Security Command Center
Overview
The Security Command Center is a centralized dashboard that allows Cloud Administrators to monitor the security posture of their backup environment easily and detect problems before they cause damage.
With the Security Command Center, you can receive a real-time security posture risk assessment and in-depth insights into the status and health of your backup environment. For example, administrators not using multi-factor authentication.
The Security Command Center provides a comprehensive view of the security status for the following:
It is designed to help Druva Cloud Administrators identify and mitigate potential security risks and to ensure that their data is protected and compliant with relevant security requirements.
Next Steps
Access Security Command Center
This section provides information on how to access Security Command Center.
Prerequisites
To access the Security Command Center, ensure that the following prerequisites are met:
- You have a valid Security Posture & Observability or Accelerated Ransomware Recovery license
- You must be a Druva Cloud Administrator
Access Path
On the Druva Cloud Platform Console, on the top-left corner of the page, click icon > Cyber Resilience > Security Command Center.
Know the Security Command Center Console
The Security Command Center displays the following risks:
-
Data-Centric Security Risks (Data Compliance risks)
Posture Security Risks
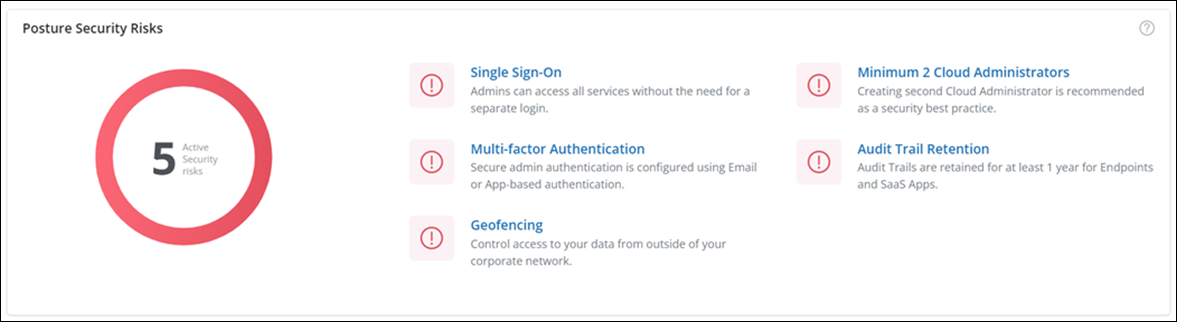
This card provides insights about the Cloud Platform and Data Governance security risks related to:
-
Druva account
-
Single Sign-On: Displays if the Single Sign-on authentication and authorization feature is enabled or disabled. For more information, see Single Sign-On.
-
Multifactor Authentication: Displays if the One Time Password (OTP) feature for administrator authorization is enabled or disabled. For more information, see Multifactor Authentication.
-
Geofencing: Displays if the Geofencing feature which restricts data access outside your organization's network is enabled or disabled. For more information, see Geofencing.
-
Minimum 2 Cloud Administrators: Displays if the second administrator is created or not. It is recommended to have a second administrator created as a best security practice. For more information, see Created at least 2 Druva Cloud Administrators.
-
-
Data Governance settings for Endpoints and SaaS Apps Data Sources
-
Audit Trail Retention: Displays this as a risk if the administrators' audit trail retention period needs to be set or is less than one year for Endpoints and SaaS Apps. For more information, see Audit Trail Retention Period.
-
The security risk for the Audit Trail retention Period is displayed only for administrators.
If these are not configured, an ![]() icon is displayed to notify the risk, and also the same is depicted on the pie graph with the count.
icon is displayed to notify the risk, and also the same is depicted on the pie graph with the count.
The icon indicates you have configured the setting to avert a security risk.
Data Protection Risks
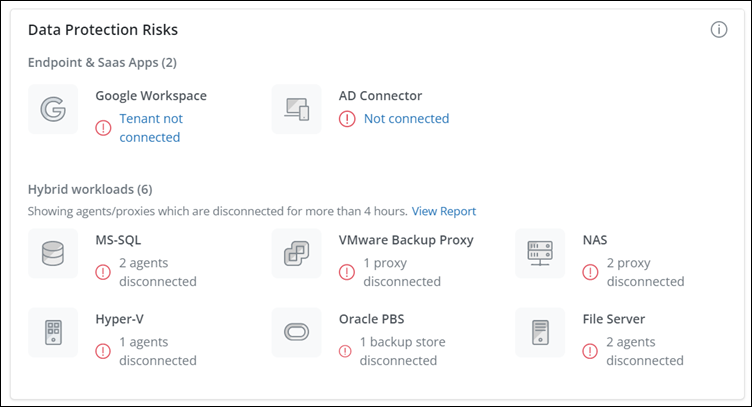
This card provides insights about the Data Sources' data protection security risks.
-
Endpoints and SaaS Apps data protection risks:
-
Microsoft 365 and Google Workspace apps are not in a connected state to authorize and allow Druva access data for backup.
-
AD Connector - Active Directory Connector is not connected to allow access to Directory Services in your organization. It may pose a risk for the following:
-
For Endpoints: New users import and management
-
For SaaS Apps: User's data backup, scheduled backups may fail in the absence of eKey not enabled.
-
-
-
Hybrid Workloads data protection risks:
-
Agent, Backup Store, and Proxy are in a disconnected state for Hybrid Workloads. Data cannot be backed up and protected.
-
| Workload Name | Entity Name - Disconnected |
|---|---|
| File Server |
Agent |
| MS-SQL |
Agent |
| NAS |
Proxy |
| Hyper-V |
Agent |
| VMware |
Proxy |
| Oracle PBS |
Backup Store |
| Oracle DTC |
Agent |
| CloudCache | Device |
You can use the View Reports option to get details about the Agent, Proxy, and Backup Store in a disconnected state beyond 4 hours for further investigation.
Data-Centric Security Risks
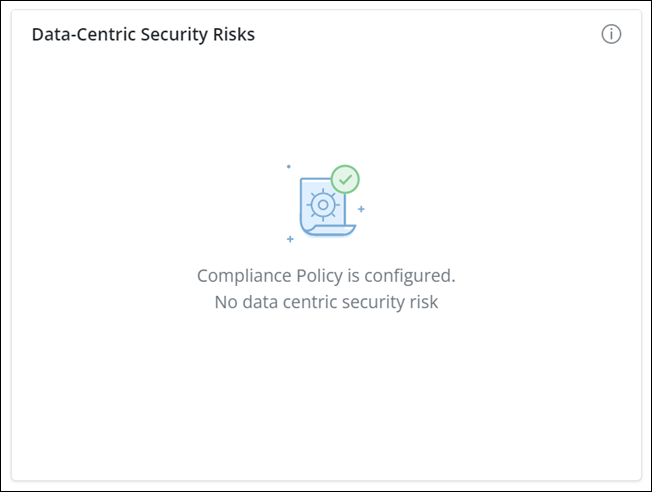
This card provides insights into your organization's data compliance risks using Sensitive Data Governance (Compliance). Sensitive Data Governance, once enabled, provides the ability to define sensitive data and scan user data for compliance violations or risks of violations.
Data Access Risks
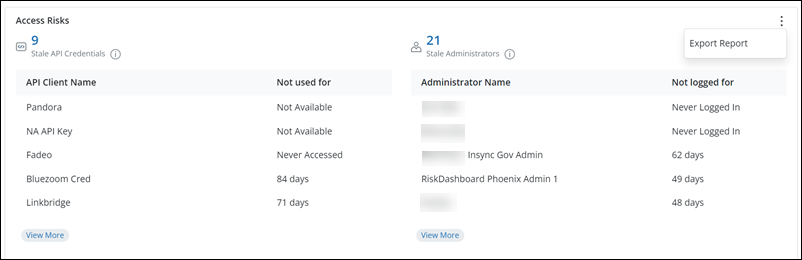
This card provides insights about the API credentials and administrator accounts that have not been accessed for a considerable period.
-
Admin login events: Details of the administrator login status.
-
Never Logged in: The administrator has not logged in even once to the Druva Cloud Platform Console
-
(Count) days: The count of days since when the administrator has not logged in to the Druva Cloud Platform Console
-
-
API access requests: Details of API access requests for each API Client Name.
-
Not Available: Data is not available for a particular API Client Name
-
Never Accessed: Any specific API Client Name has not accessed API even once.
-
(Count) days: The count of days since when the client has not accessed the API
-
The following table provides information about the Data Access Risks:
| Field | Description |
|---|---|
| Access risks for API | |
| Stale API Credentials | API credentials not used for the last seven days. |
| API Client Name | Name provided for the API credential for a client. |
| Not used for | Details of how long the API is not accessed by the client. |
| Access risks for administrators | |
| Stale Administrators | Administrators not logged into the Druva Cloud Platform Console for the last seven days. |
| Administrator Name | Name of the administrator not logged in to the Druva Cloud Platform Console |
| Not logged for | Administrators' login status. |
| Action | Description |
|---|---|
| Export Report | Use this to export the details of Data Access risks for further investigation. |
| View More | Use this to fetch and view more Data Access risks details. |
For more information, see,
Take action using the Security Command Center
Now that you know the Security Command Center, the next step is to analyze the security risks reported on the console and take corrective action.
The following table provides information about the remedial actions to be taken in case of security risk:
| Security Risk | Depicted by | Action Required |
|---|---|---|
| Posture Security Risk | Click on the risk to enable the required Cloud Platform and Data Governance configurations to resolve the risk. | |
| Data Protection Risks | Not Connected |
Click on the risk to enable, authorize, and complete the required configurations to resolve the risk. For Hybrid Workloads, if agents are in a disconnected state for more than 4 hours, use the View Report option to get more details for further investigation. You will have to get the Agent/Proxy/Backup Store connection restored in your Phoenix environment to resolve the risk. For more information, see,
|
| Data-Centric Security Risks | Compliance Policy is not configured |
Click Configure Policy link to configure the Compliance policy to scan user data for compliance violations or risks of violations. For more information, see Configure Policy. |
|
Data Access Risks |
|
You can verify and then delete the unused accounts to prevent unauthorized data access. For more information, see, |
Troubleshooting Security Command Center
Error: Information not available. Please try after some time
This error is displayed when the Druva services are down for maintenance or upgrade.

Resolution: You can retry once the services are available.
Related articles
- Data Protection Risks report - For Hybrid Workloads only

