Archived Release Notes - Cyber Resilience
Cloud Upgrade on Dec 29, 2022
New Feature
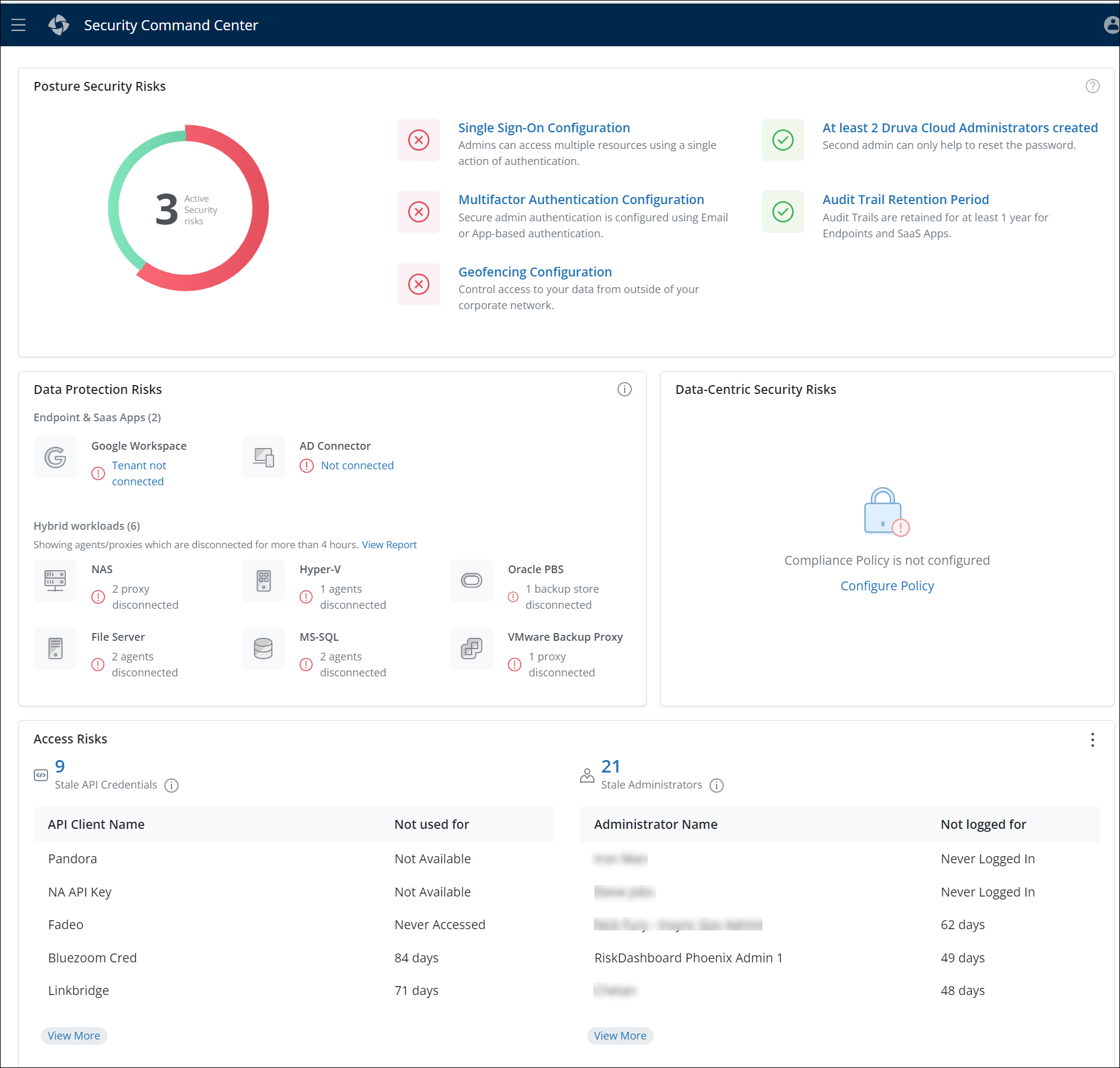
Introducing Security Command Center
A centralized dashboard that highlights the overall posture of the Druva environment in terms of:
- Cloud Platform Security
- Data Compliance
- Data Protection
- Data Access risks
The Security Command Center console is the starting point from where you can view the security risk details for your Cloud Platform and data sources and monitor its overall security health.
It also provides actionable guidance on corrective actions that can be taken to mitigate identified risks, such as those related to cloud platform security, data compliance, data protection, and data access. By regularly monitoring the security and risk posture using the Security Command Center console, you can proactively identify and address potential security risks, helping to ensure the security and compliance of your organization's data.
For more information, see Security Command Center.
Customer action required: None
Cloud Upgrade on Dec 15, 2022
This release has minor bug fixes.
Cloud Upgrade on Dec 01, 2022
This release has minor bug fixes.
Cloud Upgrade on Nov 17, 2022
This release has minor bug fixes.
Cloud Upgrade on Oct 15, 2022
New Feature
Quarantine infected Microsoft 365 and Google Workspace resources
You can now isolate the infected resources that belong to Microsoft 365 (OneDrive and SharePoint Online) and Google Workspace (Google Drive and Shared Drives) to prevent the infection from spreading.
The Quarantine Bay feature in the Ransomware Recovery module enables you to quarantine infected snapshots on the impacted Microsoft 365 (OneDrive and SharePoint Online) and Google Workspace (OneDrive and SharePoint Online) resources and helps safeguard your organization from further infection by barring users or administrators from downloading or restoring the infected data to other data sources.
For more information, see,
Customer action required: None
Cloud Upgrade on Sep 08, 2022
This release has minor bug fixes.
Cloud Upgrade on Aug 25, 2022
This release has minor bug fixes.
Cloud Upgrade on Aug 11, 2022
New Feature
Data Lock support for snapshots
With Data Lock support, you can now protect your data from accidental or malicious deletions. You cannot delete the snapshots from Ransomware Recovery > Quarantine Bay if Data Lock is enabled for resources (Endpoints, File Servers, NAS, and VMware) within the backup policy.
For more information, see
Customer action required: None.
Cloud Upgrade on July 28, 2022
This release has minor bug fixes.
July 08, 2022
Unusual Data Activity (UDA) events integration with Splunk
With this release, we have integrated Unusual Data Activity (UDA) events with Splunk, which allows you to view UDA events. For more information, see the Druva Add-on for Splunk.
Cloud Upgrade on June 16, 2022
This release has minor bug fixes.
Cloud Upgrade on June 02, 2022
This release has minor bug fixes.
Cloud Upgrade on May 28, 2022
New Feature
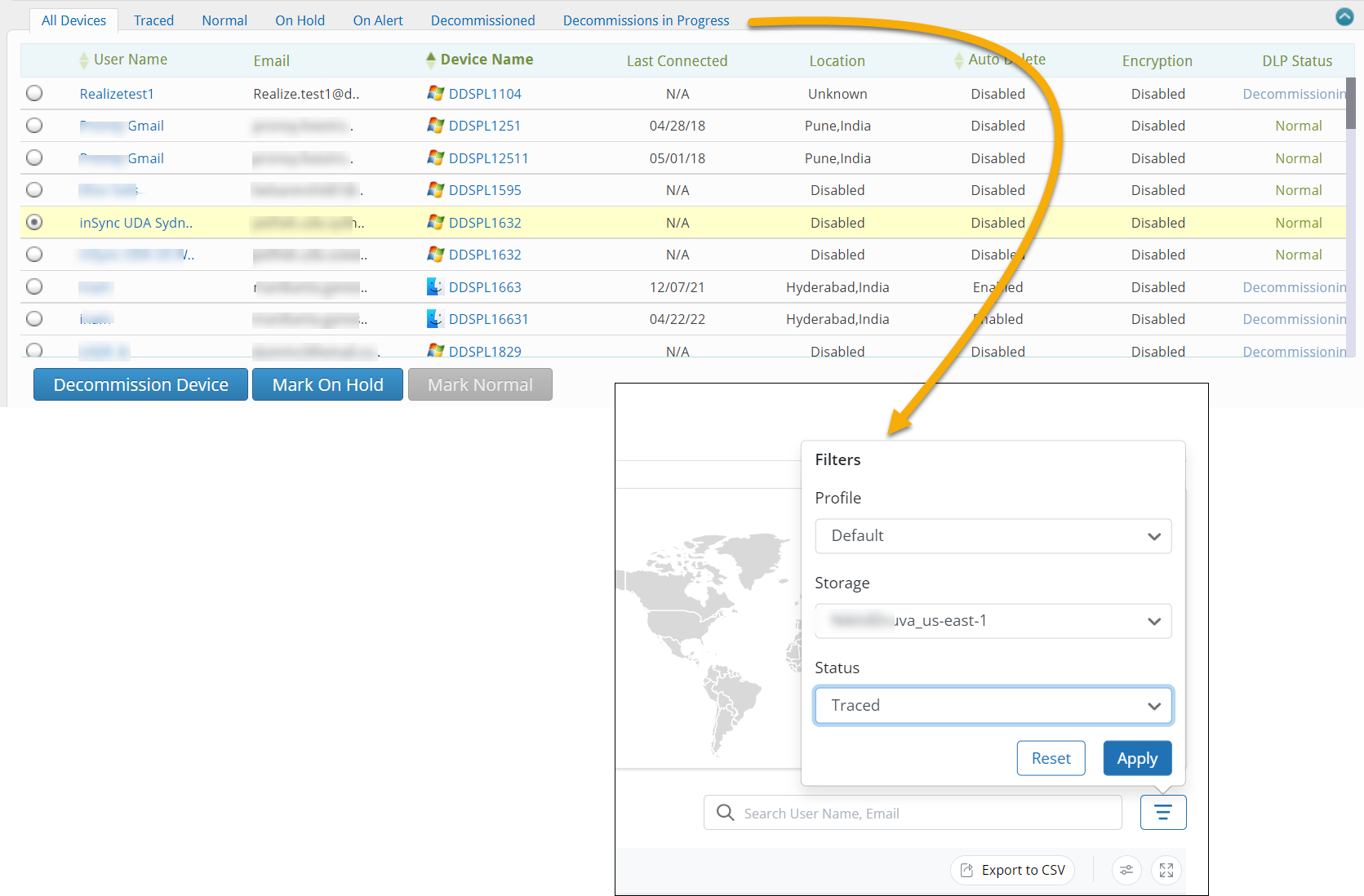
Refreshed Data Loss Prevention (DLP) page
We have refreshed the Data Loss Prevention (DLP) page to provide an enhanced and intuitive user experience.
Here is a preview of the Data Loss Prevention (DLP) page.
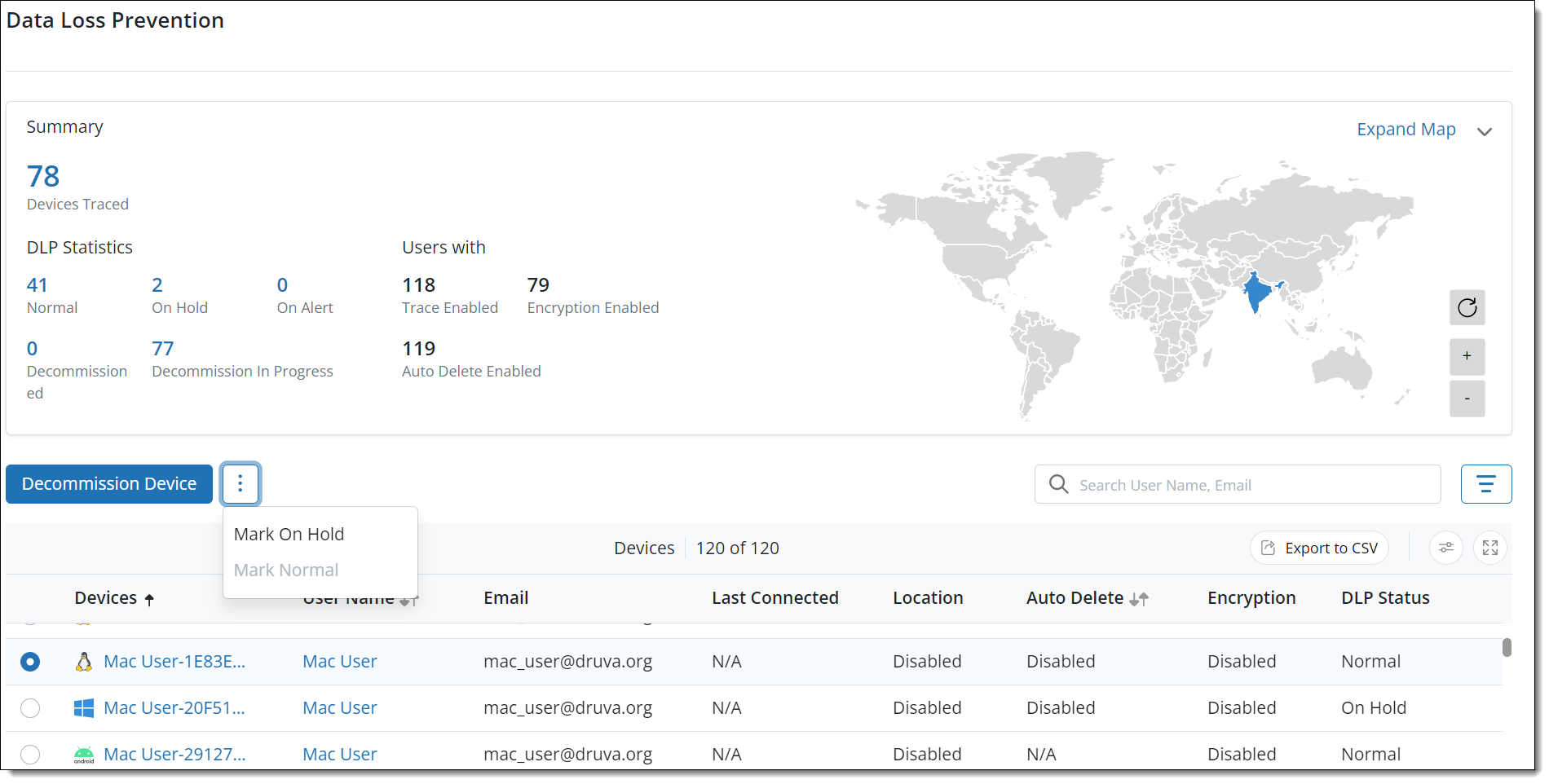
Key highlights
- All the information on the DLP Summary card is now consolidated into a single card.
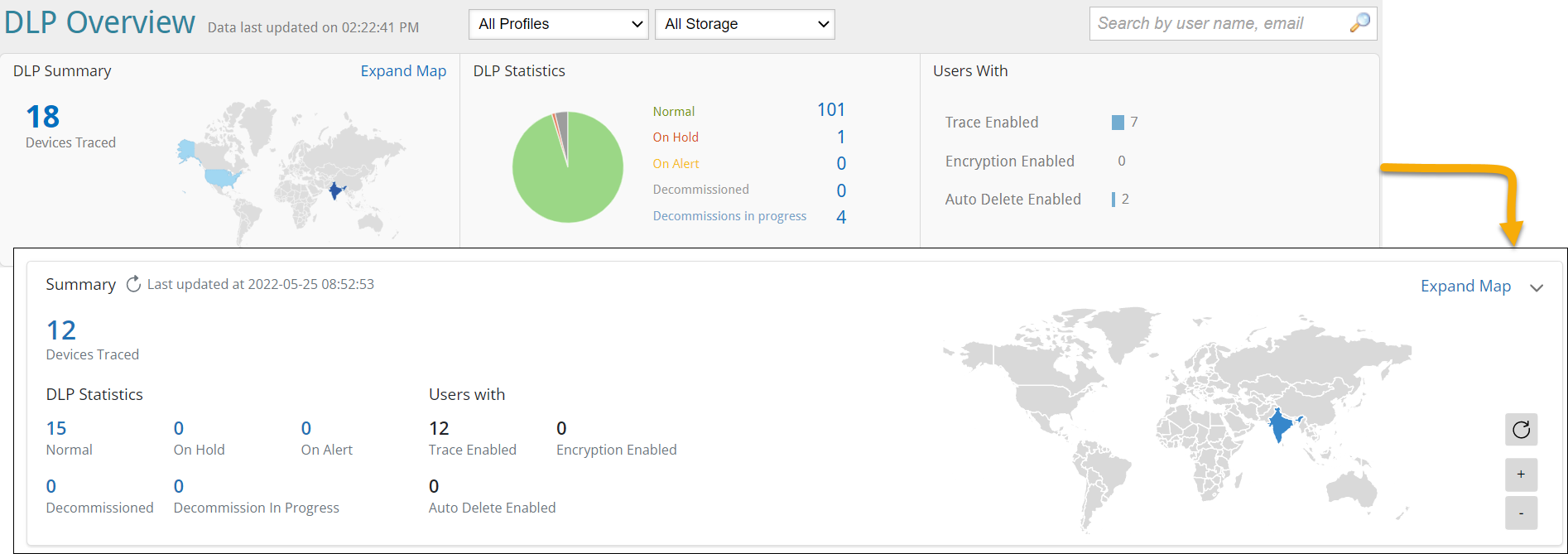
- Added a filter option. Moved the Profiles, Storage selection, and statuses (Traced, Normal, On Hold, and so on) as criteria under this filter to sort the listing.
Customer action required: None
For more information, see Data Loss Prevention Overview page.
Cloud Upgrade on May 05, 2022
New Feature
Protect mission-critical backups from accidental or malicious deletion with Rollback Actions
You can now configure the Rollback Actions capability to enhance your organization’s data security posture and safeguard backup data from accidental or malicious deletion.
With Rollback Actions, you can rollback deleted entities within a configurable rollback window. The deleted entities are available for rollback for the specified days before the entity and its backups are permanently deleted. This provides the administrator the ability to revert malicious or unintended deletes without any loss of data and enables the restoration of productivity rapidly. If you have consciously triggered the deletes, the backup copies will be permanently deleted after the rollback window expires and there will be no impact on what you were trying to do.
Action Required: Existing Ransomware Recovery customers will get this offering as part of their existing license. Customers who don’t have Ransomware Recovery license can opt to purchase the Backup Security Posture and Observability license exclusively. To obtain the license, contact Support.
Note: Currently, this feature is available only for Druva Public Cloud customers.
- ►Here is a quick video to get you started
-
For more information, see Rollback Actions.
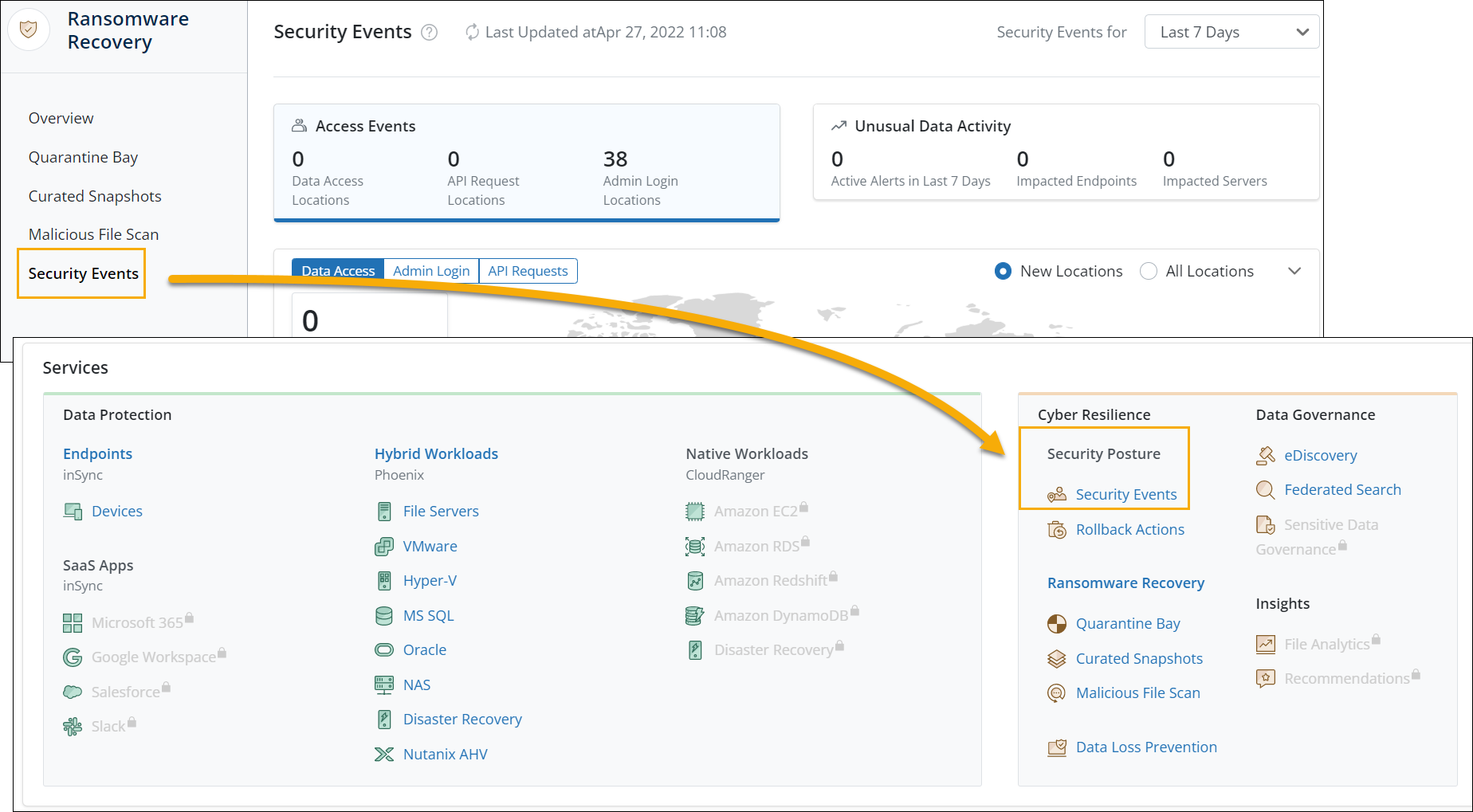
Leverage the Backup Security Posture and Observability license to enhance the security posture and observability of your backup environment
We have added a completely new license, Backup Security Posture and Observability, which includes capabilities such as Rollback Actions, Security events and SIEM integrations (FireEye Helix and Splunk)
Also, the Security Events and Rollback Actions capabilities can now be accessed from the Security Posture category under the Cyber Resilience service.
Action required: Existing Ransomware Recovery customers will get this offering as part of their existing license. Customers who don’t have a Ransomware Recovery license can opt to purchase the Backup Security Posture and Observability license exclusively.
Changed access path for Security Events services
You can now access the Security Events and Unusual Data Activity (UDA) services from the new Cyber Resilience > Security Posture services section.
Customer action required: None. With the Ransomware Recovery license, Security Events service is available by default.
For more information, see Security Events.
Known Issues
| Issue | Description |
|---|---|
| REAL-22865 | The Quarantine Bay listing page erroneously lists those resources (Servers and Virtual Machines) whose backup sets are deleted and are no longer available. |
|
DCP-8500 |
At times, after you trigger a rollback, all the entities in the delete request, the following message is displayed: Rollback Service Temporarily Unavailable Workaround: You can safely ignore the message and track the Rollback Request. |
Cloud Upgrade on March 24, 2022
New Feature
Quarantine infected VMware resources
You can now isolate the infected virtual machines to prevent the infection from spreading.
The Quarantine Bay feature in the Ransomware Recovery module enables you to quarantine infected snapshots on the impacted virtual machines and helps safeguard your organization from further infection by barring users or administrators from downloading or restoring the infected data to other data sources.
For more information, see,
- ►Here is a glimpse of the update
Known Issues
| Issue | Description |
|---|---|
| REAL-22397 | Suppose log backups follow a full backup, and the start time of your quarantine range falls between the creation times of a full backup snapshot and the subsequent log backup snapshot. Druva Phoenix blocks SQL PIT restores from the log backups marked as quarantine, however, the UI allows you to submit such a restore job. |
Cloud Upgrade on March 10, 2022
This release has minor bug fixes.
Cloud Upgrade on Feb 24, 2022
This release has minor bug fixes.
Cloud Upgrade on Feb 10, 2022
This release has minor bug fixes.
Cloud Upgrade on Jan 27, 2022
New Feature
A new Ransomware Recovery Overview page
You can now get a complete picture of the overall status of each resource in a single pane of glass. Use the Overview page to view the important details such as the number of Quarantined Resources, Curated Snapshots, Malicious File Scan Jobs, Unusual Data Activity Alerts, and so on. With this view, you can quickly identify the actionable to ensure business continuity.
- ►Here is a glimpse of the update
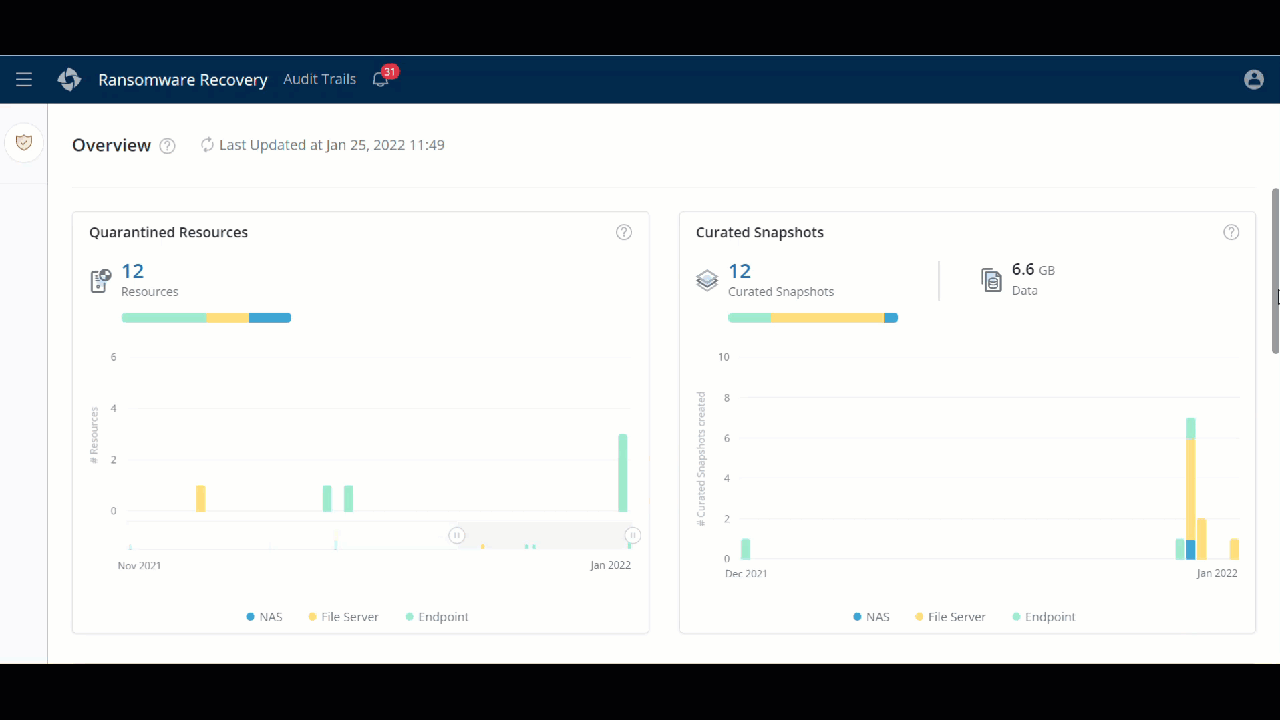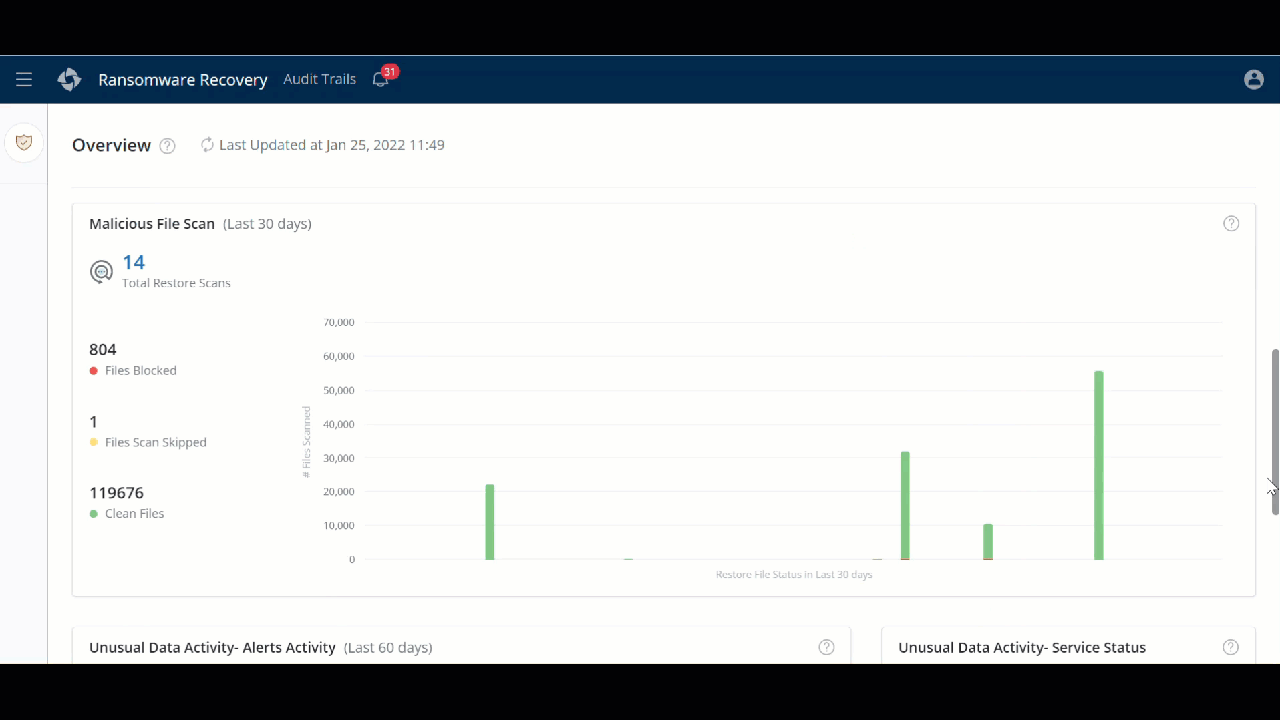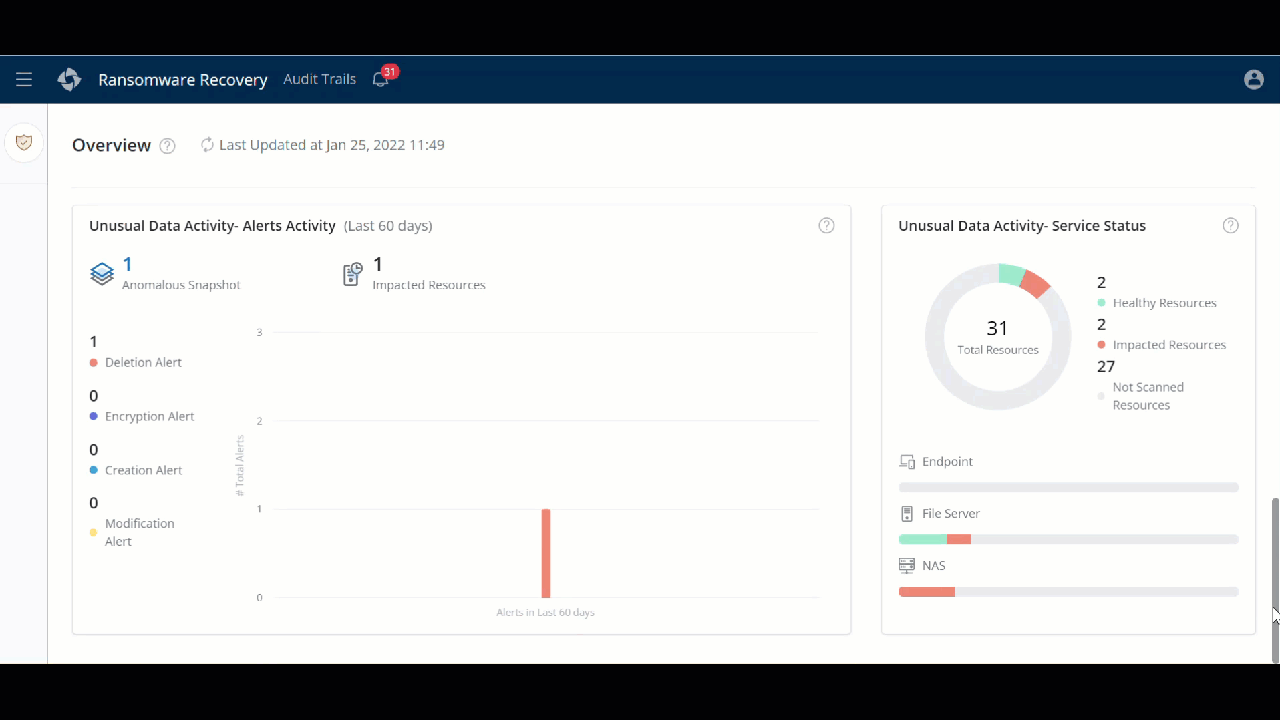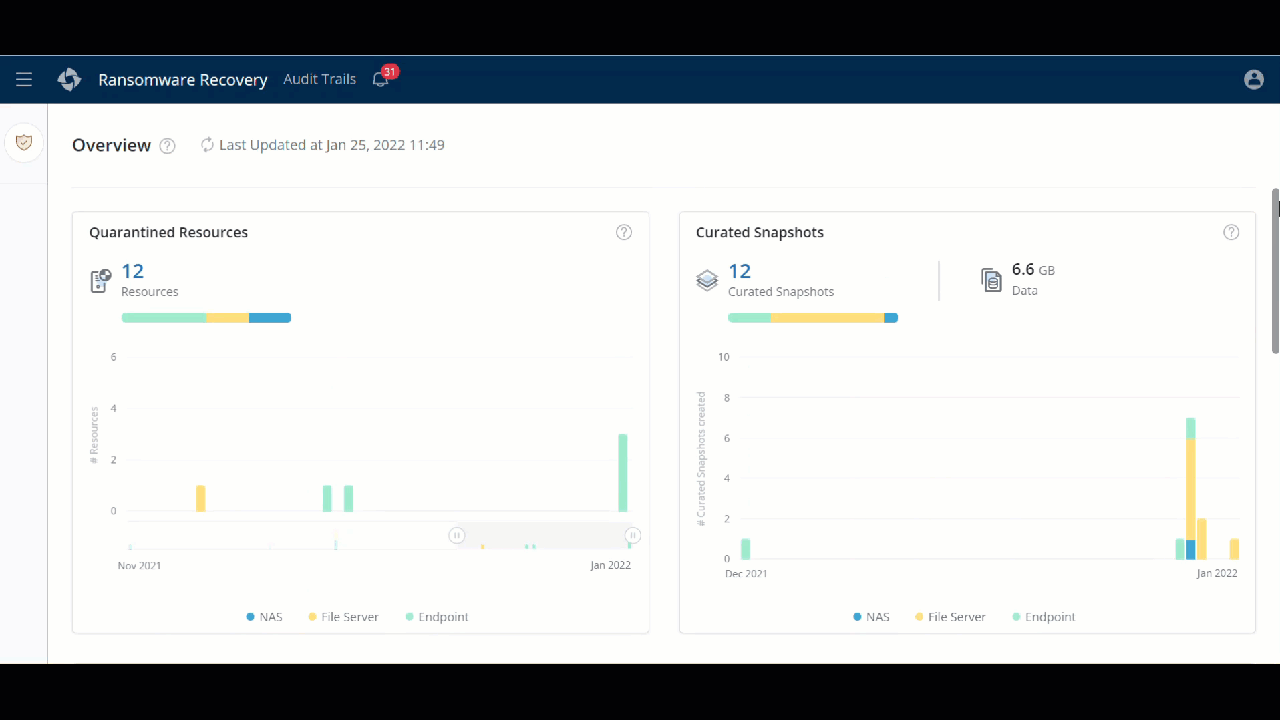
Customer action required: None.
For more information, see the Overview page.
Enhancement
Prevent accidental deletion of Endpoints and Servers data
You will now be prompted to provide a reason when you delete a snapshot or file hash value. This capability will help prevent accidental deletions, and the reason will be captured in the Audit Trail for auditing purposes.
- ►Here is a glimpse of the update
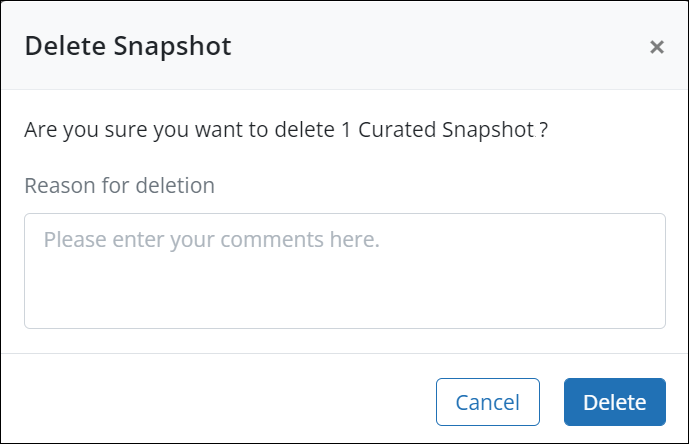
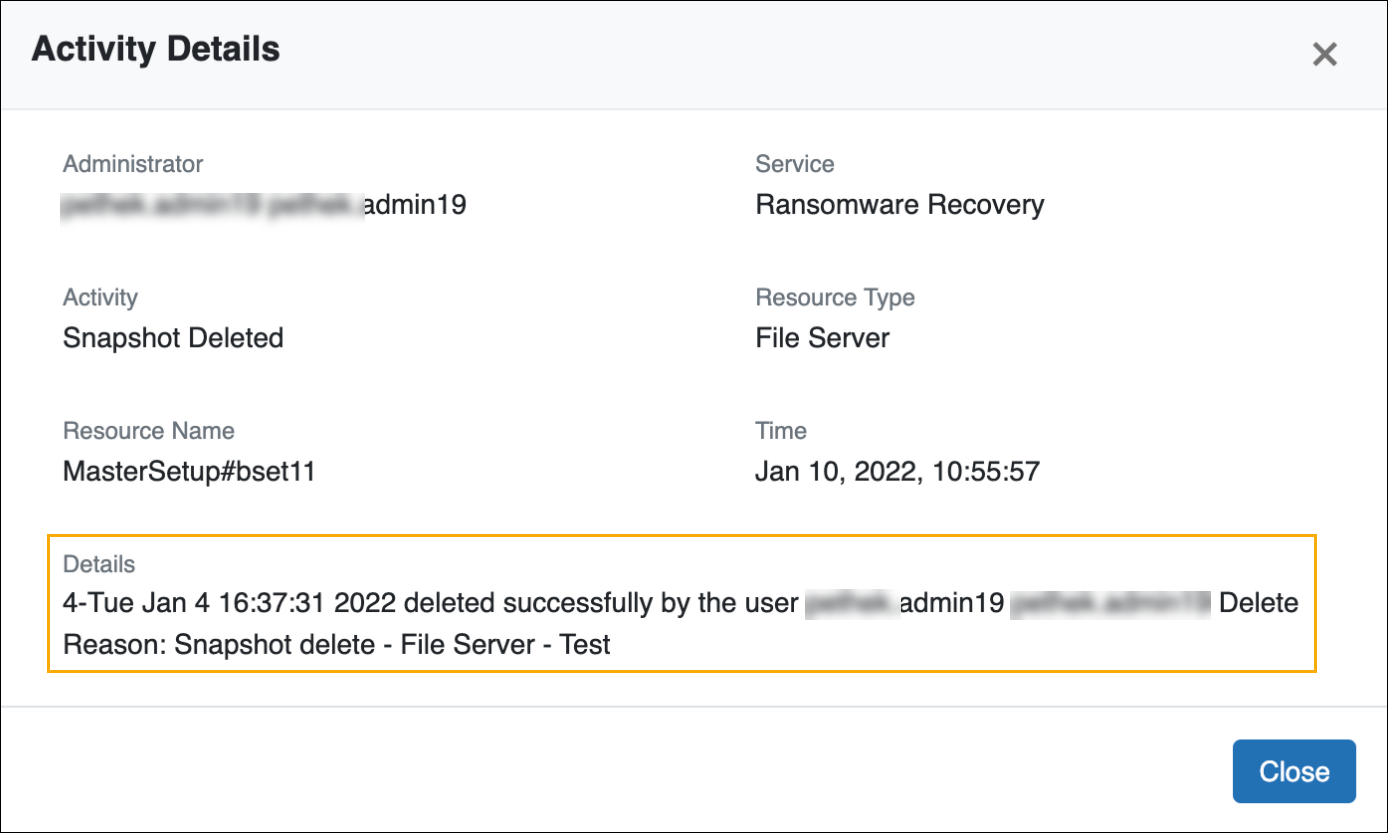
Customer action required: None.
For more information, see,
Cloud Upgrade on Nov 18, 2021
Enhancement
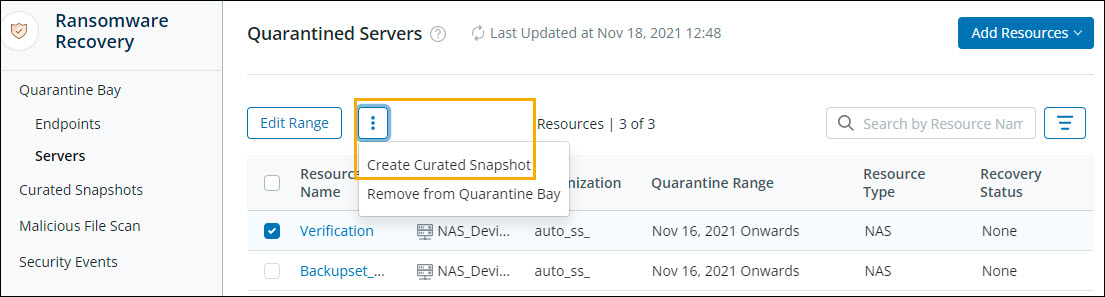
Option to create Curated Snapshot from Quarantine Bay
You no longer need to go to Curated Snapshot UI to create a Curated Snapshot for Endpoints and Servers. Now you can create a Curated Snapshot while quarantining the resource itself. For your ease, we have now added this option to the Quarantine Bay UI as well.
With this enhancement, you have to navigate to Quarantine Bay UI, select the Resource Name, and click  > Create Curated Snapshot.
> Create Curated Snapshot.
Cloud Upgrade on Sep 23, 2021
New Feature
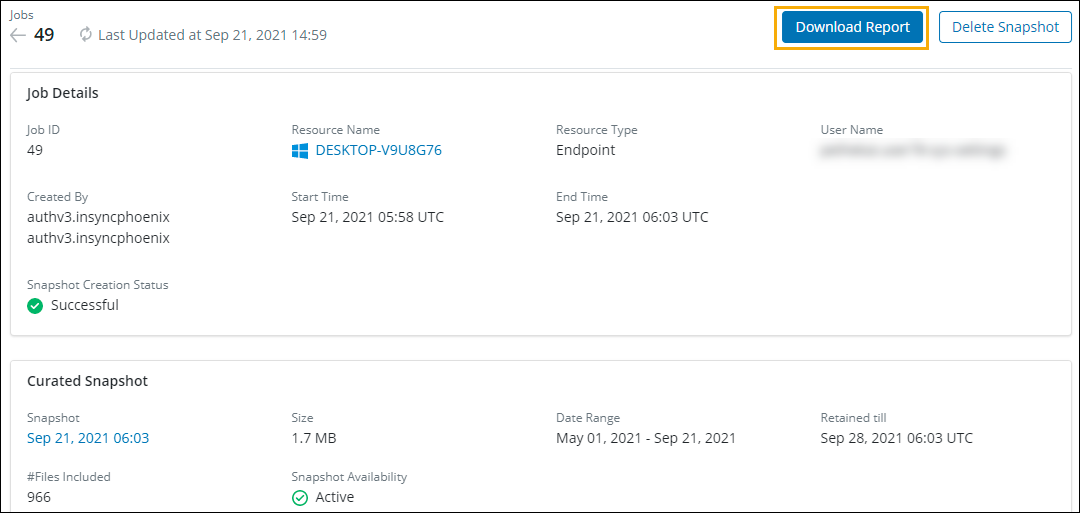
Monitor Curated Snapshots for endpoints and servers
We have now added Download Report functionality that helps you monitor and review the details of malicious files discovered while scanning the files to create Curated Snapshot for endpoints and servers.
Administrators can now generate and download the report in CSV format and get an overview of primary details such as the File Name, File Type, list of skipped files from Curated Snapshot along with its reason, and so on.
For more information, see,
Cloud Upgrade on Sep 09, 2021
New Feature
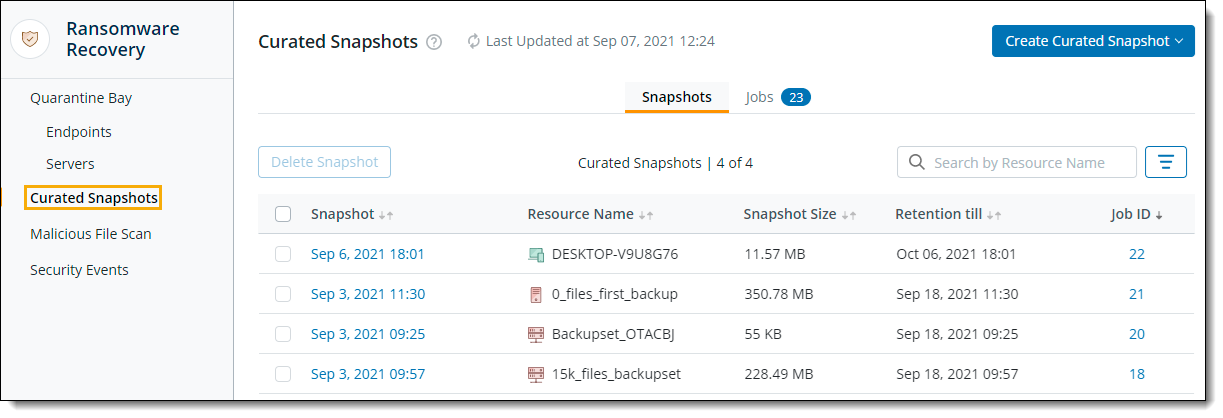
Introducing Curated Snapshots for endpoints and servers
We are excited to bring in the Curated Snapshots feature to you that allows you to create a customized snapshot that is the latest, cleanest, and safest scanned file version available for restore. You can restore files for endpoints and servers from the Curated Snapshot without any security or malware risks.
This enhancement eliminates the need to perform multiple granular restores from various snapshots and thus accelerates recovery time and minimizes data loss in the event of cyber security attacks.
For more information, see Curated Snapshots.
Cloud Upgrade on July 30, 2021
Fixed Issue
| Issue | Description |
|---|---|
| REAL-16027 | Unusual Data Activity (UDA) encryption alert does not get generated when you backup encrypted files. |
Cloud Upgrade on July 24, 2021
Known Issue
| Issue | Description |
|---|---|
| REAL-16027 | Unusual Data Activity (UDA) encryption alert does not get generated when you backup encrypted files. |
Cloud Upgrade on June 03, 2021
New Feature - Protect your data from ransomware attacks
At Druva, the security of your organization's data is our topmost priority. With the increasing risk of ransomware attacks, data breaches, and unauthorized access, now it's not only important to safeguard your data but also to have a response plan in place in case you face a cyber threat.
The availability of this feature may be limited based on the license type, region, and other criteria. To access this feature, contact your Druva Account Manager or Druva Support.
To help you protect the data minimize the risks of data loss, we have developed the Accelerated Ransomware Recovery module that aids you to do the following:
-
Detect anomalous behavior - When a data source is attacked by ransomware, it starts manipulating the data stored in it. Such behavior is suspicious in nature and is unlike how the resource owner works with the data on that data source. Since anomalies of this type often indicate issues that require attention, the Unusual Data Activity feature flags such anomalous behavior and notifies you via an alert email. For more information, see Unusual Data Activity.
-
Quarantine infected data sources - When you are already aware that a data source is infected with ransomware, you would want to isolate the infected data in order to contain the infection and restrict it from spreading. The Quarantine feature in the Ransomware Recovery module enables you to quarantine infected snapshots on the impacted data sources and helps safeguard your organization from further infection by barring users or administrators from downloading or restoring the infected data to other data sources. For more information see Ransomware Recovery for EndPoints and Ransomware Recovery for Servers.
-
Scan the data before restoring - Securely backed up data might already be infected and when you restore such data to a particular destination, you run the risk of infecting the destination machine. Using the Malicious File Scan feature, you can scan the data for viruses and malware during a data restore activity. Moreover, you can enable this feature for end-users so that they too can scan the data before restoring it. Druva scans the entire data for potential viruses and malware and blocks the malicious files and only restores the clean files. For more information, see Scan Files Before Restoring.
-
Restrict unauthorized data access - With the employees of an organization spread across the globe, it is critical that only the authorized people in the organization have access to the relevant data that you back up. Druva offers Insights, a dashboard that shows you the details of all administrator login events, data access events, and API requests made from new geographic locations in the past week or month. If you see that someone is accessing the data from an undesired location, you can block their account. This information helps you gain situational awareness about access to the backed-up data by gathering events from all Druva products. For more information, Security Insights Dashboard.
Cloud Upgrade on July 03, 2020
New Features
Realize Storage Insights - Subscribe to saved filters
Realize administrators can now subscribe to saved filters and be informed about the non-critical data growth in their organization on a regular basis. Filters can also be subscribed by non-Realize administrators or other staff in the organization.
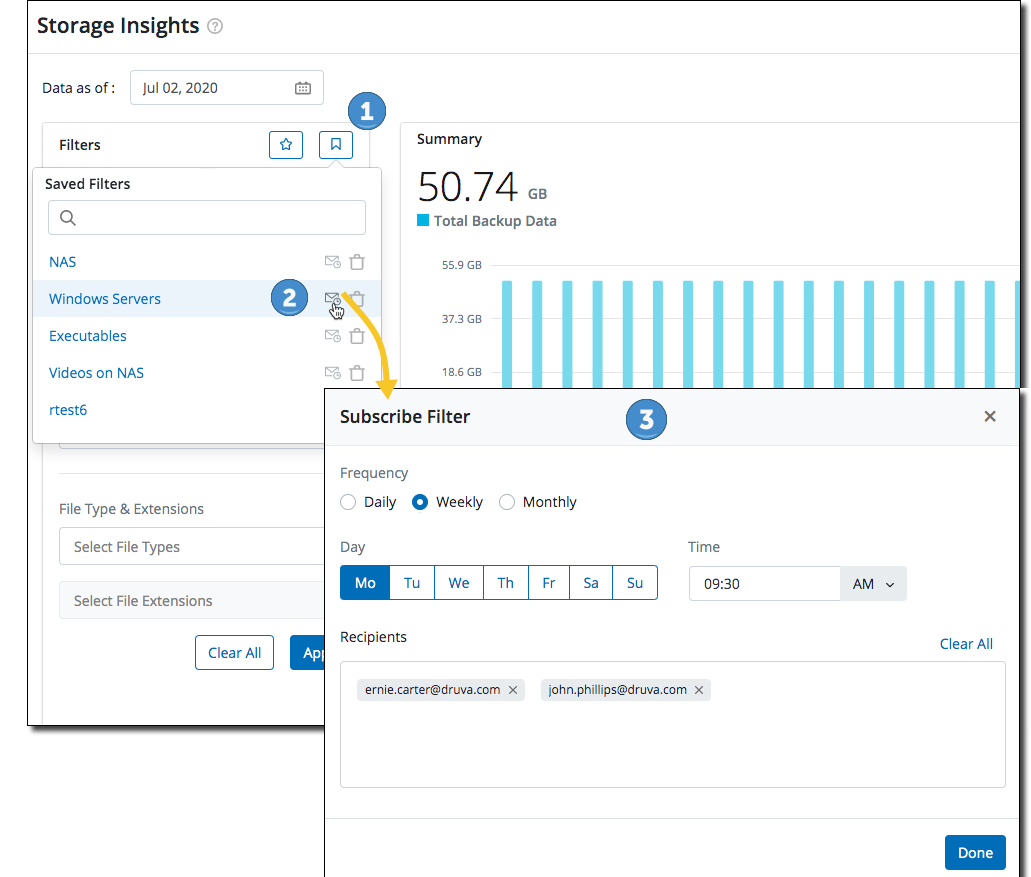
For subscribe instructions, see About Realize Storage Insights.
Recommendations
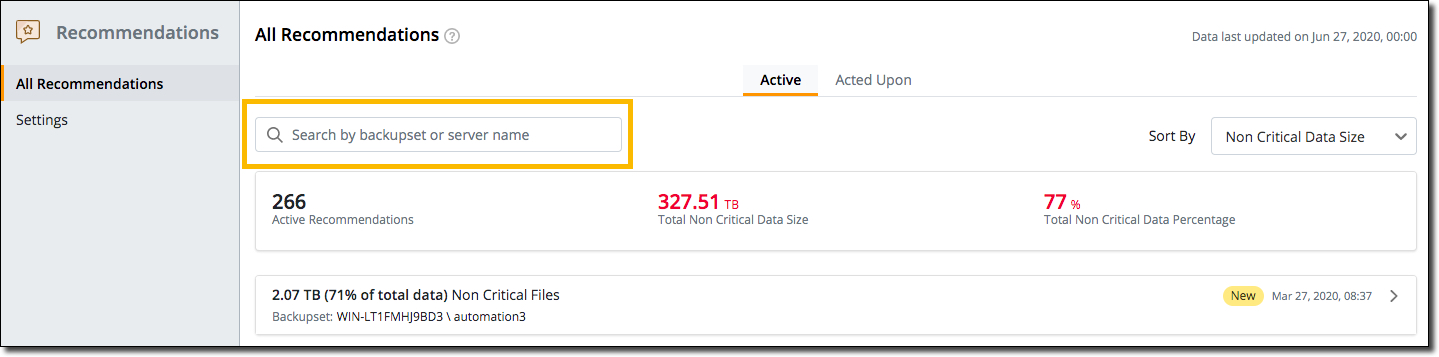
Search Recommendations using Backup Set or Server Name
Administrators can now search and view particular Recommendations using the Backup Set or Server name.
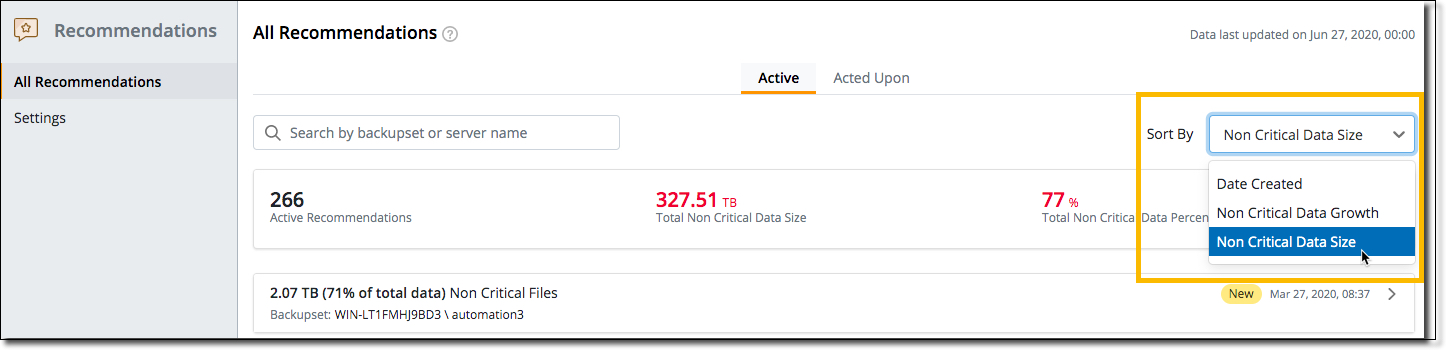
Sort Recommendations
By default, Recommendations are listed in order with the backup set having the largest amount of non-critical data at the top and the least at the bottom. Now, administrators have the option to sort the recommendations based on the following parameters-
- Date Created - List Recommendations by date created with the latest generated recommendation at the top.
- Non Critical Data Growth - List Recommendations by the growth of non-critical data in backup sets with the largest amount at the top.
- Non Critical Data Size - The default, lists Recommendations by the non-critical data size with backup set having the largest amount of non-critical data at the top.
For more information, see About Recommendations.
Known Issue
| Issue | Description |
|---|---|
| REAL-2797 | If a Backup set name is too lengthy, complete name is not displayed in the Select Resources Filter in Realize Storage Insights. |
Cloud Upgrade on Jun 19, 2020
Enhancement
Druva Realize is now enabled for Product Cloud Administrators
In addition to Druva Cloud Administrators, now Phoenix Cloud administrators can access Realize Storage Insights and Recommendations services.
New Features
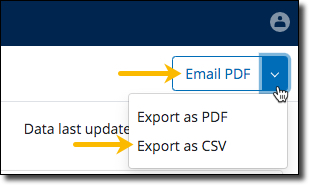
Realize Storage Insights - More options to export Realize Storage Insights view
In addition to PDF, Realize administrators can now export Realize Storage Insights view using the following options -
-
Email - Share Realize Storage Insights view over Email as a PDF attachment.
-
CSV - Export Realize Storage Insights view in CSV format. Administrators can have a more granular view of the data or use the CSV to ingest in 3rd party applications for further processing and gain additional insights.
Recommendations - Exclude non-critical file types from Phoenix Content Rule using Recommendations
Administrators can now update the Phoenix Content Rule associated with a backup set directly from a Recommendation and exclude the non-critical file types from backup.
Administrators have option to exclude the non-critical files either from a particular backup set or all the backup sets to which a Phoenix Content Rule is associated.
Use the Exclude Non Critical Data feature in a Recommendation to exclude the file types.
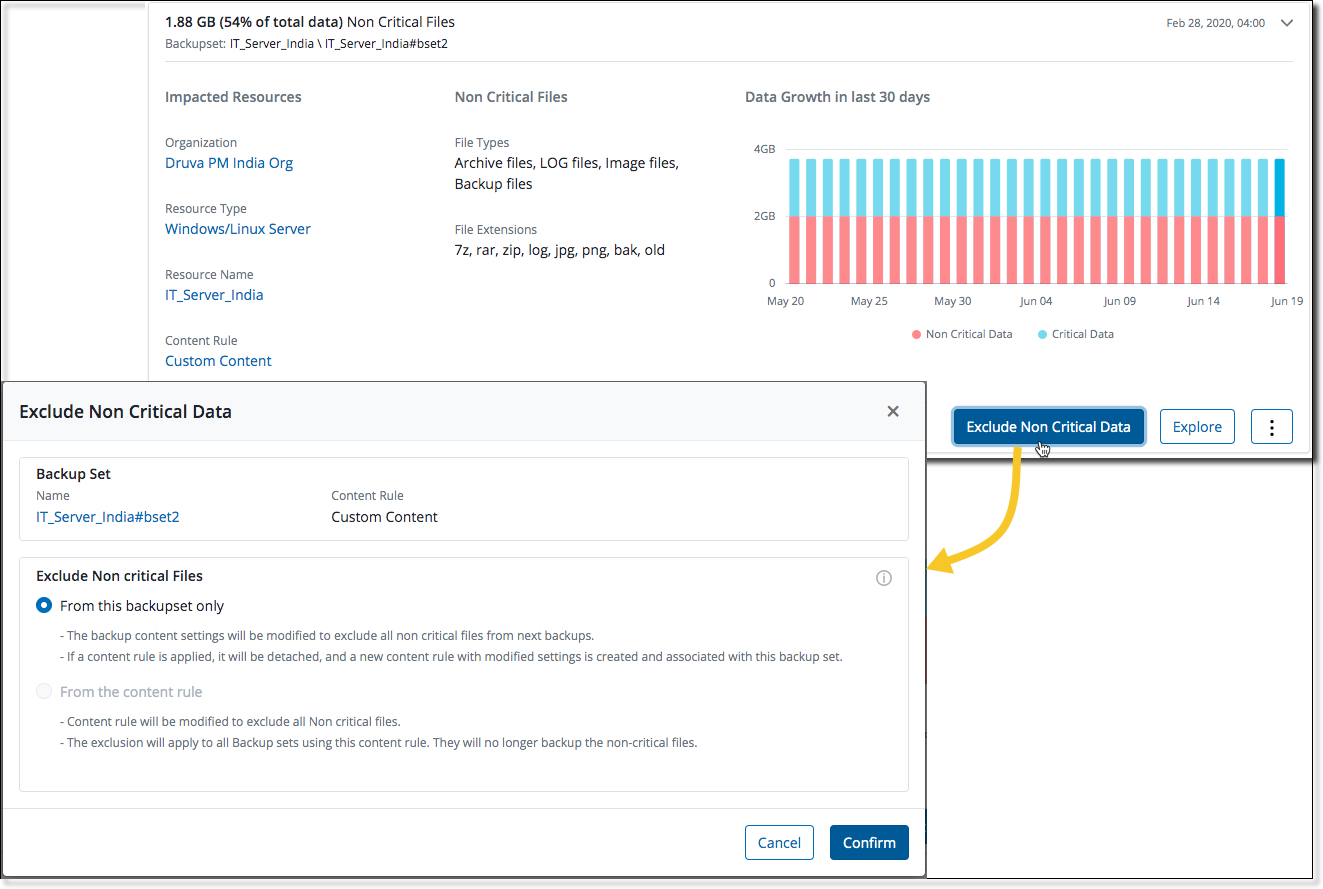
After update, non-critical file types are excluded from backup starting the next backup cycle.
For more information, see About Recommendations.
Cloud Upgrade on May 21, 2020
New Feature
File Analytics - Option to export File Analytics view as a PDF file
Administrators can now export their File Analytics view to a PDF file. This feature helps administrators print their view or share it with other administrators for collaboration purpose.
UI Enhancements
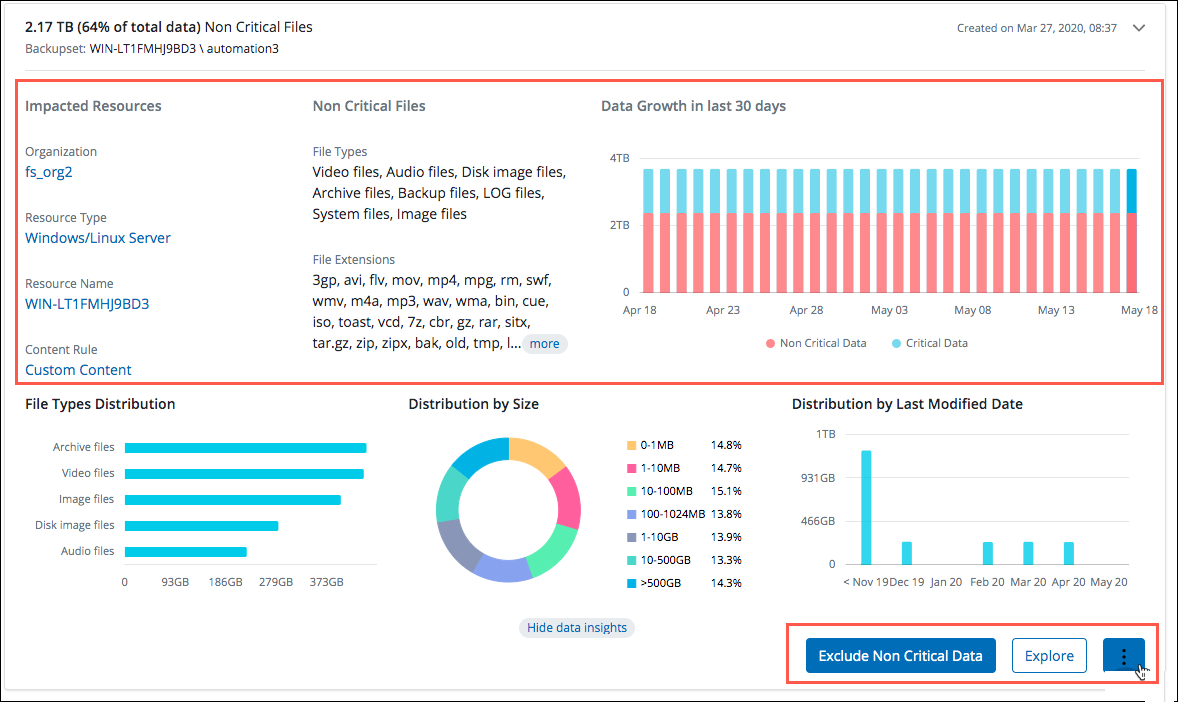
Recommendations
Based on customer interaction with Recommendations, we have updated to make it more intuitive and clear layout to display non-critical data information and enable you to actions. See Recommendations.
Cloud Upgrade on April 23, 2020
New Feature
Introducing Audit Trails - Log and monitor activities performed by administrators
Audit Trails captures the activities performed by the administrators in the Realize Managemen

