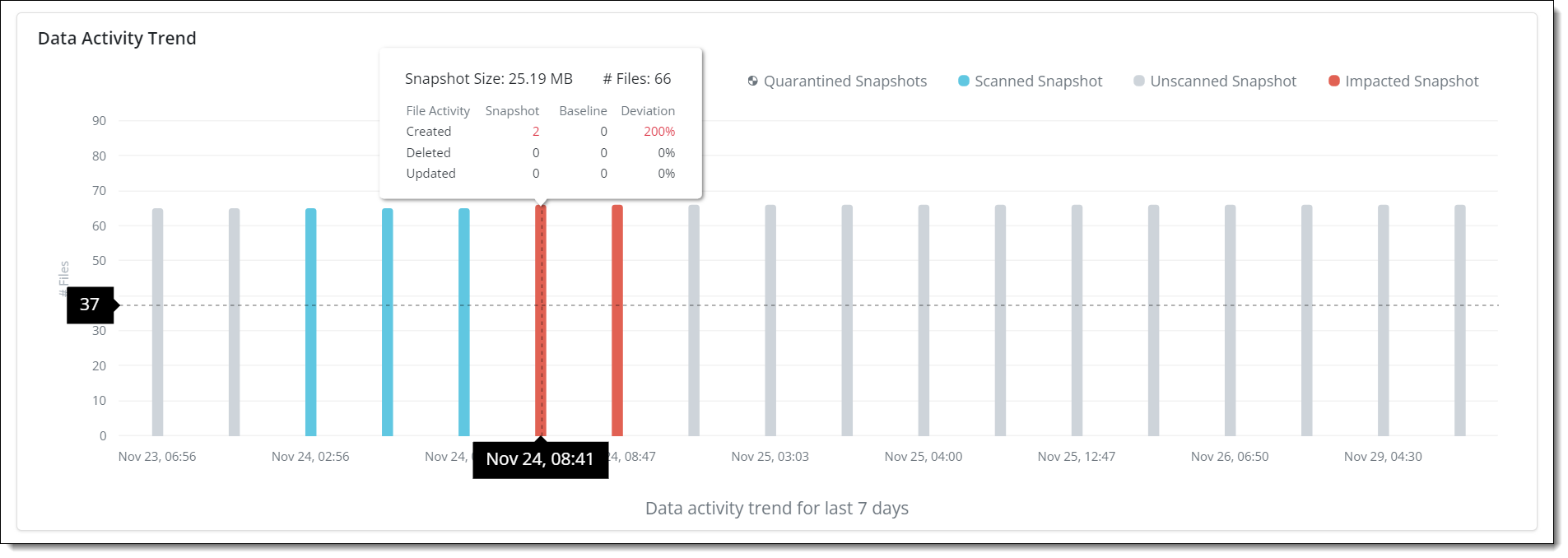
For more information, see Unusual Data Activity.
- ►Here is a quick preview of the enhanced Unusual Data Activity.
-
Customer Action Required: To sign up for this feature, contact support.
Feb 09, 2023
This release has minor bug fixes.
Jan 28, 2023
New Feature
Sandbox recovery: Malicious File Scan support for windows sandbox virtual machines
This feature is under early access and is available for limited customers.
Use the Sandbox Recovery feature to recover a specific restore point, followed by an antivirus scan in a sandbox environment. You can certify whether the selected restore point is clean based on the scan results.
After a successful sandbox virtual machine data restore, you can scan the data for viruses and malware with the Malicious File Scan feature enabled.
For Sandbox virtual machines, you can enable the Malicious File Scan feature from the Hybrid Workloads > Restore > Sandbox Recovery > Settings page.
- ►Here is a glimpse of the update

The anti-virus scan engine scans the entire data for potential viruses and malware and provides details for the following that can help you take the necessary corrective action:
-
File Scanned: Number of files scanned for a restore job
-
Malicious Files Found: Number of malicious files found in the restored snapshot
-
Files Scan Skipped: Number of files skipped from the scan
For more information, see,
New API for listing count of restore scan jobs
We have added the List count of restore scan jobs API to support automation and get information about the total count of all the restore scan jobs for different resource types- File Server, NAS, Endpoints, and so on.
For more information, see Developer Portal.
Jan 12, 2023
This release has minor bug fixes.
Archived release notes
For release notes of previous cloud updates, see Archived Release Notes.

