Support matrix
Before you set up Druva, you must ensure that the virtual machines or the servers that you plan to use, meet the system requirements.
This article gives you information about:
- Browser support
- Software requirements
- Hardware requirements
- Network requirements
- Security considerations
- Supported storage regions of Druva
- Support matrix for Azure virtual machines
Browser support
The following table lists the supported browsers for accessing the Management Console.
| Browser | Minimum requirements |
|---|---|
|
Web browser |
|
Software requirements
The following sections provide the software requirements for Druva to back up data residing on servers.
Software requirements for files and folders
Software requirements for Hyper-V
Software requirements for MS-SQL server
Certified platforms
Prerequisites
Software requirements for NAS devices
Permissions for NAS auto-discovery
Software requirements for NAS proxy
Software requirements for Oracle Druva Backup Store
Software requirements for Oracle Direct to Cloud
Software requirements for VMware
Software requirements for Nutanix AHV
Software requirements for CloudCache
Software requirements for SAP HANA
Ports and communications protocols for SAP HANA
Hardware requirements
The Hybrid Workloads agent installer, VMware backup proxy appliance, Hyper-V FLR proxy appliance, Phoenix Backup Store package, and the CloudCache installer are available at http://downloads.druva.com/phoenix/.
You can also download the installer at the time of registering servers.
Prerequisites for Hybrid Workloads agent
This section contains the prerequisites for the Hybrid Workloads agent. This configuration is applicable for one backup or restore job at a time. Applies to:
- Hyper-V virtual machines
- Files on a server
- MS-SQL server
Hardware requirements for installing Hybrid Workloads agent
| Hardware | Minimum requirements |
|---|---|
|
CPU |
|
| RAM | 3 GB |
|
Free space |
|
Hardware requirements for Hyper-V FLR proxy
Before you deploy and activate the FLR proxy, ensure that following system requirements on the Hyper-V host are met for the proxy:
- Memory: 2 GB
- vCPUs: 2
This is a recommended configuration for two restore jobs. If you want to run multiple restore jobs, increase the memory and number of vCPUs.
Disks, partitions, and files supported for File Level Restore (FLR) on Hyper-V hosts
-
Item Certified Disk Types
- Thin
- Thick
Partition Tables
- MBR
- GPT (Linux)
Partition Types
- Primary
- Extended
- LDM (Only Simple and Spanned Volumes with MBR)
- LVM (Simple/Spanned/Mirror/Striped)
File Systems
- NTFS
- FAT
- FAT32
- Ext2/3/4
- XFS
File Type
- Regular Files
- Sparse Files
- Hidden Files
Hardware requirements for NAS shares
Hardware requirements for VMware
This table lists the minimum requirements for deploying a backup proxy that is available as a virtual appliance.
Backup proxy requirements
Backup proxy is available as a virtual appliance. Deploying backup proxy creates a virtual machine with the configuration that is listed in this table. Ensure that your VMware setup can assign resources to support this requirement.
- For more information, see Prerequisites to install the backup proxy.
-
Hardware requirements for the Druva Backup Store
Hardware requirements for CloudCacheHardware requirements for SAP HANA
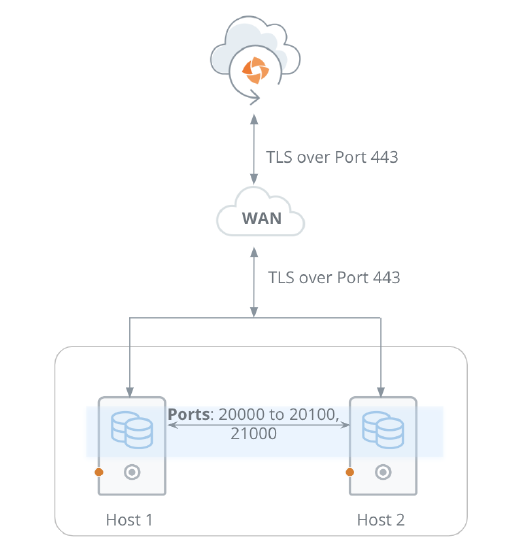
Network requirements
Field Requirement Network Traffic rules
Hybrid Workloads agent:
Hybrid Workloads agents connect to Druva Cloud using port 443.
CloudCache:
CloudCache connects to Druva Cloud using port 443.
Hybrid Workloads agents connect to CloudCache using port 443.
Druva Backup Store
Druva Backup Store connects to the Druva Cloud using port 443.
Firewall For all the agents and CloudCache: If the firewall is enabled, allow all outbound TCP/IP traffic to *.druva.com through port 443. Web proxy Druva supports the following proxy types:
- http
- socks4
- socks5
For more information see:
- For more information, see Sizing for backup proxy.
-
Security considerations
One thing that is often overlooked when deploying a data protection solution is security. While Druva automatically handles the security of information in transit and at rest, there are other security mechanisms that organizations should consider for implementing beyond encryption when it comes to data protection. The following sections discuss the security considerations that organizations should take into account as they implement Druva for their data protection solution.
Roles and responsibilities
To prevent privileged users from making unauthorized changes to resources within their organization, Druva supports the Role Based Access Control (RBAC) for separation of duties. This capability allows organizations to limit privileged user access to a predefined set of roles and data assets. This RBAC capability makes it possible to create ethical walls to enforce privacy, as well as implement a delegated administration structure to meet customers’ organizational, compliance, or security requirements. To add RBAC in your Druva deployment, see Manage administrators.
Global regulatory compliance
As part of your data protection strategy, organizations need to take into account where they operate and what requirements they have on security and availability of the data. With Druva , organizations can store data in any of twelve global regions depending on their security, compliance, data access, and availability requirements. While not only a compliance requirement, proximity to data can also help shrink the time it takes to recover in the event of a disaster.
Single Sign-On
Druva supports SAML which allows organizations to centralized authentication for the administration of their Druva environment. This allows administrators to leverage existing centralized authentication mechanisms like Okta, Ping Identity, or Active Directory which are already being used today. The use of Single Sign-On (SSO) helps to guarantee the availability of access to Druva and eliminates local authentication stores which cause audit and compliance headaches as well as create a security risk. To integrate Druva with your SSO authentication mechanism, see Configure single sign-on for Druva.
Testing your recovery
As part of your data protection strategy, it is important to see if what you are backing up is actually getting backed up, whether part of a normal business continuity and disaster recovery process.
Conclusion
While protecting data in flight and at rest are important security capabilities of any enterprise-level data protection solution, there are definitely more issues to take into account, and more capabilities to take advantage of when it comes to protecting the overall data attack surface. For identifying and implementing more such security considerations for Druva , contact Support.
Supported storage regions
The supported storage regions for Druva Cloud and Druva GovCloud are mentioned on the Cloud Status page of the Druva Support Portal.
You can hover over the relevant donut chart on the Cloud Status page or click VIEW DETAILS to see the information.
Support matrix for Azure virtual machines