About inSync for MobileIron
Overview
The Druva Mobile App allows you access to your backup and share data from your mobile device anytime, anywhere. The Druva Mobile App also gives you complete security, control, and visibility of your data. For more information, see Use the Druva Mobile App on your iOS device.
As an administrator, you can quickly perform various configurations to install and monitor the inSync for MobileIron app on all iOS user devices. This allows you to have complete visibility of all iOS devices in your organization on which the inSync for MobileIron app is installed.
For information on the MobileIron ADMIN PORTAL, also called MobileIron Virtual Smartphone platform (VSP), see the MobileIron documentation.
Note:
- The MobileIron AppConnect app or MobileIron VSP server will never communicate with the inSync Server or any of its components, such as Edge Server or Storage Node directly. As shown in the figures below, the inSync MobileIron app and MobileIron AppConnect app on the mobile device will interact during the authentication and authorization workflow.
- inSync does not support MobileIron Sentry.
Workflow when the Druva Mobile App is launched for the first time
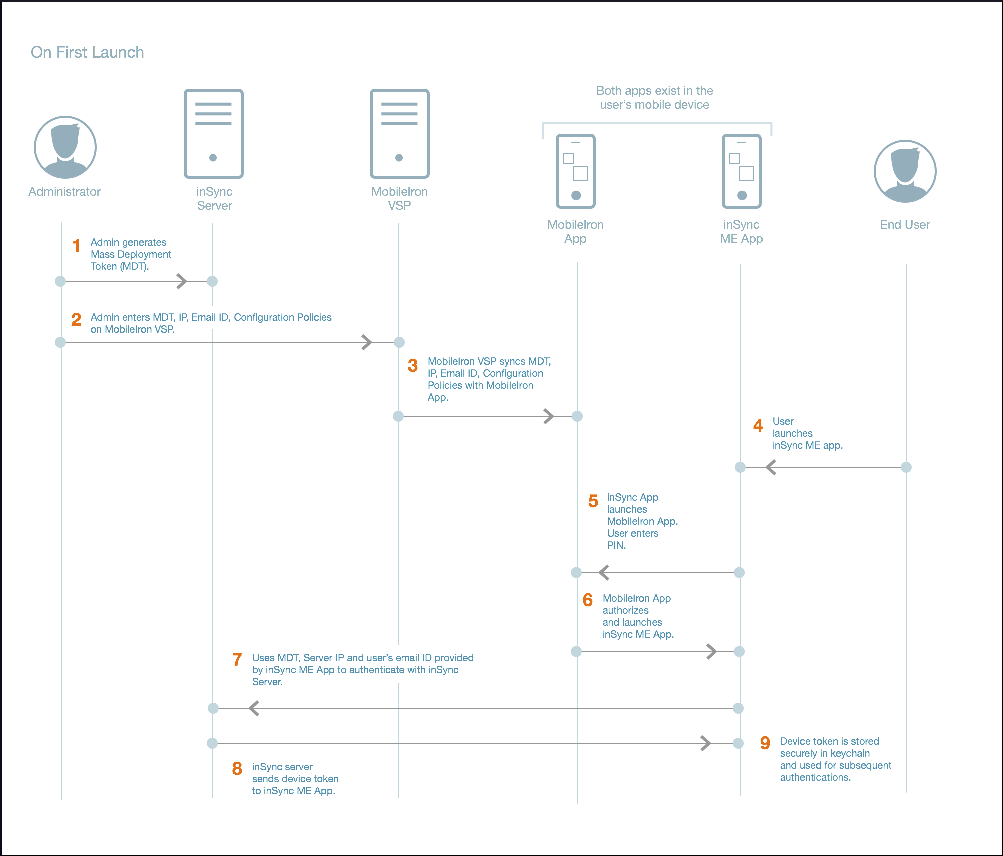
| Task no. | Task |
|---|---|
| 1. |
Administrator generates the mass deployment token from the inSync Management Console. The mass deployment token allows you to distribute and silently activate the inSync for MobileIron app on multiple iOS devices. For generating the mass deployment token, see generate a mass deployment token. |
| 2. |
Administrator executes the following tasks, and provides the information to MobileIron VSP :
|
| 3. |
MobileIron VSP syncs the the mass deployment token, IP address, user's email ID, and configuration policies with the MobileIron app. |
| 4. |
inSync user launches the Druva Mobile App on the mobile device. |
| 5. | Druva Mobile App launches the MobileIron app. insync user enters the MobileIron credentials on MobileIron app, with a PIN. |
| 6. |
MobileIron app authorizes and then launches the inSync for MobileIron app. |
| 7. |
MobileIron uses mass deployment token, Server IP, and user's email ID provided by inSync for MobileIron app to authenticate with inSync Server. |
| 8. | The inSync Server will send the device token to the inSync Client. |
| 9. | The device token is saved securely in the iOS's keychain and is used for subsequent authentication. |
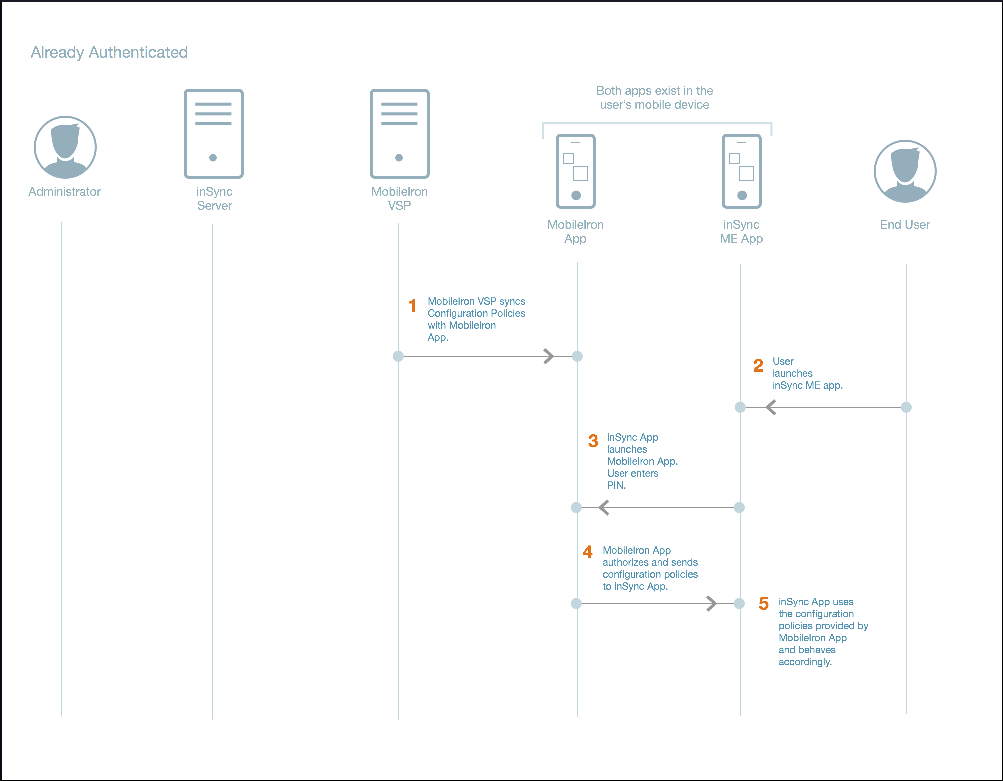
Workflow when the Druva Mobile App is already authenticated
| Task no. | Task |
| 1. | MobileIron VSP syncs the mass deployment token, IP address, user's email ID, and configuration policies with the MobileIron app. |
| 2. | inSync user launches the Druva Mobile App on the mobile device. |
| 3. | Druva Mobile App launches the MobileIron app. inSync user enters the MobileIron credentials on MobileIron app, with a PIN. |
| 4. | MobileIron app authorizes and sends the configuration policies to Druva Mobile App. |
| 5. | Druva Mobile App uses the configuration policies that are provided by the MobileIron app, and behaves accordingly. |
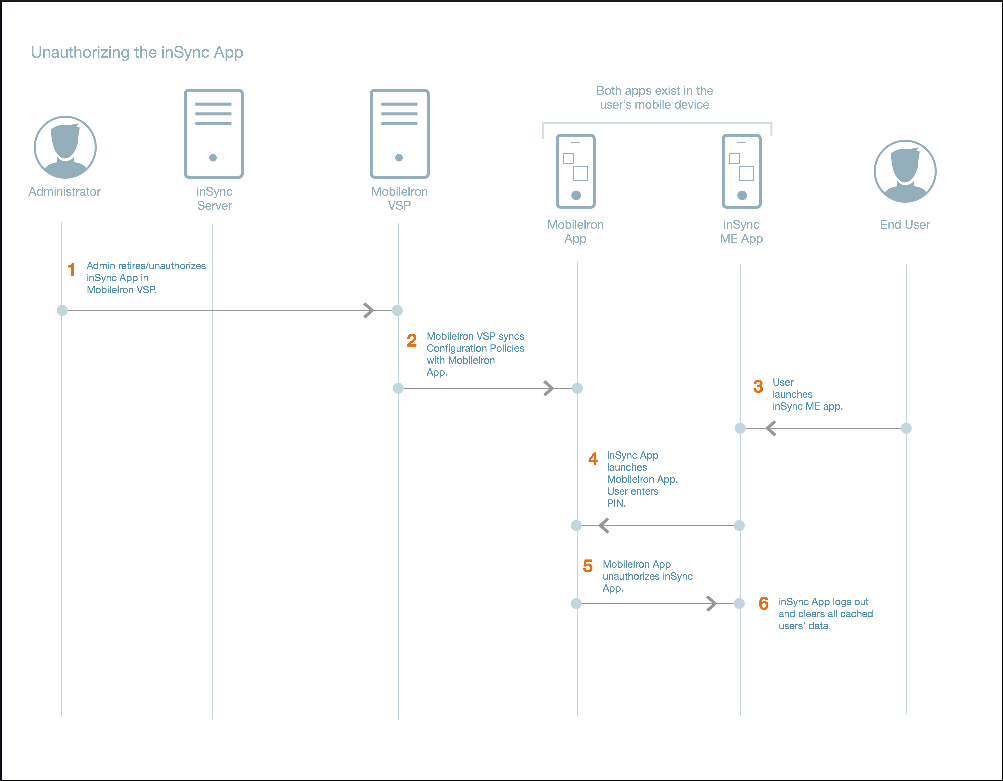
Workflow when the Druva Mobile App is unauthorized
| Task no. | Task |
|---|---|
| 1. |
On the MobileIron Server the administrator will retire or unauthorize the Druva Mobile App for a particular device. |
| 2. |
MobileIron VSP syncs the configuration policies with MobileIron app. |
| 3. | inSync user launches the inSync for MobileIron app. |
| 4. | Druva Mobile App launches the MobileIron app. inSync user enters the MobileIron credentials on MobileIron app, with a PIN. |
| 5. | MobileIron app unauthorizes the Druva Mobile App. |
| 6. |
Druva Mobile App logs out and clears the user's cache data. |
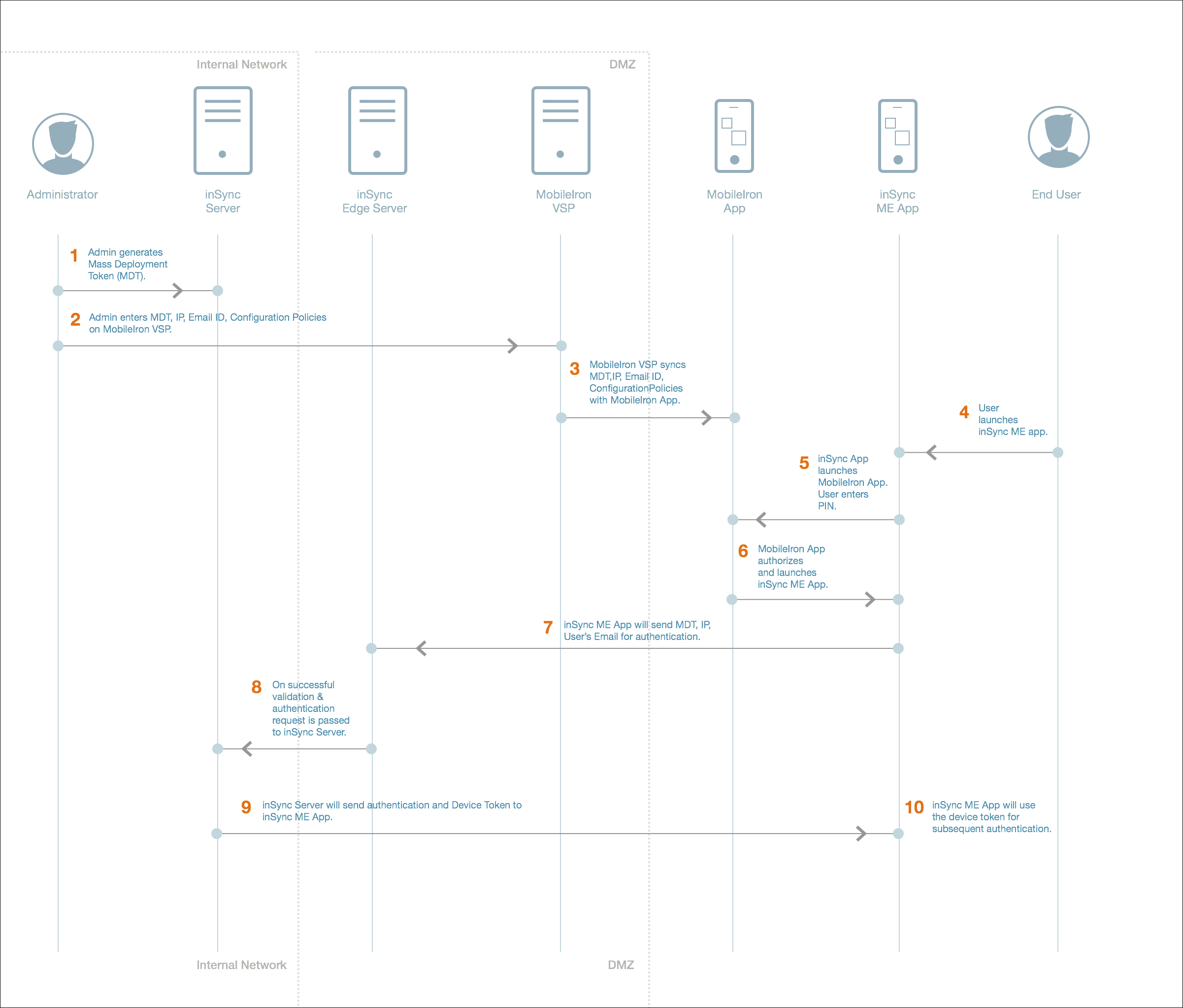
Workflow when the Druva Mobile App is launched for the first time in inSync On-Premises with Edge Server
|
Task no. |
Task |
|---|---|
| 1. |
Administrator generates the mass deployment token from the inSync Management Console. The mass deployment token allows you to distribute and silently activate the inSync for MobileIron app on multiple iOS devices. For generating the mass deployment token, see generate a mass deployment token. |
| 2. |
Administrator executes the following tasks, and provides the information to MobileIron VSP :
|
| 3. |
MobileIron VSP syncs the the mass deployment token, IP address, user's email ID, and configuration policies with the MobileIron app. |
| 4. |
inSync user launches the Druva Mobile App on the mobile device. |
| 5. | Druva Mobile App launches the MobileIron app. inSync user enters the MobileIron credentials on MobileIron app, with a PIN. |
| 6. |
MobileIron app authorizes and then launches the inSync for MobileIron app. |
| 7. |
MobileIron uses mass deployment token, Server IP, and user's email ID provided for MobileIron app to authenticate with inSync Server via the Edge Server. |
| 8. |
On successful authentication and validation, the request is forwarded to the inSync Server. inSync Client initiates a connection to the edge server and is authenticated with the inSync Server. |
| 9. |
inSync Server sends device token to inSync for MobileIron app via the Edge Server. |
| 10. | The device token is saved securely in the iOS's keychain and is used for subsequent authentication. |