How to configure SSO for DCP Administrators using PingFederate as IdP
This article applies to:
- Product edition: Druva Cloud Platform (DCP)
Overview
This article describes the steps to configure SSO for Druva Cloud Platform using PingFederate as IdP. The configuration involves the following main tasks:
- Only a Druva Cloud administrator can set up Single Sign-on.
- Configure Single Sign-on based on the applicable scenarios:
- New Druva customers that is; Phoenix customers on-boarded after 02 July 2018 and inSync customers on-boarded after 14 July 2018 must refer to the instructions given in this article.
- Existing Phoenix and inSync customers who already have configured Single Sign-on, must continue to use the existing Single Sign-on settings of Phoenix and the Single Sign-on settings of inSync as applicable.
Generate SSO Token from DCP Console
- Log in to the DCP Console and on its menu bar click the account icon > Settings.
- Click Generate SSO Token.
- Click Copy. The token gets copied to the clipboard.
- Copy the token in a text file and keep the file available for future use.
Configure the PingOne app
Prerequisites:
- Administrator credentials of PingOne
- SSO authentication token generated from the DCP Console.
Procedure:
- Log in to PingOne console with the administrator credentials (https://admin.pingone.com)
- From the dashboard, open the Applications page and click Add Application > New SAML Application.
- Enter the Application Name, Application Description, and Category as appropriate.
- Click Next and enter the values as specified below:
Assertion Consumer Service (ACS): https://login.druva.com/api/commonlogin/samlconsume
Entity ID: DCP-login - Leave default values in the remaining fields and click Continue to next step.
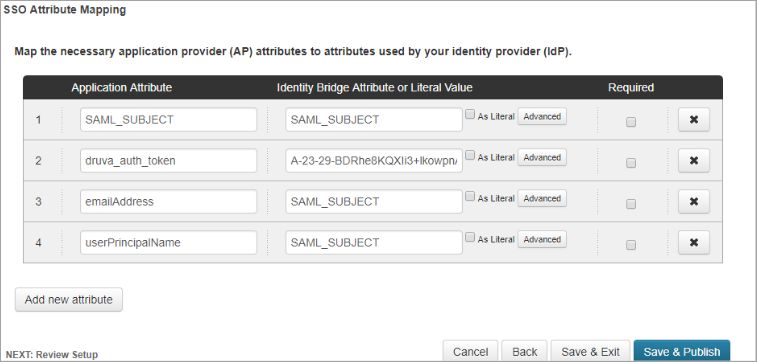
- Click Add new attribute and enter the values as shown in the illustration below:
Application Attribute Identity Bridge Attribute or Literal Value SAML_SUBJECT SAML_SUBJECT druva_auth_token Enter the SSO authentication token value and also select As Literal. If you do not wish to use As Literal, enclose the authentication token in double quotation ("") marks, such as "X-XXXXX-XXXX-S-A-M-P-L-E+TXOXKXEXNX=" email Address SAML_SUBJECT userPrincipalName SAML_SUBJECT
-
Click Save and Publish.
-
On the Review Setup page:
-
Copy IdP ID value from Initiate Single Sign-On (SSO) URL as shown in the in the image below.

-
Download the Signing Certificate.
Keep the above details available for future use.
Configure DCP to use PingOne
- Log in to the DCP Console and on its menu bar click the account icon > Settings.
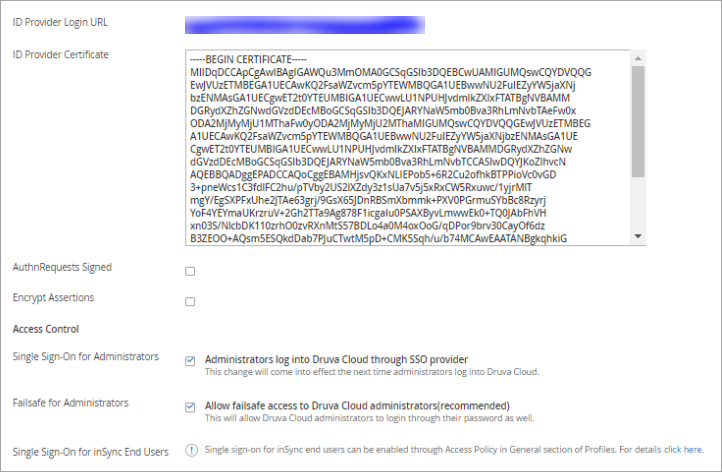
- Click Edit against Single Sign-On and update each field as directed in the table below:
ID Provider Login URL Append the IdP ID copied in the earlier procedure at the end of the below URL and copy the complete URL to this field. https://sso.connect.
pingidentity.com/sso/idp/SSO. saml2?idpid= ID Provider Certificate Open the Signing Certificate that was downloaded in the earlier procedure in a notepad and copy its content to this field. Take care to keep certificate formatting intact in the text editor. Single Sign-On for Administrators Select. Failsafe for Administrators Select.
Druva recommends enabling this fields initially. Failsafe for Administrators enables the administrator to use both SSO and DCP password to access the DCP Console. This ensures access to the DCP Console even if SSO is impacted due to any change in the IdP.
- Click Save.
On all subsequent attempts to log in to DCP Console, provide the administrator's email ID and DCP directs to the IdP page to authenticate using SSO.

