Phoenix Windows Server activation fails with the error - Druva Phoenix Client service is not running
Problem description
After a successful installation or upgrade of the Phoenix agent on a Windows server, launching the Phoenix agent for activation causes the error Druva Phoenix Client service is not running.

The Phoenix agent service is running when seen from the Services console. However, the Phoenix.exe process is missing in the list of processes in the Windows Task Manager.

The log C:\ProgramData\Phoenix\PhoenixCPH.log shows the following error:
PATH =C:\Program Files\Druva\Phoenix Agent\Phoenix.exe
Error is: 0x800b010a.
CreateProcess failed as exe verification is failed
Navigate to C:\Program Files\Druva\Phoenix Agent\Phoenix.exe. Check the properties of phoenix.exe. On the Digital Signature tab, you will see the error Certificate signature cannot be verified.
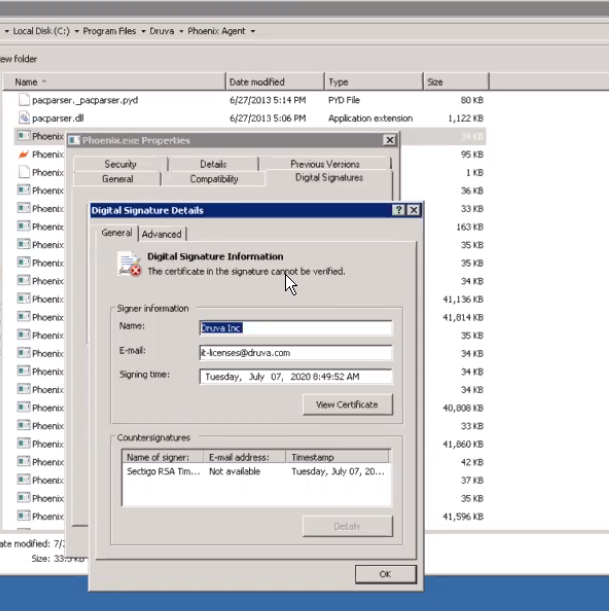
Cause
Certificates from the certificate chain are missing from the respective certificate store. A certificate chain is an ordered list of certificates, containing an SSL Certificate and Certificate Authority (CA) Certificates, that enables the receiver to verify that the sender and all CA's are trustworthy. If you click View Certificate, you will see the following chain: COMODO is a trusted root certificate authority. USER Trust RSA and Sectigo RSA are intermediate certificate authority. Druva Inc is a leaf certificate.
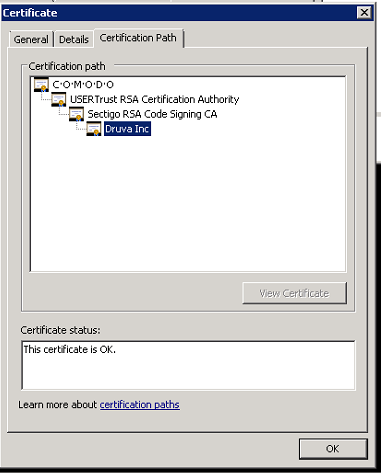
Trusted root and intermediate certificates must be present in respective certificate stores on the server for the leaf certificate to be verified. The following screenshots illustrate how the chain of certificates above authenticate one another: Root - Intermediate - Leaf hierarchy.
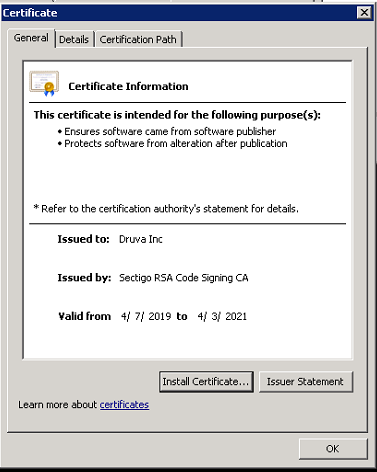
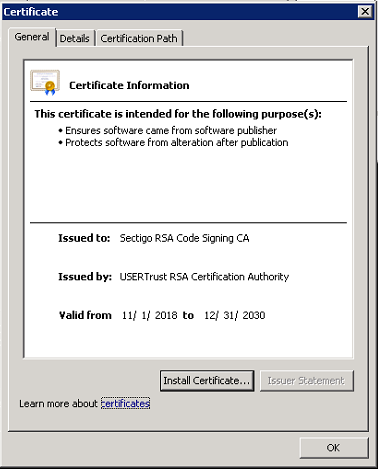
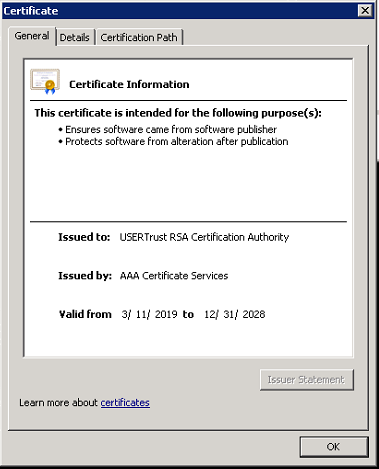
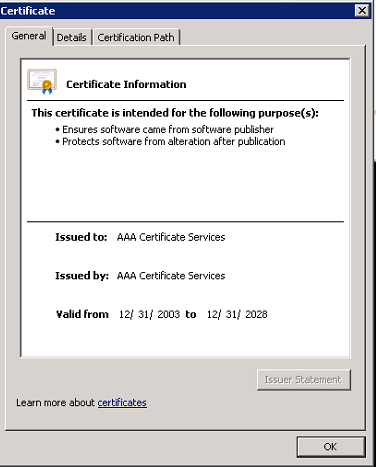
Resolution
If the certificates above are not present in the respective certificate stores, add them.
- Export the trusted root and intermediate certificates to any location on the server. To export the certificate, click Details on the certificate and select Copy to File...
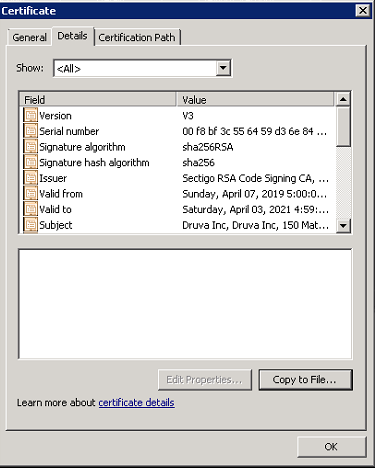
- Export in the DER encoded binary X.509 (.CER) format and save it to any location on the server.
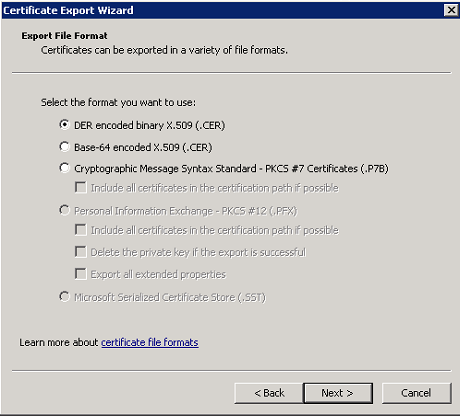
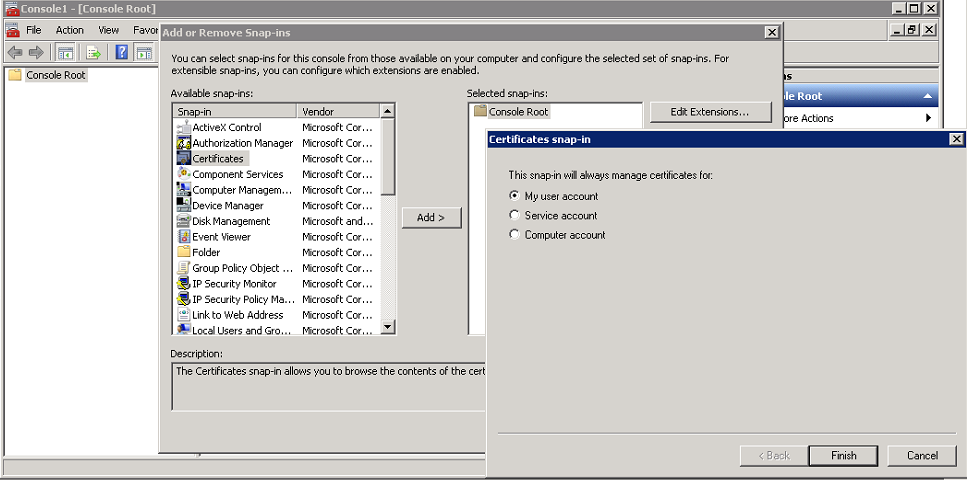
- Import the certificates into the certificate store. Launch an administrative command prompt, type mmc, and press Enter. Click File > Add/Remove Snap In...> Certificates > My user account.
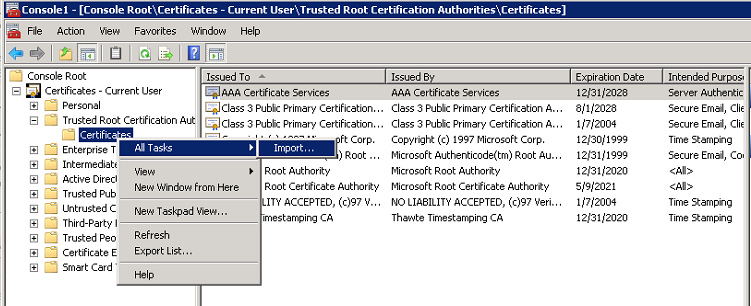
- Import the trusted root certificate (COMODO in this case) to the following store.
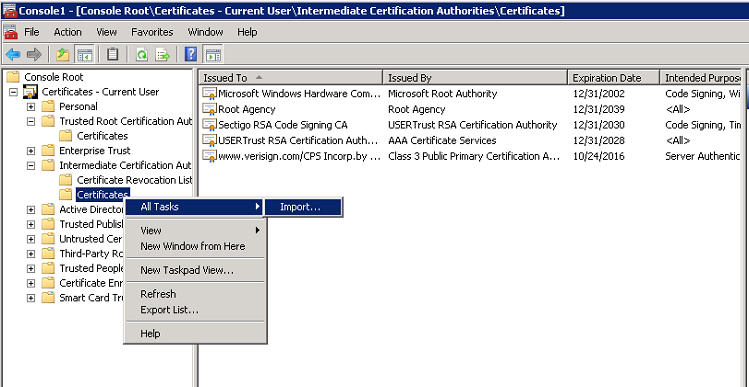
Similarly, import all the missing intermediate certificates (USERTrust and Sectigo in this case) to the following store.
-
Restart the Hybrid Workloads Agent Client Service. Phoenix.exe service should be running in the task manager now.

