Failing over in a VPC with no internet connectivity
Enterprise Workloads Editions
❌ Business| ✅ Enterprise (Purchase Separately) | ✅ Elite
Overview
Consider a scenario where your AWS account has two VPCs. The first VPC has the Druva AWS proxy. This VPC has access to the Amazon services via the AWS PrivateLink. The second VPC does not have access to the internet. You want to failover the VMs to this second VPC which is our destination VPC. The following article describes how to failover VMs in the second VPC with no internet connectivity and a private subnet.
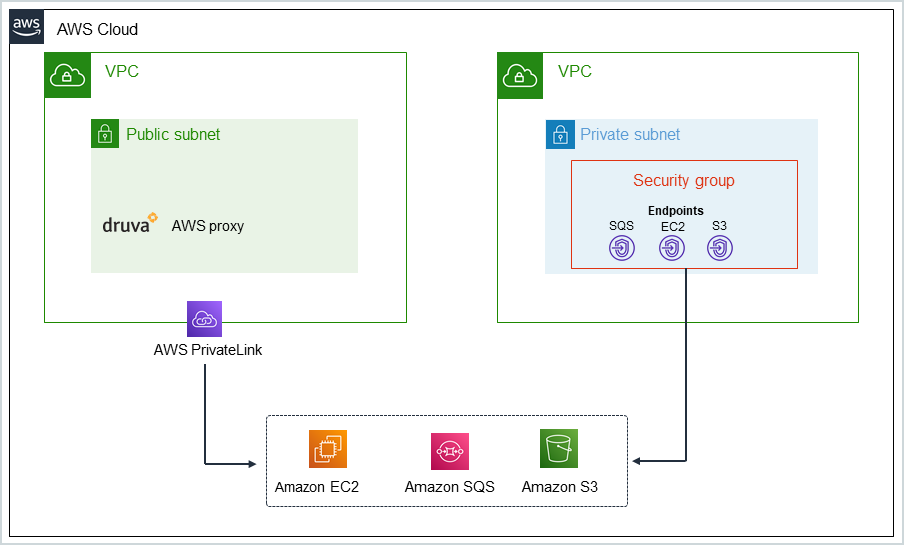
For failovers, Disaster Recovery needs the destination VPC to have access to three Amazon services - Amazon EC2, Amazon SQS, and Amazon S3. The destination VPC can access these services if the subnet in the destination VPC has an Internet Gateway (IGW). If the subnet in the destination VPC does not have an Internet Gateway (IGW) and is a private VPC, Druva needs to create VPC endpoints to access these services.
Determine if the subnet has an Internet Gateway (IGW)
- Login to AWS Management Console.
- Search for and go to the VPC service.
- In the left pane, under Virtual Private Cloud, click Subnets.
- From the list of subnets, select the subnet that you want to use for the failover.
- With the subnet selected, click the Route table tab in the pane below Subnets.
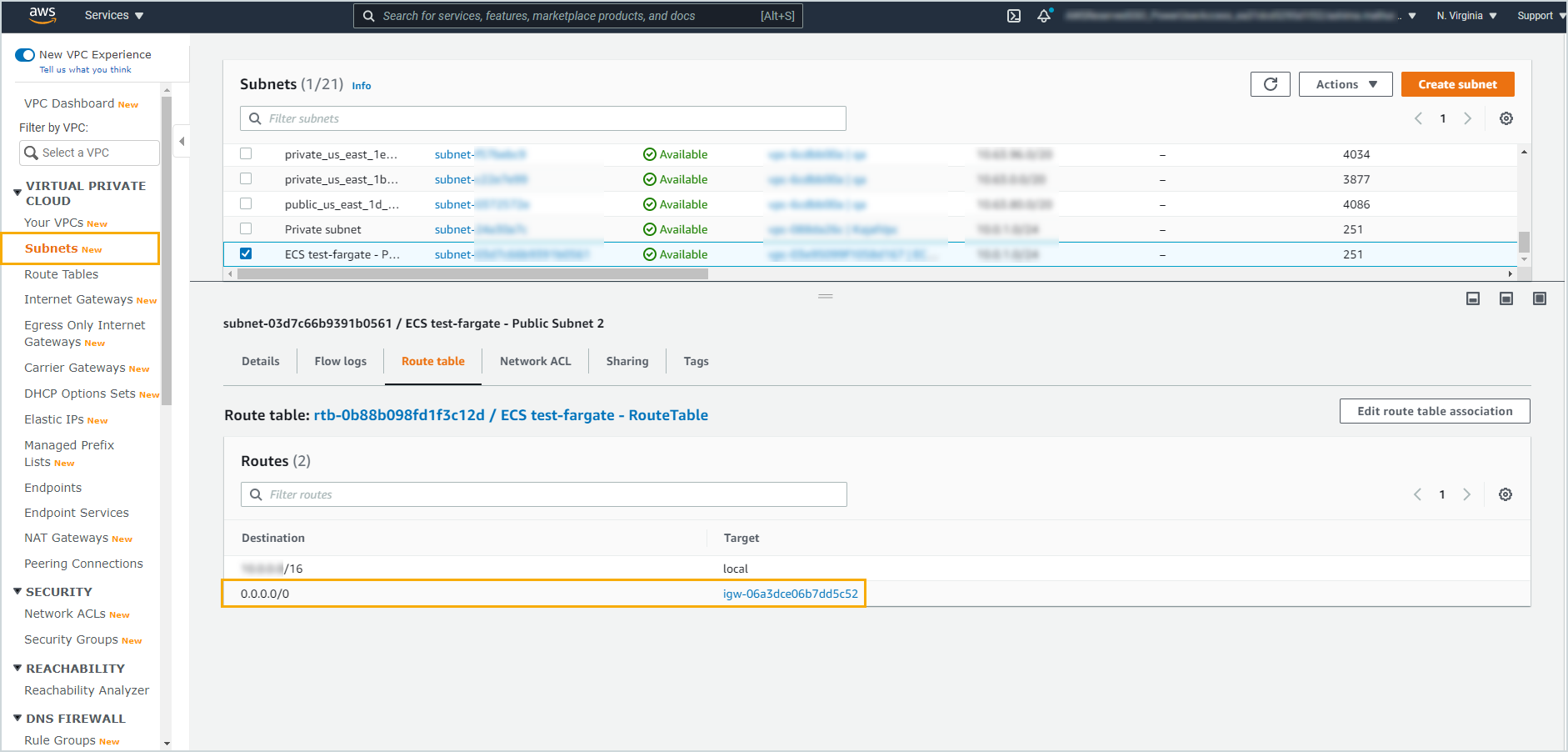
If the Route table has 0.0.0.0/0 under Destination and igw-<ID> in the Target column, then the selected subnet has an attached Internet Gateway (IGW). Since it has an IGW, it can connect to the three Amazon services (EC2, SQS, and S3). If the Route table does not have this entry, then it is a private subnet with no IGW.
Create VPC endpoints in a private subnet without an IGW
If the destination VPC does not have internet access, then we need to create VPC endpoints so that the failover instance can access the three AWS services.
Delete these endpoints once the failover is successful since the VPC endpoints are chargeable.
Prerequisite
Before creating VPC endpoints in the destination VPC, ensure that support for DNS hostnames and DNS resolution is Enabled.
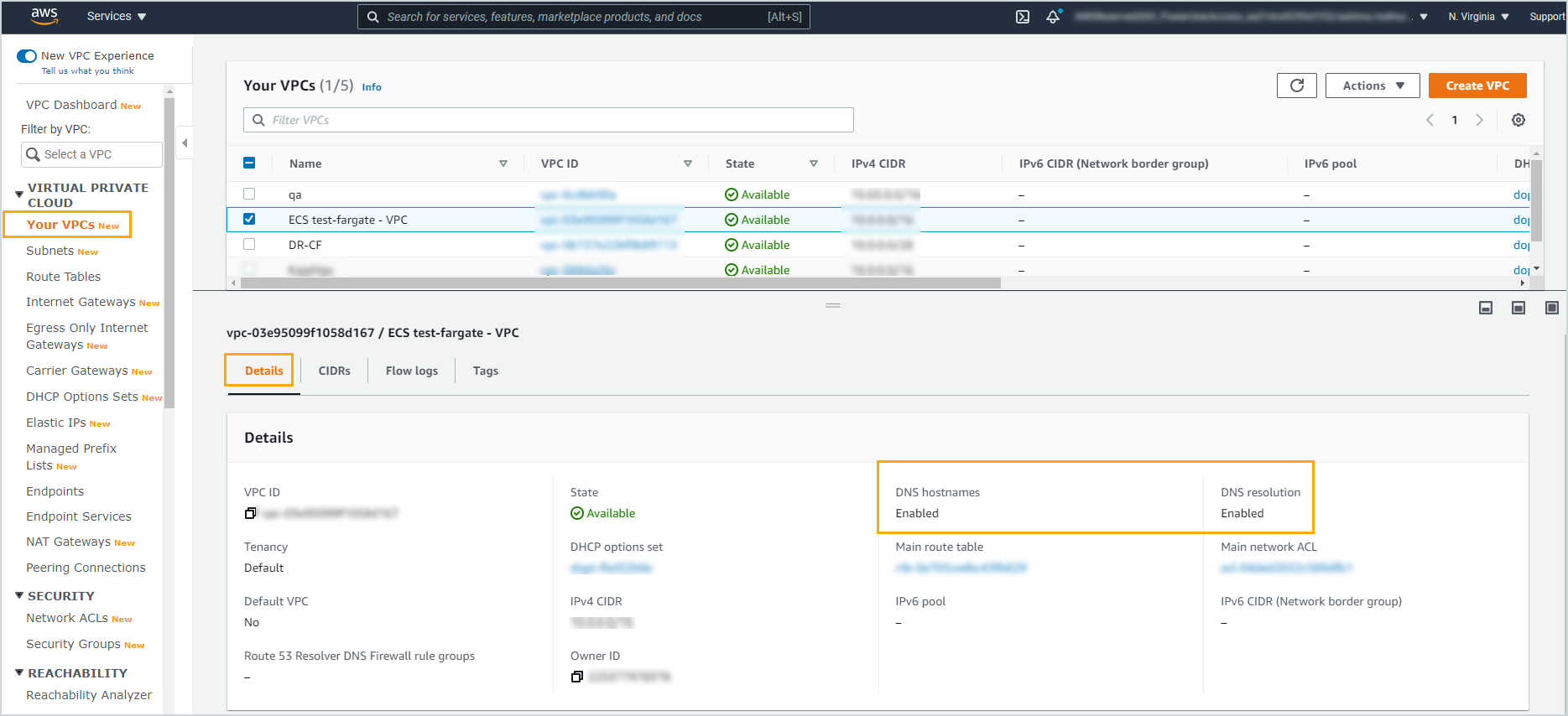
Creating endpoints involves four steps:
Step 1: Create a security group
- Login to AWS Management Console.
- Search for and go to the EC2 service.
- In the EC2 Dashboard, click Security Groups under Network & Security.
- In the Security Groups page, click Create security group on the right. Enter the following details:
- Basic details
- Security group name: Enter a name for the security group.
- Description: Enter a description that will help identify the security group.
- VPC: Select the failover VPC in which you want to create this security group.
- Inbound rules
- Click Add Rule, and then enter:
- Type: HTTPS
- Protocol: TCP
- Port range: 443
- Source: Custom 0.0.0.0/0
- Add a Tag if required.
- Click Add Rule, and then enter:
- Basic details
-
Click Create security group.
Step 2: Create an SQS endpoint
- Login to AWS Management Console.
- Search for and go to the VPC service.
- In the left pane, under Virtual Private Cloud, click Endpoints.
- In the right pane, click Create Endpoint.
- In the Create Endpoint dialog box, perform the following tasks:
- In the Service category field ensure that AWS services are selected.
- In the Service Name field, in the search bar, type sqs and press enter. From the search results, select com.amazonaws.us-east-1.sqs
- In the VPC dropdown, select the VPC where you will be failing over.
- Select the subnets.
- Ensure that Enable DNS name is enabled for the endpoint.
- Select the Security group that you created in Step 1 above.
- In the Policy field, retain the default setting of Full Access.
-
Click Create endpoint.
Step 3: Create an EC2 endpoint
- Login to AWS Management Console.
- Search for and go to the VPC service.
- In the left pane, under Virtual Private Cloud, click Endpoints.
- In the right pane, click Create Endpoint.
- In the Create Endpoint dialog box, perform the following tasks:
- In the Service category field ensure that AWS services are selected.
- In the Service Name field, in the search bar, type ec2 and press enter. From the search results, select com.amazonaws.us-east-1.ec2.
- In the VPC dropdown, select the VPC where you will be failing over.
- Select the subnets.
- Ensure that Enable DNS name is enabled for the endpoint.
- Select the Security group that you created in Step 1 above.
- In the Policy field, retain the default setting of Full Access.
- Click Create endpoint.
Step 4: Create an S3 endpoint
- Login to AWS Management Console.
- Search for and go to the VPC service.
- In the left pane, under Virtual Private Cloud, click Endpoints.
- In the right pane, click Create Endpoint.
- In the Create Endpoint dialog box, perform the following tasks:
- In the Service category field ensure that AWS services are selected.
- In the Service Name field, in the search bar, type s3 and press enter. From the search results, select com.amazonaws.us-east-1.s3 where the Type is Gateway.
- In the VPC dropdown, select the VPC where you will be failing over.
- In the Configure route tables section, select the same route table that was associated with the subnet.
- In the Policy field, retain the default setting of Full Access.
- Click Create endpoint.
Once the S3 endpoint is created, select the endpoint, and in the Route Tables tab in the pane below, click Manage Route Tables. Add a route with destination pl-63a5400a and target Gateway LoadBalancer endpoint.
Note: The destination pl-63a5400a is region specific and applies to the us-east-1 region.

