Package Signature Verification and Binary Signature Verification
Package signature verification ensures the integrity and authenticity of Linux binaries. The verification process protects you from maliciously modified or altered packages.
Druva allows protection in two ways:
-
You can verify the integrity of a download package.
-
You can also enable run-time binary signature verification.
The first step helps you confirm a downloaded package's integrity even before installing it. The second step ensures that the system does not execute an altered binary.
Package signature verification
Druva signs Linux packages with a private key. To verify the integrity of these packages, you can use the public key available here.
NOTE: Package signature verification is optional but recommended.
To verify the package signature, you can use GNU Privacy Guard (GPG), a free software implementation of the OpenPGP standard for data encryption and signing.
Druva packages are signed with a GPG key with the following fingerprint:
5484 5406 BCB6 BB5E 9BD7 B5D2 4DB5 6527 A03A F36D
Workflow for package signature verification
Following are the steps involved in verifying a package signature:
-
Import Druva's public key to your local GPG keyring.
-
Verify the signature of the package.
-
Proceed with installation if the signature is valid.
The exact commands would vary depending on your Linux distribution.
Prerequisites
You need the gpg utility, which most Linux distributions bundle.
Validate .deb package signure
You can validate .deb package signature with the following commands:
-
Install the Debian Package Archive Signature Verification(dpkg-sig) tool as follows:
apt-get install dpkg-sig
-
Import Druva's GPG public key to the local GPG keyring:
gpg --import gpg-sign-pub-key.pub
-
Verify the signature:
dpkg-sig -c Druva-package-name.deb
If the verification is successful, you will see the following message:
GOODSIG _gpgorigin
Validate .rpm package signature
You can validate .rpm package signature with the following commands:
-
Install the RPM Package Manager, if required, as follows:
apt-get install rpm
-
Import Druva’s GPG public key to the local GPG keyring:
rpm --import gpg-sign-pub-key.pub
-
Verify the signature:
rpm --checksig Druva-package-name.rpm
If the verification is successful, you will see the following message:
digests signatures OK
Binary signature verification
During the installation, you can enable runtime signatures verification. It ensures that if the binaries are altered at any time, these will not execute.
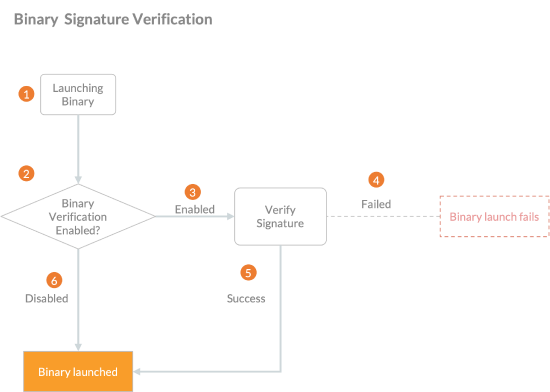
Workflow for binary signature verification
-
Attempt to launch a signed binary
-
Check if binary verification is enabled
-
If binary verification is enabled, verify the signature
-
If the signature verification fails, do not launch the binary.
-
If the signature verification is successful, launch the binary.
-
If the binary verification is disabled, skip verification and launch the binary.
Enabling binary signature verification during installation
When you install a package, you will see the following message:
Do you want to enable signature verification for Druva-EnterpriseWorkloads?
If yes, The public key will be added to your machine
Please enter input in option [yes/no][default: no]
Upon typing yes, the installer will add Druva’s public key to your local GPG keyring.
Every time you run the binary, it will verify the signature and run only if it is successful.
If you use scripts for installation
If you are installing packages from a script, you will need to set the EnterpriseWorkloads_SIGNATURE_VERIFICATION_FLAG environment variable before you run the script.
export EnterpriseWorkloads_SIGNATURE_VERIFICATION_FLAG=TRUE
Similarly, you can set the variable to FALSE to disable binary signature verification:
export EnterpriseWorkloads_SIGNATURE_VERIFICATION_FLAG=FALSE
Enabling or disabling binary verification after installation
If you did not enable binary verification at the time of the installation, you could do that even after the installation.
-
Locate the following file:
/etc/Druva/EnterpriseWorkloads/.sigConfig
Edit the file with any text editor and set the value to either true or false:
-
If this file contains true, the binary signature verification will be enabled.
-
If this file contains false, the binary signature verification will be disabled.
-
If Druva's public key is not already there in your local GPG keyring, download it from the Downloads page. After downloading, import the signature with the following command:
gpg --import gpg-sign-pub-key.pub
-
For this change to take effect, you will need to restart the Druva-EnterpriseWorkloads service.
Handling Warnings
If the binary signature verification is enabled, you may see the following warning in the Druva-EnterpriseWorkloads service status:
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
There is no impact of this warning on the functionality of binary signature verification.
To remove this warning, you can inform GPG to trust the certificate as follows:
- Execute the following command:
gpg --expert --edit-key security@druva.com trust - Select the option that says I trust ultimately. Usually, it means selecting option 5, but it may vary based on the version of the gpg utility. Select the option to Confirm and then quit the gpg utility.
- Restart Druva-EnterpriseWorkloads service.

